Security Profiles
New security profiles features include:
- Menu and Options Simplification
- SSL Inspection
- Web Filtering
- Application Control
- Flow-based Antivirus
- Intrusion Protection System (IPS)
- Vulnerability Scanning Visibility
- Removed IM Proxy Options from CLI
- Client Reputation
Menu and Options Simplification
The menus and options for security profiles have changed in several ways. The basic profile/sensor/settings options have been left in the menu for each feature, while extra tables are now located in the Advanced menu. Other changes have been made for specific features.
AntiVirus
Several changes have been made for the configuration options in AntiVirus profiles, as visible options change depending on whether Inspection Mode is set to Flow-based or Proxy.
Flow-based Profile Options
If flow-based inspection is used for AntiVirus, you can configure whether to send files to FortiSandbox Cloud for inspection as well as the actions to be taken for detected viruses, and for connections to Botnet C&C servers. You can send suspicous files or all supported files to FortiSandbox cloud. Detect Viruses and connections to Botnet C&C Servers can be set to either Block or Monitor.
Flow-based options for AntiVirus
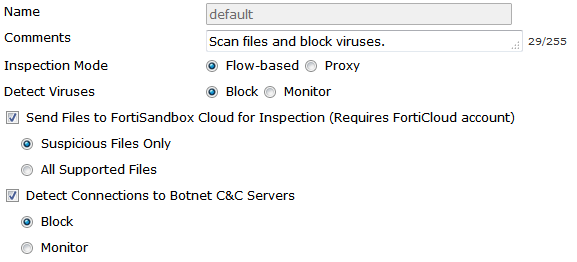
Proxy Options
If proxy inspection is used for AntiVirus, the addition Block or Monitor options are available for both detected viruses and Botnet C&C servers. The previous options for using FortiSandbox and protocol selection are also available.
Proxy options for AntiVirus
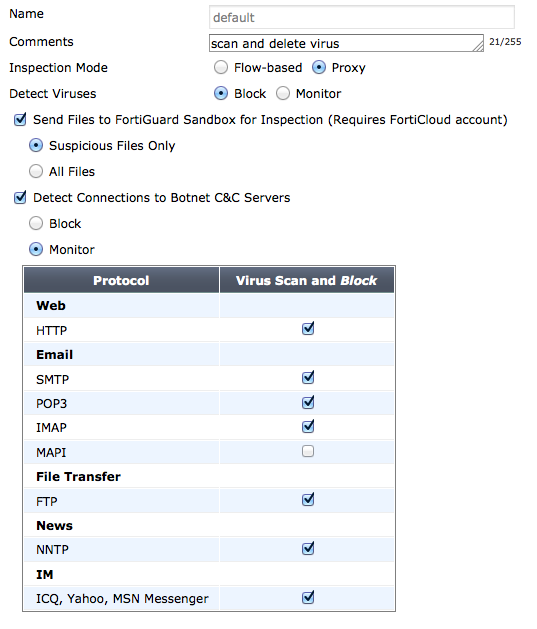
Web Filter
The web filter profile page has been expanded to contain settings for FortiGuard Categories, Search Engines, URL Filters, Ratings Options, and Proxy Options.
The web filter profile page
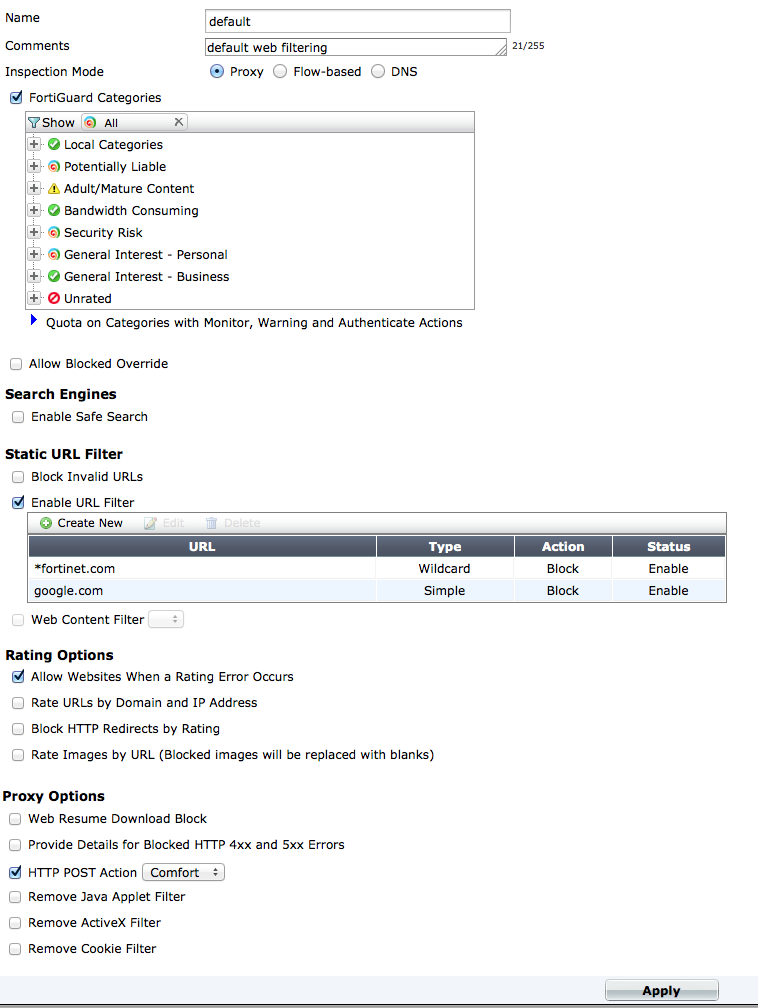
Intrusion Protection
The IPS sensor page now contains options for Pattern Based Signatures and Filters and Rate Based Signatures. The full list of IPS Signatures can be accessed from the sensor page by selecting View IPS Signatures.
The IPS sensor page
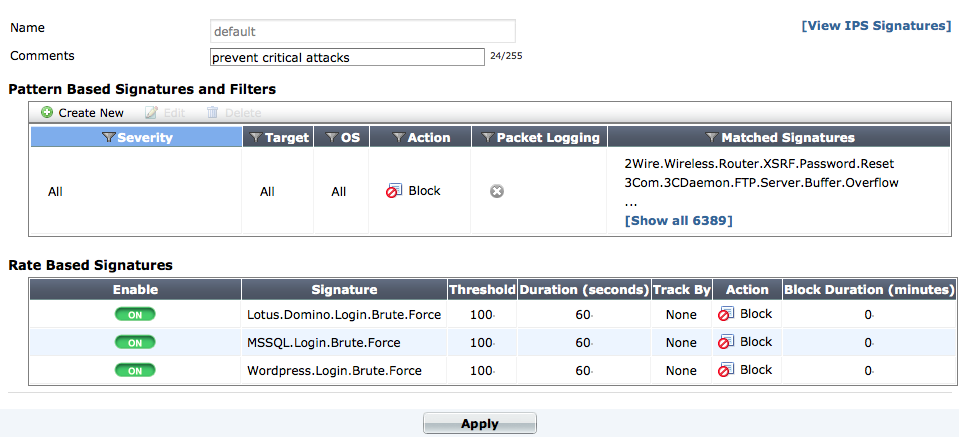
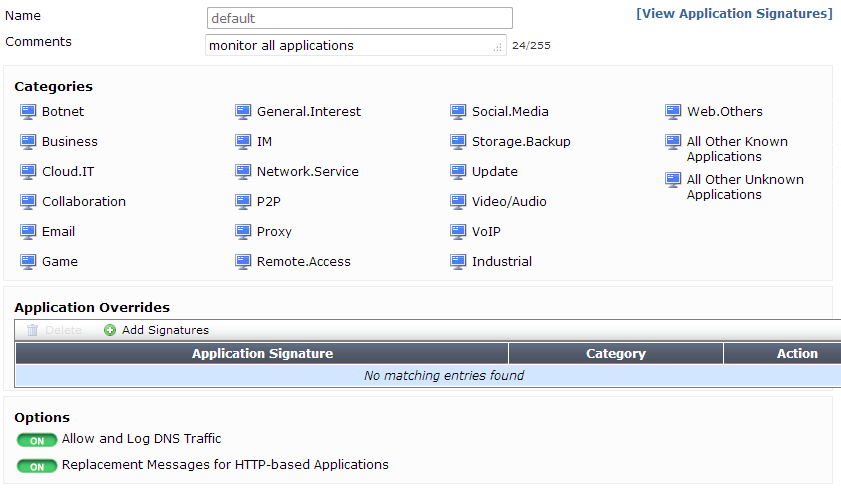
Application Control
The following changes have been made to improve usability in the web-based manager:
- A new category list has been made that appears on the sensor page, found by going to Security Profiles > Application Control. When you click on a category, a drop down menu appears, allowing the action for that category to be changed. You can also select to view all the application control signatures for that category.
- Application signatures can be viewed by selecting View Application Signatures.
- Application Overrides allow you to change the action taken for specific signatures/applications.
- The application filter sorting criteria popularity, technology, and risk have been removed.
The application control sensor page
Advanced Options
A new advanced menu has been added that contains the following features:
- Web rating overrides
- Web profile overrides
- DLP fingerprinting
Web Rating Overrides can also now be used to edit or delete custom website categories.
SSL Inspection
There have been several changes to how SSL Inspection is handled on a FortiGate unit.
Automatic Inspection When Security Profiles are Used
If any security profile is used in a security policy, SSL inspection will automatically be enabled, at which point an SSL mode must be selected (see below for more details).
HTTPS Scanning Without Deep Inspection
The following changes have been made in order to allow HTTPS traffic to be scanned without enabling deep inspection:
- There are now two modes for SSL inspection: certificate inspection (
certificate-inspectionin the CLI), which only inspects the SSL handshake, anddeep inspection (deep-inspectionin the CLI), which enables full deep inspection of SSL traffic (this was previously the default mode for SSL inspection). - The CLI command
https-url-scanhas been removed. deep-inspection-optionshas been renamedssl-ssh-profile.- The SSL
inspect-alloption and thehttps statusoption now have three states:disable,certificate-inspection, anddeep-inspection. The status option for the other protocols now usedeep-inspectioninstead ofenabled.
When a new policy or profile group is created, the SSL inspection profile certificate-inspection is automatically added.
SSL/Deep Inspection Exemptions
The options for configuring exemptions to SSL/Deep Inspection is now configured as part of the deep inspection options, rather than FortiGuard web filtering. Exemptions can be added to SSL inspection by going to Policy & Objects > Policy > SSL Inspection or through the CLI.
Certain applications, such as iTunes and Dropbox, require a specific certificate to be used, rather than using the use the system's certifciate store. Because of this, the default deep inspection profile, deep-inspection, has exemptions configured for these applications by default in FortiOS 5.2.
Syntax
config firewall ssl-ssh-profile
edit <name>
config ssl-exempt
edit <id>
set type {fortiguard-category | address | address6}
set category <id>
set address <string>
end
end
Generating Unique CA and Server Certificates
A FortiGate unit will now generate default SSL inspection CA and server certificates that are unique to that unit the first time the certificates are required. Previously, FortiGate units all have the same default CA and server certificates.
There are some exceptions: for example, in a HA cluster all FortiGate units need the same CA and server certificates. The certificates can also be changed as required for load balancing and other configurations.
Existing customers will not be affected by this change, as FortiOS 5.2 will not change the current defaults on upgrade.
You can use the CLI commands below to generate new certificates that will be unique to your FortiGate unit.
The following command re-generates the default SSL inspection CA certificate:
execute vpn certificate local generate default-ssl-ca
The following command re-generates the default SSL inspection server certificate:
execute vpn certificate local generate default-ssl-serv-key
Server Certificates
In FortiOS 5.2, two methods are available to support server certificates and allow inbound traffic to be inspected: Multiple Clients Connecting to Multiple Servers (re-sign in the CLI) or Protecting SSL Server (replace in the CLI).
The default setting for SSL Inspection is Multiple Clients Connecting to Multiple Servers.This setting can be changed by going to Policy & Objects > Policy > SSL Inspection or through the CLI.
Syntax
- Uploading a new server certificate:
config firewall ssl-ssh-profile
edit <name>
set server-cert-mode replace
set server-cert <certificate>
end
end
- Re-signing the server certificate:
config firewall ssl-ssh-profile
edit <name>
set server-cert-mode re-sign
set caname <name>
set certname <name>
end
end
Web Filtering
There have been several changes made to web filtering in FortiOS 5.2.
HTTPS for Warnings and Authentication
HTTPS protocol can now be used when sending web filtering warnings or requiring a user to authenticate, including authentication for web filter overrides.
Syntax
config webfilter fortiguard
set ovrd-auth-https enable
set warn-auth-https enable
end
Modifying HTTP Request Headers
In FortiOS 5.2, you can add, modify, and remove header fields in HTTP request when scanning web traffic in proxy-mode. If a header field exists when your FortiGate receives the request, its content will be modified based on the configurations in the URL filter.
Syntax
config web-proxy profile
edit <name>
config headers
edit <ID>
set name <name>
set content <string>
end
end
Restrict Google Access to Corporate Accounts
A new option has to web filtering to restrict Google access to specific domains. This allows you to block access to some Google accounts and services while allowing access to corporate Google accounts.
To use this option, go to Security Profiles > Web Filter and select Restrict Google Account Usage to Specific Domains under Proxy Options. You can then add the appropriate Google domains that will be allowed.
After the web filter profile has been created, this feature is applied differently in the case of transparent proxy vs. explicit proxy. For transparent proxy, the web filter profile is added to a security policy. For explicit proxy, the web filter profile must be added to an explicit proxy profile.
This feature can also be configured using the CLI, where use of the Modifying HTTP Request Headers feature (see above) is required. In the following example, access to Personal Gmail accounts is blocked while access to Google Business Mail is allowed.
Syntax
- The web-proxy profile is configured to with a modified header:
config web-proxy profile
edit "restrict-google-accounts-1"
config headers
edit 1
set name "X-GoogApps-Allowed-Domains"
set content "example.com"
end
end
- A URL filter is configured to use the web-proxy profile:
config webfilter urlfilter
edit 1
set name "GMAIL_TEST"
config entries
edit 1
set url "*.google.com"
set type wildcard
set action allow
set web-proxy-profile "restrict-google-accounts-1"
end
end
- A webfilter profile is configured that uses the URL filter:
config webfilter profile
edit "GMAIL_TEST"
......
config web
set urlfilter-table 1
end
config ftgd-wf
......
end
end
- Transparent proxy - the webfilter profile is applied to a security policy:
config firewall policy
edit 1
set srcintf "LAN"
set dstintf "WAN"
set srcaddr "all"
set dstaddr "all"
set action accept
set schedule "always"
set service "ALL"
set utm-status enable
set webfilter-profile "GMAIL_TEST"
set profile-protocol-options "default"
set ssl-ssh-profile "deep-inspection"
set nat enable
end
end
- Explicit proxy - the web-proxy policy and the web filer profile are applied to an explicit proxy policy:
config firewall explicit-proxy-policy
edit 1
set proxy web
set dstintf "WAN"
set srcaddr "all"
set dstaddr "all"
set service "webproxy"
set action accept
set schedule "always"
set webproxy-profile "restrict-google-accounts-1"
set utm-status enable
set webfilter-profile "GMAIL_TEST"
set profile-protocol-options "default"
set ssl-ssh-profile "deep-inspection"
end
end
Referer Added to URL Filtering
You can now add a referer to URL filters. If a referer is specified, the host name in the referer field of the HTTP require will be compared for any entry that contains the matching URL. If the referer matches, then the specified action will be performed by proxy.
The referer can also be set in the web-based manager, but only if advanced web filter features has been enabled using the following command:
config system global
set gui-webfilter-advanced enable
end
After this command is used, a new column will be created in Security Profiles > Web Filter > Static URL Filter to set the referer.
The command set referrer-host has been added to the CLI. The CLI has also changed so that URL filters are now identified by their IDs, and the URL values can be set under each entry.
Syntax
config webfilter urlfilter
edit <ID>
config entries
edit 1
set url <url>
set referrer-host <url>
set type {simple | regex | wildcard}
set action {block | allow | monitor | exempt}
set status {enable | disable}
end
end
FortiGuard Rating Checks for Images, JavaScript, CSS, and CRL
Web filter profiles that use FortiGuard rating checks can now be configured to rate images, JavaScript, CSS, and CRL.
Syntax
config webfilter profile
edit <name>
config ftgd-wf
set rate-javascript-urls enable
set rate-css-urls enable
set rate-crl-urls enable
set rate-image-urls enable
end
end
Additional Replacement Message Variables
Along with the variables for source IP (%%SOURCE_IP%%), destination IP (%%DEST_IP%%), and user name (%%USERNAME%%) that have been added for all replacement messages, the following variables can now be added to replacement messages for web filtering:
- Group name (%%GROUPNAME%%)
- Policy UUID (%%POLICY_UUID%%)
- FortiGate Hostname (%%FGT_HOSTNAME%%)
New Daemon for Overrides and Warnings
The new daemon ovrd is used in FortiOS 5.2 to handle user-level webfilter overrides and warnings.
Application Control
There have been several changes made to application control.
Deep Inspection for Cloud Applications
Deep inspection allows the following information to be examined and logged for cloud applications:
Information about user logins and file transfers for cloud applications.
Video names will be shown in the Application Details column for video streaming applications such as Youtube and Vimeo.
The following new fields have been added to both the application control log and to traffic logs: cloud user, cloud action, file name, and file size.
To enable this feature, turn on Deep Inspection of Cloud Applications in an application control profile. It can also be enabled using the CLI.
Syntax
config application list
edit <name>
set deep-app-inspection enable
end
end
Using the CLI, you can specify a global timeout for the deep application control database. Any database entries that exceed the timeout will be deleted. A global size threshold on the number of entries in the deep application control database can also be set.
When the total number of entries exceeds this threshold, the internal timeout value will be reduced to accelerate entry retiring. Both values are set to 0 (unlimited) by default.
Syntax
config ips global
set deep-app-insp-timeout <integer>
set deep-app-insp-db-limit <integer>
end
A new option, --deep_ctrl, has also been added to the syntax for IPS/application control signatures.
Several new CLI commands have also been added for diagnose and debugging:
diagnose ips dac infodiagnose ips dac cleardiagnose ips debug enable dac
Traffic Shaping Settings
Traffic shaping settings can be applied to categories of applications that are part of the application control sensor.
To apply settings, select a category and set it to Traffic Shaping. The Traffic Shaping Settings options will appear, allowing you to select the settings for forward and reverse traffic shaping. These settings will be applied to all categories set to Traffic Shaping in your application control sensor.
5-Point-Risk Rating
A new rating system will be used for all pages related to application control, including the application list, the application filters list, traffic logs, the FortiView Applications dashboard, and the FortiView All Sessions dashboard. Risk levels are indicated in the various tables and logs by using a series of icons.
The rating system is as follows:
| Icon | Risk Level | Description | Example |
|---|---|---|---|
|
|
Critical | Applications that are used to conceal activity to evade detection | Tor, SpyBoss |
|
|
High | Applications that can cause data leakage, or prone to vulnerabilities or downloading malware | Remote Desktop, File Sharing, P2P |
|
|
Medium | Applications that can be misused | VoiP, Instant Messaging, File Storage, WebEx, Gmail |
|
|
Elevated | Applications are used for personal communications or can lower productivity | Gaming, Facebook, Youtube |
|
|
Low | Business Related Applications or other harmless applications | Windows Updates |
Replacement Message
A replacement message has been added that will appear when an application has been blocked.
This replacement message can be enabled in the CLI.
Syntax
config application list
edit <name>
set app-replacemsg {enable | disable}
end
end
Support for SPDY Protocol
The SPDY protocol, and its required SSL/TLS component, is now recognized within application control profiles. It is counted as part of application traffic for Google and other sources that use the protocol.
Support for Non-HTTP WAN Optimization and Explicit Proxy Traffic
Application control is now supported for both non-HTTP WAN optimization traffic and explicit proxy traffic.
Flow-based Antivirus
In FortiOS 5.2, flow-based AntiVirus has been improved to have the same enhanced performance as flow-based antivirus scanning in FortiOS 5.0 while providing the same accuracy and many of the extended features of proxy-based antivirus.
Flow-based AntiVirus now allows data to accumulate until it detect the end of a file. When the end is reached, traffic is paused and data is sent asynchronously for analysis. When the results are received, the traffic is either allowed to resume or the connection is reset.
Because of this change, the default AntiVirus profile on a FortiGate uses flow-based inspection. Flow-based inspection can also utilize the extended AntiVirus database. Detecting and reporting only occurs when AntiVirus is enabled in the security policy.
Flow-based AntiVirus is also supported for sniffer policies.
Intrusion Protection System (IPS)
There have been several changes made to intrusion protection system (IPS).
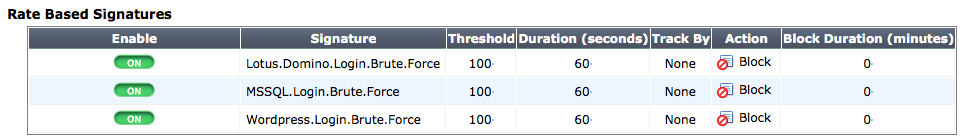
Adjusting Rate Based Signatures
Setting for rate based IPS signatures can now be edited in the web-based manager as part of an IPS sensor. In each sensor, you can enable a selected list of rate based signatures and adjust threshold, duration, track by setting, action, and block duration.
Rate Based Signatures list
Extensible Meta Data
Extensible meta data allow you to specify custom options in IPS signatures that are delivered to your FortiGate without interpretation, in order to make signatures easier to find and understand for the FortiGate administrator. Four types of meta data options are supported: integers, bitmaps, enumerables, and strings.
Example
In this example, a set of meta data is declared and then used to create IPS signatures.
The meta data is declared:
F-META2( --name points; --index 12; --type integer; )
F-META2( --name flags; --index 34; --type bitmap; --value foo:1; --value bar:2; --value baz:4; )
F-META2( --name dr_seuss; --index 56; --type enum; --value "One Fish":1; --value "Two Fish":2; --value "Red Fish":3; --value "Blue Fish":4; )
F-META2( --name secret; --index 78; --type string; )
The meta data is used:
F-SBID( --points 42; ... )
F-SBID( --flags foo; --flags baz; ... )
F-SBID( --dr_seuss "One Fish"; ... )
F-SBID( --secret "Abracadabra"; ... )
Extended Database
In FortiOS 5.2, the IPS extended database is enabled by default for all FortiGate models that have multiple CP8.
Support for Non-HTTP WAN Optimization and Explicit Proxy Traffic
IPS is now supported for both non-HTTP WAN optimization traffic and explicit proxy traffic.
Vulnerability Scanning Visibility
The options to configure vulnerability scanning either in the web-based manager or the CLI are also only available in NAT/Route mode.
Vulnerability scanning options in the web-based manager are now hidden by default. To enable vulnerability scanning, go to System > Config > Features, select Show More, turn on Vulnerability Scan, and select Apply.
Vulnerability scanning is also hidden by default for FortiClient profiles until being enabled in the CLI. To enable scanning, enter the following commands:
config endpoint-control profile
edit <profile-name>
config forticlient-winmac-settings
set forticlient-vuln-scan {enable | disable}
set forticlient-vuln-scan-schedule {daily | weekly | monthly}
set forticlient-vuln-scan-on-registration {enable | disable}
set forticlient-ui-options {av | wf | af | vpn | vs}
end
end
Removed IM Proxy Options from the CLI
The proxy options related to instant messaging (IM) functions and attributes have been removed from the CLI in FortiOS 5.2. This includes the following commands:
config imp2pget imp2p- The DLP sensor options for AIM, ICQ, MSN, and Yahoo protocols.
- The AntiVirus profile option
config im. - The AntiVirus quarantine options for IM.
- The Application Control profile options for IM.
- The firewall profile protocol options for IM.
Client Reputation
The 5.0 feature client reputation has been renamed Threat Weight in FortiOS 5.2 and has been moved from Security Profiles to Log & Report > Log Config > Threat Weight. It can now be configured in the CLI using the command config log threat-weight.

