Traffic shaping methods
In FortiOS, there are three types of traffic shaping configurations. Each has a specific function, and all can be used together in varying configurations. Policy shaping enables you to define the maximum bandwidth and the guaranteed bandwidth set for a security policy. Per-IP shaping enables you to define traffic control on a more granular level. Application traffic shaping goes further, enabling traffic controls on specific applications or application groupings.
This chapter describes the types of traffic shapers and how to configure them in the web‑based manager and the CLI.
Traffic shaping options
When configuring traffic shaping for your network, there are three different methods to control the flow of network traffic to ensure that the desired traffic gets through while also limiting the bandwidth that users use for other less important or bandwidth consuming traffic. The three shaping options are:
- Shared policy shaping - bandwidth management by security policies
- Per-IP shaping - bandwidth management by user IP addresses
- Application control shaping - bandwidth management by application
Shared policy shaping and Per-IP shaping are enabled within the security policy under Policy & Objects > Policy. Application control shaping is enabled under Security Profiles > Application Control, and setting the Action to Traffic Shaping.
The three different traffic shaping options offered by the FortiGate unit can also be enabled at the same time within the same security policy. Generally, the hierarchy for traffic shapers in FortiOS is:
- Application Control shaper
- Security policy shaper
- Per-IP shaper
Within this hierarchy, if an application control list has a traffic shaper defined, it will always have precedence over any other security policy shaper. For example, the Facebook application control example shown in Application control shaping will supersede any security policy enabled traffic shapers. While the Facebook application may reach its maximum bandwidth, the user can still have the bandwidth room available from the shared shaper and, if enabled, the per-IP shaper.
Equally, any security policy shared shaper will have precedence over any per-IP shaper. However, traffic that exceeds any of these shapers will be dropped. For example, the policy shaper will take effect first, however, if the per-IP shaper limit is reached first, then traffic for that user will be dropped even if the shared shaper limit for the policy has not been exceeded.
Shared policy shaping
Traffic shaping by security policy enables you to control the maximum and/or guaranteed throughput for a selected security policy. When configuring a shaper, you can select to apply the bandwidth shaping per policy or for all policies. Depending on your selection, the FortiGate unit will apply the shaping rules differently.
Per policy
When selecting a shaper to be per policy, the FortiGate unit will apply the shaping rules defined to each security policy individually.
For example, the shaper is set to be per policy with a maximum bandwidth of 1000 Kb/s. There are four security policies monitoring traffic through the FortiGate unit. Three of these have the shaper enabled. Each security policy has the same maximum bandwidth of 1000 Kb/s.
Per policy traffic shaping is compatible with client/server (active-passive) transparent mode WAN optimization rules. Traffic shaping is ignored for peer-to-peer WAN optimization and for client/server WAN optimization not operating in transparent mode.
All policies
When selecting a shaper to be for all policies -All Policies using this shaper - the FortiGate unit applies the shaping rules to all policies using the same shaper. For example, the shaper is set to be per policy with a maximum bandwidth of 1000 Kb/s. There are four security policies monitoring traffic through the FortiGate unit. All four have the shaper enabled. Each security policy must share the defined 1000 Kb/s, and is set on a first come, first served basis. For example, if policy 1 uses 800 Kb/s, the remaining three must share 200 Kb/s. As policy 1 uses less bandwidth, it is opened up to the other policies to use as required. Once used, any other policies will encounter latency until free bandwidth opens from a policy currently in use.
Maximum and guaranteed bandwidth
The maximum bandwidth instructs the security policy what the largest amount of traffic allowed using the policy. Depending on the service or the users included for the security policy, this number can provide a larger or smaller throughput depending on the priority you set for the shaper.
The Maximum Bandwidth can be set to a value of between 1 and 16776000 kbit/s. The Web-Based Manager gives an error if any value outside of this range is used, but in the CLI a value of 0 can be entered. Setting maximum-bandwidth to 0 (zero) prevents any traffic from going through the policy.
The guaranteed bandwidth ensures there is a consistent reserved bandwidth available for a given service or user. When setting the guaranteed bandwidth, ensure that the value is significantly less than the bandwidth capacity of the interface, otherwise no other traffic will pass through the interface or very little an potentially causing unwanted latency.
Traffic priority
Select a Traffic Priority of high, medium or low, so the FortiGate unit manages the relative priorities of different types of traffic. For example, a policy for connecting to a secure web server that needed to support e-commerce traffic should be assigned a high traffic priority. Less important services should be assigned a low priority. The firewall provides bandwidth to low-priority connections only when bandwidth is not needed for high-priority connections.
Be sure to enable traffic shaping on all security policies. If you do not apply any traffic shaping rule to a policy, the policy is set to high priority by default. Distribute security policies over all three priority queues.
VLAN, VDOM and virtual interfaces
Policy-based traffic shaping does not use queues directly. It shapes the traffic and if the packet is allowed by the security policy, then a priority is assigned. That priority controls what queue the packet will be put in upon egress. VLANs, VDOMs, aggregate ports and other virtual devices do not have queues and as such, traffic is sent directly to the underlying physical device where it is queued and affected by the physical ports. This is also the case with IPsec connections.
Shared traffic shaper configuration settings
To configure a shared traffic shaper go to Policy & Objects > Objects > Traffic Shapers and select the Create New “Plus” sign to create a new traffic shaper.
| Type | Select Shared. |
| Name | Enter a name for the traffic shaper. |
| Apply Shaper | When selecting a shaper to be Per Policy, the FortiGate unit will apply the shaping rules defined to each security policy individually. For example, the shaper is set to be per policy with a maximum bandwidth of 1000 Kb/s. There are four security policies monitoring traffic through the FortiGate unit. Three of these have the shaper enabled. Each security policy has the same maximum bandwidth of 1000 Kb/s. Per policy traffic shaping is compatible with client/server (active-passive) transparent mode WAN optimization rules. Traffic shaping is ignored for peer-to-peer WAN optimization and for client/server WAN optimization not operating in transparent mode. When selecting a shaper to be for all policies - For All Policies Using This Shaper - the FortiGate unit applies the shaping rules to all policies using the same shaper. For example, the shaper is set to be per policy with a maximum bandwidth of 1000 Kb/s. There are four security policies monitoring traffic through the FortiGate unit. All four have the shaper enabled. Each security policy must share the defined 1000 Kb/s, and is set on a first come, first served basis. For example, if policy 1 uses 800 Kb/s, the remaining three must share 200 Kb/s. As policy 1 uses less bandwidth, it is opened up to the other policies to use as required. Once used, any other policies will encounter latency until free bandwidth opens from a policy currently in use. |
| Traffic Priority | Select level of importance Priority so the FortiGate unit manages the relative priorities of different types of traffic. For example, a policy for connecting to a secure web server needed to support e-commerce traffic should be assigned a high traffic priority. Less important services should be assigned a low priority. If you do not apply any traffic shaping priority, the priority is set to high priority by default. |
| Maximum Bandwidth | The maximum bandwidth instructs the security policy what the largest amount of traffic allowed using the policy. Depending on the service or the users included for the security policy, this number can provide a larger or smaller throughput depending on the priority you set for the shaper. Setting Maximum Bandwidth to 0 (zero) provides unlimited bandwidth. |
| Guaranteed Bandwidth | The guaranteed bandwidth ensures there is a consistent reserved bandwidth available for a given service or user. When setting the guaranteed bandwidth, ensure that the value is significantly less than the bandwidth capacity of the interface, otherwise no other traffic will pass through the interface or very little and potentially causing unwanted latency. Setting Guaranteed Bandwidth to 0 (zero) provides unlimited bandwidth. |
| DSCP | Enter the number for the DSCP value. You can use the FortiGate Differentiated Services feature to change the DSCP (Differentiated Services Code Point) value for all packets accepted by a policy. The network can use these DSCP values to classify, mark, shape, and police traffic, and to perform intelligent queuing. DSCP features are applied to traffic by configuring the routers on your network to apply different service levels to packets depending on the DSCP value of the packet. For more information, see Differentiated Services. |
Example
The following steps creates a Per Policy traffic shaper called “Throughput” with a maximum traffic amount of 720,000 Kb/s, and a guaranteed traffic of 150,000 Kb/s with a high traffic priority.
To create the shared shaper - web-based manager:
- Go to Policy & Objects > Objects > Traffic Shapers and select the Create New “Plus” sign.
- Set the Type to Shared.
- Enter the Name
Throughput. - Set the Apply shaper field to Per Policy.
- Set the Traffic Priority to High.
- Select the Maximum Bandwidth check box and enter the value
150000. - Select the Guaranteed Bandwidth check box and enter the value
120000. - Select OK.
To create the shared shaper - CLI:
config firewall shaper traffic-shaper
edit Throughput
set per-policy enable
set maximum-bandwidth 150000
set guaranteed-bandwidth 120000
set priority high
end
Per-IP shaping
Traffic shaping by IP enables you to apply traffic shaping to all source IP addresses in the security policy. As well as controlling the maximum bandwidth users of a selected policy, you can also define the maximum number of concurrent sessions.
Per-IP traffic shaping enables you limit the behavior of every member of a policy to avoid one user from using all the available bandwidth - it now is shared within a group equally. Using a per-IP shaper avoids having to create multiple policies for every user you want to apply a shaper to. Per-IP traffic shaping is not supported over NP2 interfaces.
Per-IP traffic shaping configuration settings
To configure per-IP traffic shaping go to Firewall Policy & Objects > Objects > Traffic Shapers > Per-IP and select the Create New “Plus” sign.
| Type | Select Per-IP. |
| Name | Enter a name for the per-IP traffic shaper. |
| Maximum Bandwidth | The maximum bandwidth instructs the security policy what the largest amount of traffic allowed using the policy. Depending on the service or the users included for the security policy, this number can provide a larger or smaller throughput depending on the priority you set for the shaper. Setting Maximum Bandwidth to 0 (zero) provides unlimited bandwidth. |
| Maximum Concurrent Connections | Enter the maximum allowed concurrent connection. |
| Forward DSCP Reverse DSCP |
Enter the number for the DSCP value. You can use the FortiGate Differentiated Services feature to change the DSCP (Differentiated Services Code Point) value for all packets accepted by a policy. The network can use these DSCP values to classify, mark, shape, and police traffic, and to perform intelligent queuing. DSCP features are applied to traffic by configuring the routers on your network to apply different service levels to packets depending on the DSCP value of the packet. For more information, see Differentiated Services. |
Example
The following steps create a Per-IP traffic shaper called “Accounting” with a maximum traffic amount of 720,000 Kb/s, and the number of concurrent sessions of 200.
To create the Per-IP shaper - web-based manager:
- Go to Policy & Objects > Objects > Traffic Shapers and select the Create New “Plus” Icon.
- Set the Type to Per-IP.
- Enter the Name
Accounting. - Select the Maximum Bandwidth checkbox and enter the value
720000. - Select the Maximum Concurrent Sessions checkbox and enter the value
200. - Select OK.
To create the shared shaper - CLI:
config firewall shaper per-ip-shaper
edit Accounting
set max-bandwidth 720000
set max-concurrent-session 200
end
Adding Per-IP traffic shapers to a security policy
Per-IP traffic shaping is supported by IPv6 security policies. You can add any Per-IP traffic shaper to an IPv6 security policy in the CLI.
Example
The following steps show you how to add an existing Per-IP traffic shaper to an IPv6 security policy. Ensure that you have already created a Per-IP traffic shaper.
To add a Per-IP traffic shaper to an IPv6 security policy - web-based manager:
- Go to Policy & Objects > Policy > IPv6 and click the Create New “Plus” icon.
- Set the Incoming Interface to internal.
- Set the Source Address to All.
- Set the Outgoing interface to any.
- Set the Destination address to all.
- Set the Schedule to Always.
- Set the Service to Any.
- Set the Action to Accept.
- Under Traffic Shaping enable Per-IP Shaper and select your shaper from the dropdown menu.
To add a Per-IP traffic shaper to an IPv6 security policy- CLI:
config firewall policy6
edit <security_policy_ID_number>
set per-ip-shaper <per_ip_shaper>
end
Application control shaping
Traffic shaping is also possible for specific applications for both shared and per-IP shaping. Through the Security Profiles > Application Control feature, you can configure a specific application’s maximum bandwidth. When configuring the application control features, if the application is set to pass, you can set the traffic shaping options. The shapers available are those set up in the Policy & Objects > Objects > Traffic Shaping menu.
For more information on configuring application control shapers, see the FortiOS Guide.
Example
This example sets the traffic shaping definition for Facebook to a medium priority, a default traffic shaper.
To add traffic shaping for Facebook - web-based manager:
- Go to Security Profiles > Application Control.
- Select the Create New “Plus” icon in the upper right corner of the screen to create a new application group, and enter the name
Web. - Select OK.
- In the Categories section, click Social.Media and select Traffic Shaping from the dropdown menu. The Traffic Shaping Settings are now displayed below.
- In the Traffic Shaping Settings section, set Forward to medium-priority.
- Click Apply.
To add traffic shaping for Facebook using a Shared Shaper- CLI:
config application list
edit web
config entries
edit 1
set category 23
set application 17735
set action pass
set shaper medium-priority
end
|
|
Application Control Per-IP shaping options are not available in the web-based manager, but you can apply Per-IP shapers in the CLI. |
To add traffic shaping for Facebook using a Per-IP Shaper- CLI:
config application list
edit web
config entries
edit 1
set category 23
set application 17735
set action pass
set per-ip-shaper {per_ip_shaper_name}
end
Enabling traffic shaping in the security policy
All traffic shapers are enabled within a security policy, including the Application Control shapers. As such, the shapers go into effect after any DoS detection policies, and before any routing or packet scanning occurs.
Traffic shaping is also supported for IPv6 policies.
To enable traffic shaping - web-based manager:
- Go to Policy & Objects > Policy > IPv4.
- Click Create New or select an existing policy and click Edit.
- Navigate to the Traffic Shaping section, enable the Per-IP Shaper and select an option from the drop down list.
- Select OK.
Shapers applied in the security policy affect outbound or traffic to a destination. To affect inbound, or download, traffic, enable both the Shared Traffic Shaper and the Reverse Shaper. For more information, see Reverse direction traffic shaping.
To enable traffic shaping - CLI:
config firewall {policy or policy6}
edit <policy_number>
...
set traffic-shaper <shaper_name>
set per-ip-shaper <per_ip_shaper_name>
end
Reverse direction traffic shaping
The shaper you select for the security policy (shared shaper) will affect the traffic in the direction defined in the policy. For example, if the source port is port 1 and the destination is port 3, the shaping affects the flow in this direction only, that is, the upload or outbound direction. By selecting Shared Traffic Shaper Reverse Direction, you can define the traffic shaper for the policy in the opposite direction, that is, the download or inbound direction. In this example, from port 3 to port 1.
To add a reverse shaper
- Go to Policy & Objects > Policy > IPv4.
- Click Create New or select an existing policy and click Edit.
- Navigate to the Traffic Shaping section, enable the Shared Shaper and select a shaper from the dropdown list.
- Enable the Reverse Shaper and select a shaper from the dropdown list.
- Select OK.
Setting the reverse direction only
There may be instances where you only need traffic shaping for incoming connections, which is in the “reverse” direction of typical traffic shapers.
To add a reverse shaper - web-based manager:
- Go to Policy & Objects > Policy > IPv4.
- Select Traffic Shaping.
- Select Shared Traffic Shaper Reverse Direction and select the shaper from the list.
- Select OK.
To configure a reverse-only shaper - CLI:
config firewall policy
edit <policy_number>
...
set traffic-shaper-reverse <shaper_name>
end
Type of Service priority
Type of service (ToS) is an 8-bit field in the IP header that enables you to determine how the IP datagram should be delivered, using criteria of Delay, Throughput, Priority, Reliability, and Cost. Each quality helps gateways determine the best way to route datagrams. A router maintains a ToS value for each route in its routing table. The lowest priority ToS is 0; the highest is 7 when bits 3, 4, and 5 are all set to 1. There are other seldom used or reserved bits that are not listed here.
Together these bits are the ToS variable of the tos‑based-priority command. The router tries to match the ToS of the datagram to the ToS on one of the possible routes to the destination. If there is no match, the datagram is sent over a zero ToS route. Using increased quality may increase the cost of delivery because better performance may consume limited network resources.
Each bit represents the priority as per RFC 1349:
- 1000 - minimize delay
- 0100 - maximize throughput
- 0010 - maximize reliability
- 0001 - minimize monetary cost
The ToS value is set in the CLI using the commands:
config system tos-based-priority
edit <sequence-number>
set tos [0-15]
set priority [high | medium | low]
end
Where tos is the value of the type of service bit in the IP datagram header with a value between 0 and 15, and priority is the priority of this type of service priority. These priority levels conform to the firewall traffic shaping priorities, as defined in RFC 1349.
For example, if you want to configure the FortiGate unit so that reliability is the first priority, set the tos value to 4.
config system tos-based-priority
edit 1
set tos 4
set priority high
end
For a list of ToS values and their DSCP equivalents see ToS and DSCP traffic mapping.
Example
config system tos-based-priority
edit 1
set tos 1
set priority low
next
edit 4
set tos 4
set priority medium
next
edit 6
set tos 6
set priority high
next
end
ToS in FortiOS
Traffic shaping and ToS follow the following sequence:
- The CLI command
tos-based-priorityacts as atos-to-prioritymapping. FortiOS maps the ToS to a priority when it receives a packet. - Traffic shaping settings adjust the packet’s priority according the traffic.
- Deliver the packet based on its priority.
Differentiated Services
Differentiated Services describes a set of end-to-end Quality of Service (QoS) capabilities. End-to-end QoS is the ability of a network to deliver service required by specific network traffic from one end of the network to another. By configuring differentiated services, you configure your network to deliver particular levels of service for different packets based on the QoS specified by each packet.
Differentiated Services (also called DiffServ) is defined by RFC 2474 and 2475 as enhancements to IP networking to enable scalable service discrimination in the IP network without the need for per-flow state and signaling at every hop. Routers that can understand differentiated services sort IP traffic into classes by inspecting the DS field in IPv4 header or the Traffic Class field in the IPv6 header.
You can use the FortiGate Differentiated Services feature to change the DSCP (Differentiated Services Code Point) value for all packets accepted by a policy. The network can use these DSCP values to classify, mark, shape, and police traffic, and to perform intelligent queuing. DSCP features are applied to traffic by configuring the routers on your network to apply different service levels to packets depending on the DSCP value of the packet.
If the differentiated services feature is not enabled, the FortiGate unit treats traffic as if the DSCP value is set to the default (00), and will not change IP packets' DSCP field. DSCP values are also not applied to traffic if the traffic originates from a FortiGate unit itself.
The FortiGate unit applies the DSCP value and IPsec encryption to the differentiated services (formerly ToS) field in the first word of the IP header. The typical first word of an IP header, with the default DSCP value, is 4500:
- 4 for IPv4
- 5 for a length of five words
- 00 for the default DSCP value
You can change the packet's DSCP field for traffic initiating a session (forward) or for reply traffic (reverse) and enable each direction separately and configure it in the security policy.
Changes to DSCP values in a security policy affect new sessions. If traffic must use the new DSCP values immediately, clear all existing sessions.
DSCP is enabled using the CLI command:
config firewall policy
edit <policy_number>
...
set diffserv-forward enable
set diffservcode-forward <binary_integer>
set diffserv-reverse enable
set diffservcode-rev <binary_integer>
end
For more information on the different DCSP commands, see the examples below and the CLI Reference. If you only set diffserv-forward and diffserv-reverse without setting the corresponding diffvercode values, the FortiGate unit will reset the bits to zero.
For a list of DSCP values and their ToS equivalents see ToS and DSCP traffic mapping. DSCP values can also be defined within a shared shaper as a single value, and per-IP shaper for forward and reverse directions.
DSCP examples
For all the following DSCP examples, the FortiGate and client PC configuration is the following diagram and used firewall-based DSCP configurations.
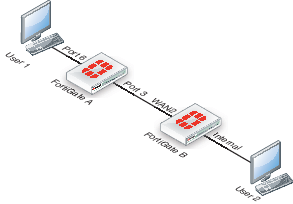
Example
In this example, an ICMP ping is executed between User 1 and FortiGate B, through a FortiGate unit. DSCP is disabled on FortiGate B, and FortiGate A contains the following configuration:
config firewall policy
edit 2
set srcintf port6
set dstintf port3
set src addr all
set dstaddr all
set action accept
set schedule always
set service ANY
set diffserv-forward enable
set diffservcode-forward 101110
end
As a result, FortiGate A changes the DSCP field for outgoing traffic, but not to its reply traffic. The binary DSCP values used map to the following hexadecimal ToS field values, which are observable by a sniffer (also known as a packet tracer):
- DSCP 000000 is TOS field 0x00
- DSCP 101110 is TOS field 0xb8, the recommended DSCP value for expedited forwarding (EF)
If you performed an ICMP ping between User 1 and User 2, the following output illustrates the IP headers for the request and the reply by sniffers on each of FortiGate unit’s network interfaces. The right-most two digits of each IP header are the ToS field, which contains the DSCP value.

Example
In this example, an ICMP ping is executed between User 1 and FortiGate B, through FortiGate A. DSCP is disabled on FortiGate B, and FortiGate A contains the following configuration:
config firewall policy
edit 2
set srcintf port6
set dstintf port3
set src addr all
set dstaddr all
set action accept
set schedule always
set service ANY"
set diffserv-forward enable
set diffserv-rev enable
set diffservcode-forward 101110
set diffservcode-rev 101111
end
As a result, FortiGate A changes the DSCP field for both outgoing traffic and its reply traffic. The binary DSCP values in map to the following hexadecimal ToS field values, which are observable by a sniffer (also known as a packet tracer):
- DSCP 000000 is TOS field 0x00
- DSCP 101110 is TOS field 0xb8, the recommended DSCP value for expedited forwarding (EF)
- DSCP 101111 is TOS field 0xbc
If you performed an ICMP ping between User 1 and User 2, the output below illustrates the IP headers observed for the request and the reply by sniffers on each of FortiGate A's and FortiGate B's network interfaces. The right-most two digits of each IP header are the ToS field, which contains the DSCP value.

Example
In this example, an ICMP ping is executed between User 1 and FortiGate B, through FortiGate A. DSCP is enabled for both traffic directions on FortiGate A, and enabled only for reply traffic on FortiGate B. FortiGate A contains the following configuration:
config firewall policy
edit 2
set srcintf port6
set dstintf port3
set src addr all
set dstaddr all
set action accept
set schedule always
set service ANY
set diffserv-forward enable
set diffserv-rev enable
set diffservcode-forward 101110
set diffservcode-rev 101111
end
FortiGate B contains the following configuration:
config firewall policy
edit 2
set srcintf wan2
set dstintf internal
set src addr all
set dstaddr all
set action accept
set schedule always
set service ANY
set diffserv-rev enable
set diffservcode-rev 101101
end
As a result, FortiGate A changes the DSCP field for both outgoing traffic and its reply traffic, and FortiGate B changes the DSCP field only for reply traffic. The binary DSCP values in this configuration map to the following hexadecimal ToS field values:
- DSCP 000000 is TOS field 0x00
- DSCP 101101 is TOS field 0xb4
- DSCP 101110 is TOS field 0xb8, the recommended DSCP value for expedited forwarding (EF)
- DSCP 101111 is TOS field 0xbc
If you performed an ICMP ping between User 1 and User 2, the output below illustrates the IP headers observed for the request and the reply by sniffers on each of FortiGate A's and FortiGate B's network interfaces. The right-most two digits of each IP header are the ToS field, which contains the DSCP value.

Example
In this example, HTTPS and DNS traffic is sent from User 1 to FortiGate B, through FortiGate A. DSCP is enabled for both traffic directions on FortiGate A, and enabled only for reply traffic on FortiGate B. FortiGate A contains the following configuration:
config firewall policy
edit 2
set srcintf port6
set dstintf port3
set src addr all
set dstaddr all
set action accept
set schedule always
set service ANY
set diffserv-forward enable
set diffserv-rev enable
set diffservcode-forward 101110
set diffservcode-rev 101111
end
FortiGate B contains the following configuration:
config firewall policy
edit 2
set srcintf wan2
set dstintf internal
set src addr all
set dstaddr all
set action accept
set schedule always
set service ANY
set diffserv-rev enable
set diffservcode-rev 101101
end
As a result, FortiGate A changes the DSCP field for both outgoing traffic and its reply traffic, but FortiGate B changes the DSCP field only for reply traffic which passes through its internal interface. Since the example traffic does not pass through the internal interface, FortiGate B does not mark the packets. The binary DSCP values in this configuration map to the following hexadecimal ToS field values:
- DSCP 000000 is TOS field 0x00
- DSCP 101101 is TOS field 0xb4, which is configured on FortiGate B but not observed by the sniffer because the example traffic originates from the FortiGate unit itself, and therefore does not match that security policy.
- DSCP 101110 is TOS field 0xb8, the recommended DSCP value for expedited forwarding (EF)
- DSCP 101111 is TOS field 0xbc
If you sent HTTPS or DNS traffic from User 1 to FortiGate B, the following would illustrate the IP headers observed for the request and the reply by sniffers on each of FortiGate A's and FortiGate B's network interfaces. The right-most two digits of each IP header are the ToS field, which contains the DSCP value.

ToS and DSCP traffic mapping
There are two types of traffic mapping: Type of Service (ToS) or DSCP (Differentiated Services Code Point). Only one method can be used at a time, with ToS set as the default method. You can set the type used and attributes in the CLI.
To set ToS or DSCP traffic mapping
config system global
set traffic-priority {tos | dscp}
set traffic-priority-level {low | medium | high }
end
Mapping of DSCP and ToS hexadecimal values for QoS
| Service Class | DSCP Bits | DSCP Value | ToS Value | ToS Hexidecimal |
|---|---|---|---|---|
| Network Control | 111000 | 56-63 | 224 | 0xE0 |
| Internetwork Control | 110000 | 48-55 | 192 | 0xC0 |
| Critical - Voice Data (RTP) | 101110 | 46 | 184 | 0xB8 |
| 101000 | 40 | 160 | 0xA0 | |
| Flash Override Video Data | 100010 | 34 | 136 | 0x88 |
| 100100 | 36 | 144 | 0x90 | |
| 100110 | 38 | 152 | 0x98 | |
| 100000 | 32 | 128 | 0x80 | |
| Flash Voice Control | 011010 | 26 | 104 | 0x68 |
| 011100 | 28 | 112 | 0x70 | |
| 011110 | 30 | 120 | 0x78 | |
| 011000 | 24 | 96 | 0x60 | |
| Immediate Deterministic (SNA) | 010010 | 18 | 72 | 0x48 |
| 010100 | 20 | 80 | 0x50 | |
| 010110 | 22 | 88 | 0x58 | |
| 010000 | 16 | 64 | 0x40 | |
| Priority Controlled Load | 001010 | 10 | 40 | 0x28 |
| 001100 | 12 | 48 | 0x30 | |
| 001110 | 14 | 56 | 0x38 | |
| 001000 | 8 | 32 | 0x20 | |
| Routine - Best Effort | 000000 | 0 | 0 | 0x00 |
| Routine - Penalty Box | 000010 | 2 | 8 | 0x08 |
Traffic Shaper Monitor
You can view statistical information about traffic shapers and their bandwidth from Policy & Objects > Monitor > Traffic Shaper Monitor.
| Refresh | Select to refresh the information on the page. |
| Reset | Select to reset the information to clear the current information from the page. New information is included on the page. |
| Report By | Select to display dropped packets or current bandwidth. The chart changes its name so you know what current information is displayed. |
| Traffic Shaper Usage Dropped packets | The bar chart displays the packets dropped by the traffic shaper. |
| Traffic Shaper Usage Current Bandwidth | The bar chart displays the current bandwidth of traffic shapers. |

