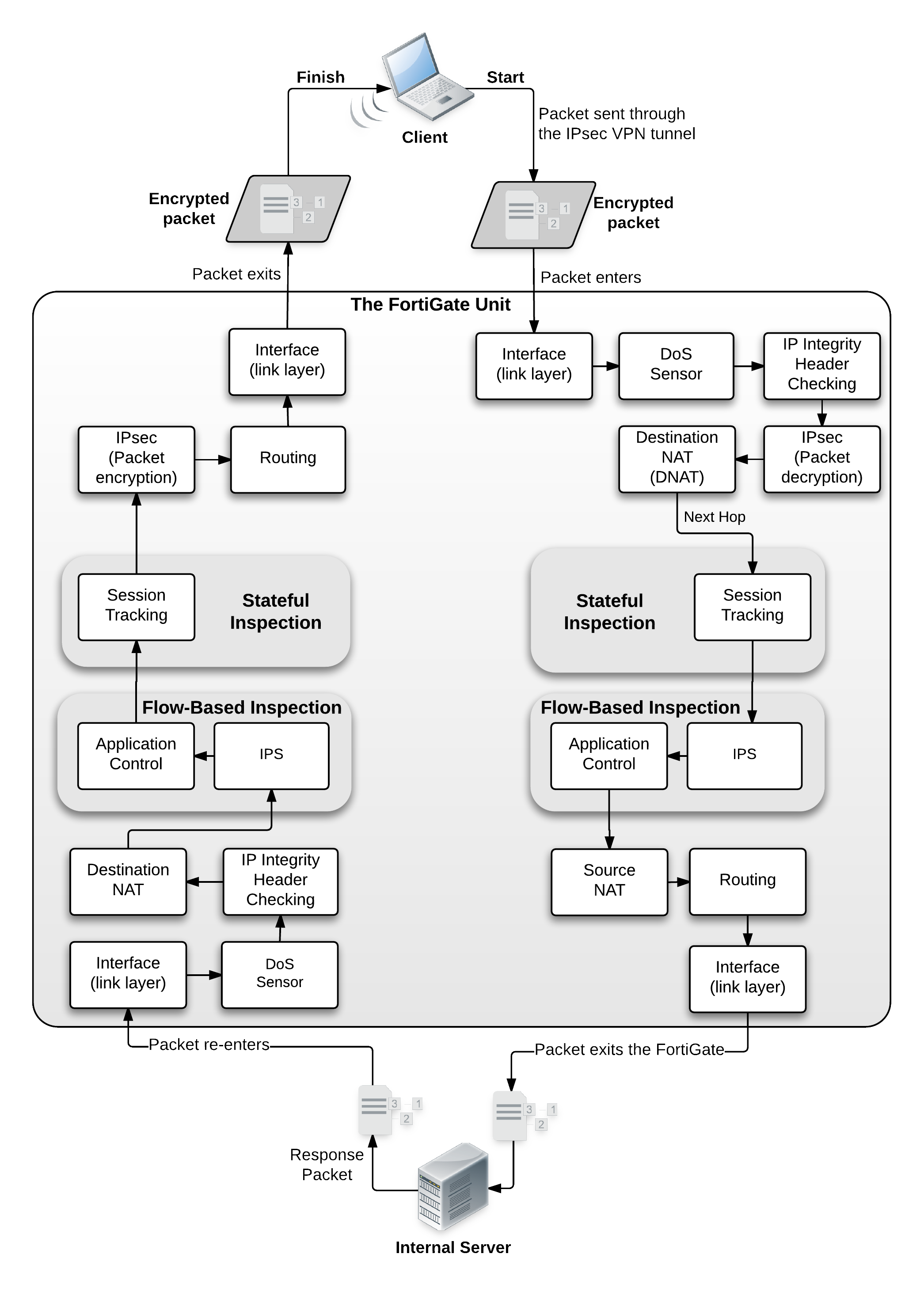
> Chapter 20 - Parallel Path Processing - Life of a Packet > Example 3 Dialup IPsec VPN with Application Control
Dialup IPsec VPN with Application control example
This example includes these steps:
- FortiGate unit receives IPsec encrypted packet from the Internet.
- Packet intercepted by FortiGate unit interface.
- DoS sensor checks to ensure the sender is valid and not attempting a denial of service attack.
- IP integrity header checking. If the packet is OK it continues, otherwise it is dropped.
- IPsec
- Packet matches IPsec phase 1
- Packet is unencrypted
- Interface policy
- Destination NAT
- Next hop route
- Stateful Inspection
- Session Tracking
- Flow-based inspection
- IPS
- Application Control
- Source NAT
- Routing
- Interface transmission to network
- Packet forwarded to internal server
Response from server
- Server sends response packet
- Packet intercepted by FortiGate unit interface
- DoS sensor checks to ensure the sender is valid and not attempting a denial of service attack.
- IP integrity header checking. If the packet is OK it continues, otherwise it is dropped.
- Destination NAT
- Flow-based inspection
- IPS
- Application Control
- Stateful Inspection
- Session Tracking
- IPsec
- Packet is encrypted
- Routing
- Interface transmission to network
- Encrypted Packet returns to internet