The FortiGate explicit FTP proxy
You can use the FortiGate explicit FTP proxy to enable explicit FTP proxying on one or more FortiGate interfaces. The explicit web and FTP proxies can be operating at the same time on the same or on different FortiGate interfaces.
|
|
Explicit FTP proxies are configured for each VDOM when multiple VDOMs are enabled. |
In most cases you would configure the explicit FTP proxy for users on a network by enabling the explicit FTP proxy on the FortiGate interface connected to that network. Users on the network would connect to and authenticate with the explicit FTP proxy before connecting to an FTP server. In this case the IP address of the explicit FTP proxy is the IP address of the FortiGate interface on which the explicit FTP proxy is enabled.
|
|
Enabling the explicit FTP proxy on an interface connected to the Internet is a security risk because anyone on the Internet who finds the proxy could use it to hide their source address. |
If the FortiGate unit is operating in Transparent mode, users would configure their browsers to use a proxy server with the FortiGate unit management IP address.
The FTP proxy receives FTP sessions to be proxied at FortiGate interfaces with the explicit FTP proxy enabled. The FTP proxy uses FortiGate routing to route sessions through the FortiGate unit to a destination interface. Before a session leaves the exiting interface, the explicit FTP proxy changes the source addresses of the session packets to the IP address of the exiting interface. When the FortiGate unit is operating in Transparent mode the explicit web proxy changes the source addresses to the management IP address.
Example explicit FTP proxy topology
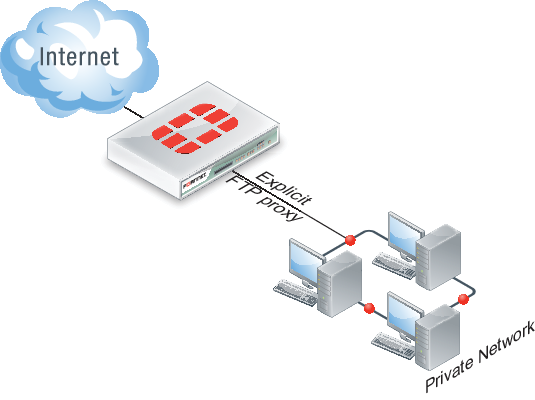
To allow anyone to anonymously log into explicit FTP proxy and connect to any FTP server you can set the explicit FTP proxy default firewall proxy action to accept. When you do this, users can log into the explicit FTP proxy with any username and password.
In most cases you would want to use explicit proxy policies to control explicit FTP proxy traffic and apply security features, access control/authentication, and logging. You can do this by keeping the default explicit FTP proxy firewall policy action to deny and then adding explicit FTP proxy policies. In most cases you would also want users to authenticate with the explicit FTP proxy. By default an anonymous FTP login is required. Usually you would add authentication to explicit FTP proxy policies. Users can then authenticate with the explicit FTP proxy according to users or user groups added to the policies. User groups added to explicit FTP proxy policies can use any authentication method supported by FortiOS including the local user database and RADIUS and other remote servers.
If you leave the default firewall policy action set to deny and add explicit FTP proxy policies, all connections to the explicit FTP proxy must match an or else they will be dropped. Sessions that are accepted are processed according to the ftp-proxy security policy settings.
You can also change the explicit FTP proxy default firewall policy action to accept and add explicit FTP proxy policies. If you do this, sessions that match explicit FTP proxy policies are processed according to the policy settings. Connections to the explicit FTP proxy that do not match an explicit FTP proxy policy are allowed and the users can authenticate with the proxy anonymously.
There are some limitations to the security features that can be applied to explicit FTP proxy sessions. See Security profiles, threat weight, device identification, and the explicit FTP proxy.
You cannot configure IPsec, SSL VPN, or Traffic shaping for explicit FTP proxy traffic. Explicit FTP proxy policies can only include firewall addresses not assigned to a FortiGate unit interface or with interface set to any. (On the web-based manager you must set the interface to Any. In the CLI you must unset the associated-interface.)
How to use the explicit FTP proxy to connect to an FTP server
To connect to an FTP server using the explicit FTP proxy, users must run an FTP client and connect to the IP address of a FortiGate interface on which the explicit FTP proxy is enabled. This connection attempt must use the configured explicit FTP proxy port number (default 21).
The explicit FTP proxy is not compatible with using a web browser as an FTP client. To use web browsers as FTP clients configure the explicit web proxy to accept FTP sessions.
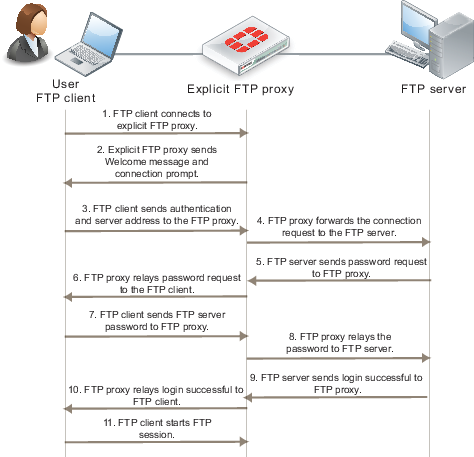
The following steps occur when a user starts an FTP client to connect to an FTP server using the explicit FTP proxy. Any RFC-compliant FTP client can be used. This example describes using a command-line FTP client. Some FTP clients may require a custom FTP proxy connection script.
- The user enters a command on the FTP client to connect to the explicit FTP proxy.
For example, if the IP address of the FortiGate interface on which the explicit FTP proxy is enabled is 10.31.101.100, enter:
ftp 10.31.101.100
- The explicit FTP proxy responds with a welcome message and requests the user’s FTP proxy user name and password and a username and address of the FTP server to connect to:
Connected to 10.31.101.100.
220 Welcome to Fortigate FTP proxy
Name (10.31.101.100:user):
You can change the message by editing the FTP Explicit Banner Message replacement message.
- At the prompt the user enters their FTP proxy username and password and a username and address for the FTP server. The FTP server address can be a domain name or numeric IP address. This information is entered using the following syntax:
<proxy-user>:<proxy-password>:<server-user>@<server-address>
For example, if the proxy username and password are
p-nameandp-passand a valid username for the FTP server iss-nameand the server’s IP address isftp.example.comthe syntax would be:
p-name:p-pass:s-name@ftp.example.com
|
|
If the FTP proxy accepts anonymous logins p-name and p-pass can be any characters. |
- The FTP proxy forwards the connection request, including the user name, to the FTP server.
- If the user name is valid for the FTP server it responds with a password request prompt.
- The FTP proxy relays the password request to the FTP client.
- The user enters the FTP server password and the client sends the password to the FTP proxy.
- The FTP proxy relays the password to the FTP server.
- The FTP server sends a login successful message to the FTP proxy.
- The FTP proxy relays the login successful message to the FTP client.
- The FTP client starts the FTP session.
All commands entered by the client are relayed by the proxy to the server. Replies from the server are relayed back to the FTP client.
Explicit FTP proxy session
From a simple command line FTP client connecting to an the previous sequence could appear as follows:
ftp 10.31.101.100 21
Connected to 10.31.101.100.
220 Welcome to Fortigate FTP proxy
Name (10.31.101.100:user): p-name:p-pass:s-name@ftp.example.com
331 Please specify the password.
Password: s-pass
230 Login successful.
Remote system type is UNIX
Using binary mode to transfer files.
ftp>
General explicit FTP proxy configuration steps
You can use the following general steps to configure the explicit FTP proxy.
To enable the explicit FTP proxy - web-based manager:
- Go to System > Network > Explicit Proxy > Explicit FTP Proxy Options. Select Enable Explicit FTP Proxy to turn on the explicit FTP proxy.
- Select Apply.
The Default Firewall Policy Action is set to Deny and requires you to add a explicit FTP proxy policy to allow access to the explicit FTP proxy. This configuration is recommended and is a best practice because you can use policies to control access to the explicit FTP proxy and also apply security features and authentication. - Go to System > Network > Interface and select one or more interfaces for which to enable the explicit web proxy. Edit the interface and select Enable Explicit FTP Proxy.
|
|
Enabling the explicit FTP proxy on an interface connected to the Internet is a security risk because anyone on the Internet who finds the proxy could use it to hide their source address. If you enable the proxy on such an interface make sure authentication is required to use the proxy. |
- Go to Policy & Objects > Policy > Explicit Proxy and select Create New and set the Explicit Proxy Type to FTP.
You can add multiple explicit FTP proxy policies. - Configure the policy as required to accept the traffic that you want to be processed by the explicit FTP proxy.
The source address of the policy should match client source IP addresses. The firewall address selected as the source address cannot be assigned to a FortiGate interface. The Interface field of the firewall address must be blank or it must be set to Any.
The destination address of the policy should match the IP addresses of FTP servers that clients are connecting to. The destination address could be all to allow connections to any FTP server.
If Default Firewall Policy Action is set to Deny, traffic sent to the explicit FTP proxy that is not accepted by an explicit FTP proxy policy is dropped. If Default Firewall Policy Action is set to Allow then all FTP proxy sessions that don’t match a policy are allowed.
For example the following explicit FTP proxy policy allows users on an internal network to access FTP servers on the Internet through the wan1 interface of a FortiGate unit.
| Explicit Proxy Type | FTP |
| Source Address | Internal_subnet |
| Outgoing Interface | wan1 |
| Destination Address | all |
| Schedule | always |
| Action | ACCEPT |
The following explicit FTP proxy policy requires users on an internal network to authenticate with the FortiGate unit before accessing FTP servers on the Internet through the wan1 interface.
| Explicit Proxy Type | FTP |
| Source Address | Internal_subnet |
| Outgoing Interface | wan1 |
| Destination Address | all |
| Action | AUTHENTICATE |
- Select Create New to add an Authentication Rule and configure the rule as follows:
| Groups | Proxy-Group |
| Source Users | (optional) |
| Schedule | always |
- Add security profiles as required and select OK.
- You can add multiple authentication rules to apply different authentication for different user groups and users and also apply different security profiles and logging settings for different users.
- Select OK.
To enable the explicit FTP proxy - CLI:
- Enter the following command to turn on the explicit FTP proxy. This command also changes the explicit FTP proxy port to 2121.
config ftp-proxy explicit
set status enable
set incoming-port 2121
end
The default explicit FTP proxy configuration has
sec-default-actionset todenyand requires you to add a security policy to allow access to the explicit FTP proxy.
- Enter the following command to enable the explicit FTP proxy for the internal interface.
config system interface
edit internal
set explicit-ftp-proxy enable
end
end
- Use the following command to add a firewall address that matches the source address of users who connect to the explicit FTP proxy.
config firewall address
edit Internal_subnet
set type iprange
set start-ip 10.31.101.1
set end-ip 10.31.101.255
end
The source address for a ftp-proxy security policy cannot be assigned to a FortiGate unit interface.
- Use the following command to add an explicit FTP proxy policy that allows all users on the internal subnet to use the explicit FTP proxy for connections through the wan1 interface to the Internet.
config firewall explicit-proxy-policy
edit 0
set proxy ftp
set dstintf wan1
set scraddr Internal_subnet
set dstaddr all
set action accept
set schedule always
end
- Use the following command to add an explicit FTP proxy policy that allows authenticated users on the internal subnet to use the explicit FTP proxy for connections through the wan1 interface to the Internet.
config firewall explicit-proxy-policy
edit 0
set proxy ftp
set dstintf wan1
set scraddr Internal_subnet
set dstaddr Fortinet-web-sites
set action accept
set schedule always
set identity-based enable
config identity-based-policy
edit 1
set groups Proxy-group
set schedule always
end
end
Restricting the IP address of the explicit FTP proxy
You can use the following command to restrict access to the explicit FTP proxy using only one IP address. The IP address that you specify must be the IP address of an interface that the explicit FTP proxy is enabled on. You might want to use this option if the explicit FTP proxy is enabled on an interface with multiple IP addresses.
For example, to require uses to connect to the IP address 10.31.101.100 to connect to the explicit FTP proxy:
config ftp-proxy explicit
set incoming-ip 10.31.101.100
end
Restricting the outgoing source IP address of the explicit FTP proxy
You can use the following command to restrict the source address of outgoing FTP proxy packets to a single IP address. The IP address that you specify must be the IP address of an interface that the explicit FTP proxy is enabled on. You might want to use this option if the explicit FTP proxy is enabled on an interface with multiple IP addresses.
For example, to restrict the outgoing packet source address to 172.20.120.100:
config ftp-proxy explicit
set outgoing-ip 172.20.120.100
end
Security profiles, threat weight, device identification, and the explicit FTP proxy
You can apply antivirus, data leak prevention (DLP), and SSL/SSH inspection to explicit FTP proxy sessions. Security profiles are applied by selecting them in an explicit FTP proxy policy or an authentication rule in an FTP proxy security policy.
Traffic accepted by explicit FTP proxy policies contributes to threat weight data.
The explicit FTP proxy is not compatible with device identification.
Explicit FTP proxy options and SSL/SSH inspection
Since the traffic accepted by the explicit FTP proxy is known to be FTP and since the ports are already known by the proxy, the explicit FTP proxy does not use the FTP port proxy options settings.
When adding UTM features to an FTP proxy security policy, you must select a proxy options profile. In most cases you can select the default proxy options profile. You could also create a custom proxy options profile.
The explicit FTP proxy supports the following proxy options:
- Block Oversized File and oversized file limit
The explicit FTP proxy does not support the following protocol options:
- Client comforting
Explicit FTP proxy sessions and antivirus
For explicit FTP proxy sessions, the FortiGate unit applies antivirus scanning to FTP file GET and PUT requests. The FortiGate unit starts virus scanning a file in an FTP session when it receives a file in the body of an FTP request.
Flow-based virus scanning is not available for explicit FTP proxy sessions. Even if the FortiGate unit is configured to use flow-based antivirus, explicit FTP proxy sessions use the regular virus database.
Example users on an internal network connecting to FTP servers on the Internet through the explicit FTP with RADIUS authentication and virus scanning
This example describes how to configure the explicit FTP proxy for the example network shown below. In this example, users on the internal network connect to the explicit FTP proxy through the Internal interface with IP address 10.31.101.100. The explicit web proxy is configured to use port 2121 so to connect to an FTP server on the Internet users must first connect to the explicit FTP proxy using IP address 10.31.101.100 and port 2121.
Example explicit FTP proxy network topology
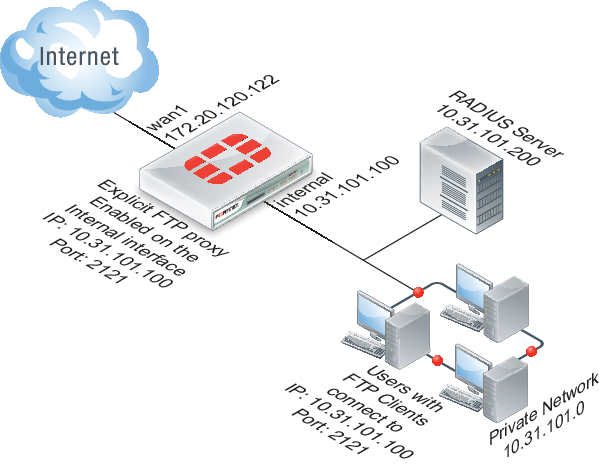
In this example, explicit FTP proxy users must authenticate with a RADIUS server before getting access to the proxy. To apply authentication, the security policy that accepts explicit FTP proxy traffic includes an identity based policy that applies per session authentication to explicit FTP proxy users and includes a user group with the RADIUS server in it. The identity based policy also applies UTM virus scanning and DLP.
General configuration steps
This section breaks down the configuration for this example into smaller procedures. For best results, follow the procedures in the order given:
- Enable the explicit FTP proxy and change the FTP port to 2121.
- Enable the explicit FTP proxy on the internal interface.
- Add a RADIUS server and user group for the explicit FTP proxy.
- Add a user identity security policy for the explicit FTP proxy.
- Enable antivirus and DLP features for the identity-based policy.
Configuring the explicit FTP proxy - web-based manager
Use the following steps to configure the explicit FTP proxy from FortiGate web-based manager.
To enable and configure the explicit FTP proxy
- Go to System > Network > Explicit Proxy > Explicit FTP Proxy Options and change the following settings:
| Enable Explicit FTP Proxy | Select. |
| Listen on Interface | No change. This field will eventually show that the explicit web proxy is enabled for the Internal interface. |
| FTP Port | 2121 |
| Default Firewall Policy Action | Deny |
- Select Apply.
To enable the explicit FTP proxy on the Internal interface
- Go to System > Network > Interface, edit the Internal interface and select Enable Explicit FTP Proxy.
To add a RADIUS server and user group for the explicit FTP proxy
- Go to User & Device > Authentication > RADIUS Servers.
- Select Create New to add a new RADIUS server:
| Name | RADIUS_1 |
| Primary Server Name/IP | 10.31.101.200 |
| Primary Server Secret | RADIUS_server_secret |
- Go to User > User > User Groups and select Create New.
| Name | Explict_proxy_user_group |
| Type | Firewall |
| Remote groups | RADIUS_1 |
| Group Name | ANY |
- Select OK.
To add a security policy for the explicit FTP proxy
- Go to Policy &Objects > Objects > Addresses and select Create New.
- Add a firewall address for the internal network:
| Address Name | Internal_subnet |
| Type | Subnet |
| Subnet / IP Range | 10.31.101.0 |
| Interface | Any |
- Go to Policy & Objects > Policy > Explicit Proxy and select Create New.
- Configure the explicit FTP proxy security policy.
| Explicit Proxy Type | FTP |
| Source Address | Internal_subnet |
| Outgoing Interface | wan1 |
| Destination Address | all |
| Action | AUTHENTICATE |
- Under Configure Authentication Rules select Create New to add an authentication rule:
| Groups | Explicit_policy |
| Users | Leave blank |
| Schedule | always |
- Turn on Antivirus and Web Filter and select the default profiles for both.
- Select the default proxy options profile.
- Select OK.
- Make sure Enable IP Based Authentication is not selected and Default Authentication Method is set to Basic.
- Select OK.
Configuring the explicit FTP proxy - CLI
Use the following steps to configure the example explicit web proxy configuration from the CLI.
To enable and configure the explicit FTP proxy
- Enter the following command to enable the explicit FTP proxy and set the TCP port that proxy accepts FTP connections on to 2121.
config ftp-proxy explicit
set status enable
set incoming-port 2121
set sec-default-action deny
end
To enable the explicit FTP proxy on the Internal interface
- Enter the following command to enable the explicit FTP proxy on the internal interface.
config system interface
edit internal
set explicit-ftp-proxy enable
end
To add a RADIUS server and user group for the explicit FTP proxy
- Enter the following command to add a RADIUS server:
config user radius
edit RADIUS_1
set server 10.31.101.200
set secret RADIUS_server_secret
end
- Enter the following command to add a user group for the RADIUS server.
config user group
edit Explicit_proxy_user_group
set group-type firewall
set member RADIUS_1
end
To add a security policy for the explicit FTP proxy
- Enter the following command to add a firewall address for the internal subnet:
config firewall address
edit Internal_subnet
set type iprange
set start-ip 10.31.101.1
set end-ip 10.31.101.255
end
- Enter the following command to add the explicit FTP proxy security policy:
config firewall explicit-proxy-policy
edit 0
set proxy ftp
set dstintf wan1
set srcaddr Internal_subnet
set dstaddr all
set action accept
set identity-based enable
set ipbased disable
set active-auth-method basic
config identity-based-policy
edit 0
set groups Explicit_Proxy_user_group
set schedule always
set utm-status enable
set av-profile default
set profile-protocol-options default
end
end
Testing and troubleshooting the configuration
You can use the following steps to verify that the explicit FTP proxy configuration is working as expected. These steps use a command line FTP client.
To test the explicit web proxy configuration
- From a system on the internal network start an FTP client and enter the following command to connect to the FTP proxy:
ftp 10.31.101.100
The explicit FTP proxy should respond with a message similar to the following:
Connected to 10.31.101.100.
220 Welcome to Fortigate FTP proxy
Name (10.31.101.100:user):
- At the prompt enter a valid username and password for the RADIUS server followed by a user name for an FTP server on the Internet and the address of the FTP server. For example, if a valid username and password on the RADIUS server is ex_name and ex_pass and you attempt to connect to an FTP server at ftp.example.com with user name s_name, enter the following at the prompt:
Name (10.31.101.100:user):ex_name:ex_pass:s_name@ftp.example.com
- You should be prompted for the password for the account on the FTP server.
- Enter the password and you should be able to connect to the FTP server.
- Attempt to explore the FTP server file system and download or upload files.
- To test UTM functionality, attempt to upload or download an ECAR test file. Or upload or download a tex file containing text that would be matched by the DLP sensor.
For eicar test files, go to http://www.eicar.org/.
Explicit FTP proxy sessions and user limits
FTP clients do not open large numbers of sessions with the explicit FTP proxy. Most sessions stay open for a short while depending on how long a user is connected to an FTP server and how large the file uploads or downloads are. So unless you have large numbers of FTP users, the explicit FTP proxy should not be adding large numbers of sessions to the session table.
Explicit FTP proxy sessions and user limits are combined with explicit web proxy session and user limits. For information about explicit proxy session and user limits, see Explicit web proxy sessions and user limits.

