Configuring FRUP
The FortiGate Redundant UTM Protocol (FRUP) provides similar redundancy to FGCP full mesh HA in a single unified design that includes redundant switching and routing. FRUP is available on the FortiGate-100D and will be expanded to other models in future releases.
A FRUP cluster consists of 2 (and only 2) identical FortiGate-100D units that have dual redundant links to all connected devices and networks and can include redundant FortiAP units. Connections to the Internet normally use the wan1 and wan2 interfaces for redundant connections. Connections to internal networks and servers use redundant connections to FortiGate-100D switch ports. FRUP uses the FortiGate-100D switch ports for full mesh HA instead of external redundant switches.
Each device or network has a default active connection to one of the FortiGate units and a default backup connection to the other. Ideally, the default active and backup connections should balance traffic between the FortiGate units in the cluster so that both FortiGate units are processing the same amount of traffic.
FRUP uses virtual IPs and virtual MACs so that when a failover occurs, network devices do not have to learn new IP or MAC addresses. FRUP also synchronizes the configuration between the units in the cluster.
Use the following CLI command on both FortiGate-100D units to configure FRUP.
config system ha
set hbdev "ha1" 50 "ha2" 100
set override disable
set priority 128
set frup enable
config frup-settings
set active-interface "wan2"
set active-switch-port 14
set backup-interface "wan1"
end
end
Both units must have the same heartbeat device configuration and have FRUP enabled to form a FRUP cluster. Active interface and switch ports must be complementary according to your configuration (see the following example).
FRUP and the mode of the FortiGate hardware switch
FRUP is only available when the FortiGate's internal hardware switch is configured to operate as a switch. You can determine the current internal switch mode using the following command:
get system status
...
Internal Switch Mode: switch
...
If Internal Switch Mode is set to switch the hardware switch is operating in the correct mode and you can configure FRUP. If Internal Switch Mode is set to interface or hub you need to enter the following command to set it to hardware switch mode:
config system global
set internal-switch-mode switch
end
Before you can set the switch to hardware switch mode you need to remove all configuration settings that will be affected by this change. This includes firewall policies and DHCP servers. Also, if you have configured a software switch you must remove it. You can use the following command:
config system virtual-switch
purge
end
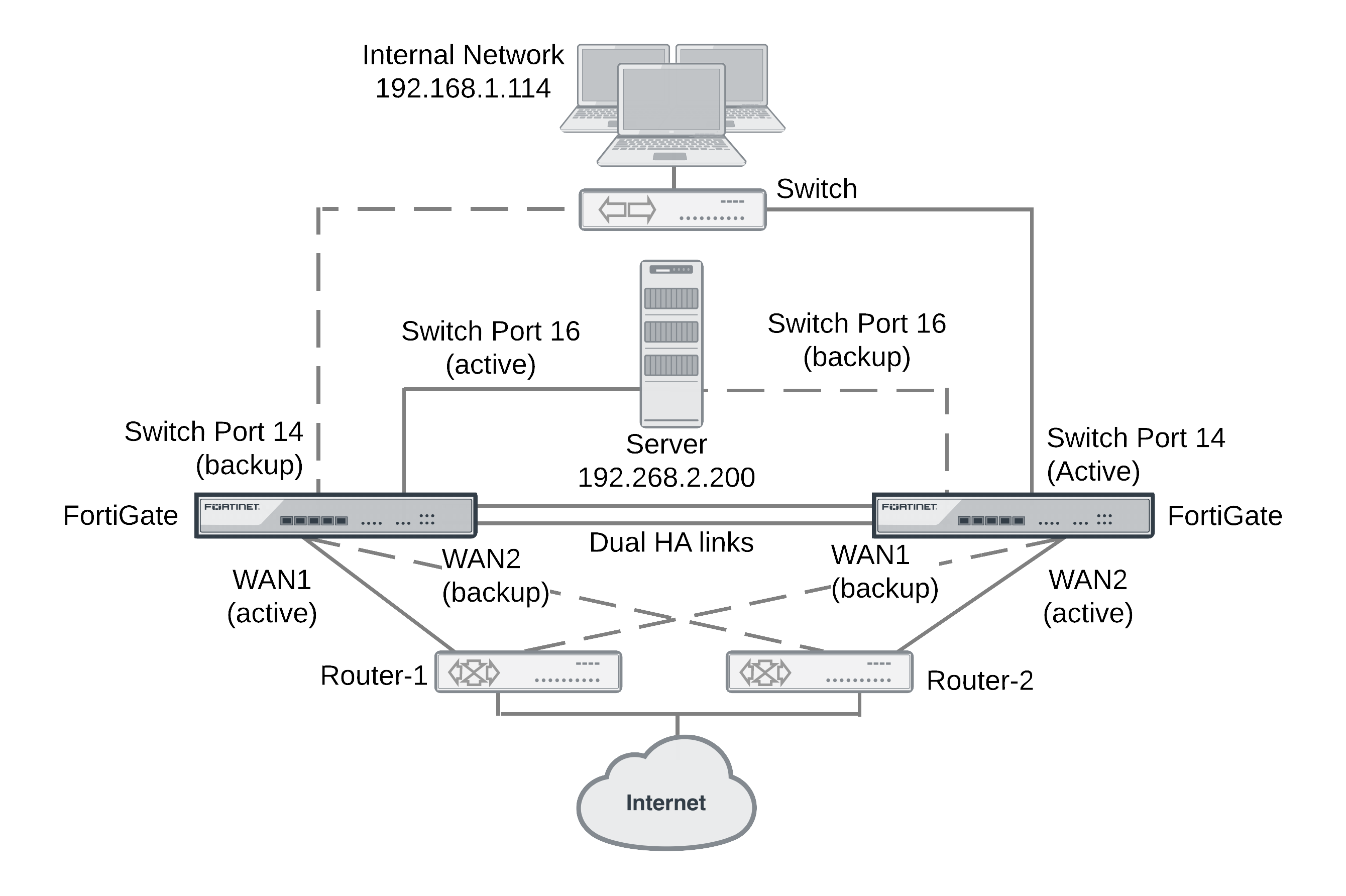
FRUP configuration example
This example includes the following:
- Two FortiGate-100D units (FGT-A and FGT-B)
- HA1 and HA2 for redundant HA heartbeat connectivity between FGT-1 and FGT-2
- Dual gateways (router1 and router2):
- FGT-A has an active connection from WAN1 to router-1 and a backup connection from WAN2 to router-2
- FGT-B has an active connection from WAN2 to router-2 and a backup connection from WAN1 to router-1
- Dual connections to the internal network and an internal server:
- FGT-A has an active connection to an internal server using switch port 16 and a backup connection to the internal network using switch port 14
- FGT-B has a backup connection to an internal server using switch port 16 and an active connection to the internal network using switch port 14
- FortiGate interfaces use virtual IP addresses and pseudo-MAC physical addresses, all devices continue to send to the same IP/Mac and don't need to re-learn after a failover
- Both FortiGate units will handle and process traffic
- Backup links are normally administratively down
- Sessions and the FortiGate configuration are synchronized between the cluster units
Example FRUP configuration
Configuring FGT-A
Change the host name to FGT-A. Set up FGT-A with dual redundant internet links using WAN1 and WAN2. Set WAN1 and WAN2 interfaces to use static addressing and set both static routes to same priority and distance.
From CLI enter the following command:
config system ha
set hbdev "ha1" 50 "ha2" 100
set override disable
set priority 255
set frup enable
config frup-settings
set active-interface "wan1"
set active-switch-port 16
set backup-interface "wan2"
end
end
Configuring FGT-B
Use the same firmware version as FGT-A and set the FortiGate unit to factory defaults. Change the host name to FGT-B.
From CLI enter the following command:
config system ha
set hbdev "ha1" 50 "ha2" 100
set override disable
set priority 128
set frup enable
config frup-settings
set active-interface "wan2"
set active-switch-port 14
set backup-interface "wan1"
end
end
Connecting, testing and operating the FRUP cluster
Connect to the FortiGate-100D units to the network as shown in the diagram and power them on. The FortiGate-100D units should find each other and form a cluster.
Traffic from the server (IP: 192.168.1.200) connected to port16 should pass through FGT-A (since port16 is the active-switch-port in FGT-A) and to the Internet using WAN1 (since WAN1 is the active-interface in FGT-A).
Run a sniffer on both FortiGate units using the following command:
diagnose sniffer packet any ‘icmp’ 4
interfaces=[any]
filters=[icmp]
Then run a ping to 4.2.2.2 from the server. The sniffer should show results similar to the following:
Traffic initiating from a host on the internal network (for example, IP: 192.168.1.114) connected to port14 should flow through FGT-B (since port14 is the active-switch-port in FGT-B) to the Internet using WAN2 (since WAN2 is FGT-B’s active interface).
Run the same sniffer on both FortiGate units and then run a ping to 74.125.226.1 from the internal network. The sniffer should show results similar to the following:
Shutdown FGT-A.
Traffic from the internal network should be handled by FGT-B using WAN1 and WAN2 interfaces:
To re-establish the cluster after a failover you need to restart both FortiGate-100D units. Just re-starting FGT-A may not bring the cluster back online.

