Configure the dynamically-addressed VPN peer
It is assumed that this FortiGate unit (branch_2) has already had its public facing interface, for example the wan1, configured with the proper dynamic DNS configuration.
Configure branch_2, the dynamic address side
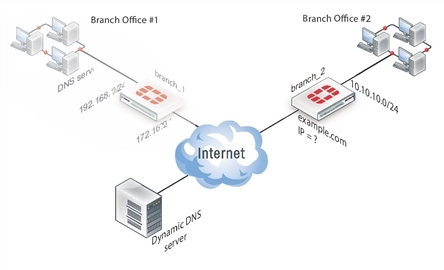
Configuring the dynamically-addressed VPN peer includes:
Configuring branch_2 VPN tunnel settings
Define the Phase 1 parameters needed to establish a secure connection with the remote peer. See Phase 1 parameters. During this procedure you need to choose if you will be using route-based or policy-based VPNs.
To configure branch_2 VPN tunnel settings
- Go to VPN > IPsec > Tunnels and create the new custom tunnel or edit an existing tunnel.
- Edit the Phase 1 Proposal (if it is not available, you may need to click the Convert to Custom Tunnel button).
- Enter the following information:
| Name | Enter branch_2, a name to identify the VPN tunnel. This name appears in Phase 2 configurations, security policies, and the VPN monitor. |
| Remote Gateway | Select Static IP Address. The remote peer this FortiGate is connecting to has a static IP public address. If the remote interface is PPPoE do not select Retrieve default gateway from server. |
| IP Address | Enter 172.16.20.1. The IP address of the public interface to the remote peer. |
| Enter 172.16.20.1 The IP address of the public interface to the remote peer. |
Select Aggressive. |
- Select Advanced and complete the following:
| Local ID | Enter example.com.A character string used by the branch_2 FortiGate unit to identify itself to the remote peer. This value must be identical to the value in the This peer ID field of the Phase 1 remote gateway configuration on the branch_1 remote peer. See Configure the dynamically-addressed VPN peer. |
- Open the Phase 2 Selectors panel.
Define the Phase 2 parameters needed to create a VPN tunnel with the remote peer. For details on Phase 2, see Phase 2 parameters. - Enter the following information and select OK.
| Name | Enter branch_2_phase2.A name to identify this Phase 2 configuration. |
| Phase 1 | Select branch_2. The name of the Phase 1 configuration that you defined earlier. |
Configuring branch_2 security policies
Define security policies to permit communications between the private networks through the VPN tunnel. Route-based and policy-based VPNs require different security policies. For detailed information about creating security policies, see Defining VPN security policies.
After defining the two address ranges, select one of Creating branch_2 route-based security policies or Creating branch_2 policy-based security policies to configure the appropriate VPN policies.
Define address ranges for branch_2 security policies
Define VPN connection names for the address ranges of the private networks. These addresses are used in the security policies that permit communication between the networks. For more information, see Defining VPN security policies.
Define an address name for the IP address and netmask of the private network behind the local FortiGate unit.
To define branch_2 address ranges
- Go to Policy & Objects > Objects > Addresses.
- Select Create New.
- Enter the following information, and select OK.
| Name | Enter branch_2_internal. Enter a meaningful name. |
| Type | Select Subnet. |
| Subnet / IP Range | Enter 10.10.10.0/24.Include the netmask or specify a specific range. |
| Interface | Select internal. The interface that will be handling the traffic from the internal network. |
Define an address name for the IP address and netmask of the private network behind the remote peer.
- Select Create New.
- Enter the following information, and select OK.
| Name | Enter branch_1_internal. A meaningful name for the private network at the remote end of the VPN tunnel. |
| Type | Select Subnet. |
| Subnet / IP Range | Enter 192.168.1.0/24. Include the netmask. Optionally you can specify a range |
| Interface | Select any. The interface that will be handling the remote VPN traffic on this FortiGate unit. If you are unsure, or multiple interfaces may be handling this traffic use any. |
Creating branch_2 route-based security policies
Define ACCEPT security policies to permit communication between the branch_2 and branch_1 private networks. Once the route-based policy is configured a routing entry must be configured to route traffic over the VPN interface.
Define a policy to permit the branch_2 local FortiGate unit to initiate a VPN session with the branch_1 VPN peer.
To create route-based security policies
- Go to Policy & Objects > Policy > IPv4 and select Create New.
- Leave the Policy Type as Firewall and leave the Policy Subtype as Address.
- Enter the following information, and select OK.
| Incoming Interface | Select internal. The interface that connects to the private network behind this FortiGate unit. |
| Source Address | Select branch_2_internal. Select the address name for the private network behind this FortiGate unit. |
| Outgoing Interface | Select branch_2. The VPN Tunnel (IPsec Interface). |
| Destination Address | Select branch_1_internal. The address name the private network behind the remote peer. |
| Action | Select ACCEPT. |
| Enable NAT | Disable. |
| Comments | Route-based: Initiate a branch_2 to branch_1 VPN tunnel. |
Define a policy to permit the branch_1 remote VPN peer to initiate VPN sessions.
- Select Create New.
- Leave the Policy Type as Firewall and leave the Policy Subtype as Address.
- Enter the following information, and select OK.
| Incoming Interface | Select branch_2. The VPN Tunnel (IPsec Interface). |
| Source Address | Select branch_1_internal. The address name for the private network behind the remote peer. |
| Outgoing Interface | Select internal. The interface connecting the private network behind this FortiGate unit. |
| Destination Address | Select branch_2_internal. The address name for the private network behind this FortiGate unit. |
| Action | Select ACCEPT. |
| Enable NAT | Disable. |
| Comments | Route-based: Initiate a branch_1 to branch_2 internal VPN tunnel. |
- Optionally configure any other security policy settings you require such as UTM or traffic shaping for this policy.
- Place these policies in the policy list above any other policies having similar source and destination addresses. This will ensure VPN traffic is matched against the VPN policies before any other policies.
To create routing entry for VPN interface - CLI
config router static
edit 5
set dst 0.0.0.0 0.0.0.0
set dynamic-dateway enable
set device wan1
next
end
This routing entry must be added in the CLI because the dynamic-gateway option is not available in the web-based manager.
Creating branch_2 policy-based security policies
Define an IPsec policy to permit VPN sessions between the private networks. Define an IPsec policy to permit the VPN sessions between the local branch_2 unit and the remote branch_1 unit.
- Go to Policy & Objects > Policy > IPv4 and select Create New.
- Enter the following information, and select OK.
| Incoming Interface | Select internal. The interface connecting the private network behind this FortiGate unit. |
| Source Address | Select branch_2_internal. The address name for the private network behind this local FortiGate unit. |
| Outgoing Interface | Select wan1. The FortiGate unit’s public interface. |
| Destination Address | Select branch_1_internal. The address name for the private network behind branch_1, the remote peer. |
| VPN Tunnel | Select Use Existing and select branch_2 from the drop-down list. The name of the Phase 1 tunnel. |
| Select Allow traffic to be initiated from the remote site. | |
| Comments | Policy-based: allows traffic in either direction to initiate the VPN tunnel. |
- Optionally configure any other security policy settings you require such as UTM or traffic shaping for this policy.
- Place these policies in the policy list above any other policies having similar source and destination addresses. This will ensure VPN traffic is matched against the VPN policies before any other policies.

