Configuring WAN optimization
This chapter describes FortiGate WAN optimization client server architecture and other concepts you need to understand to be able to configure FortiGate WAN optimization.
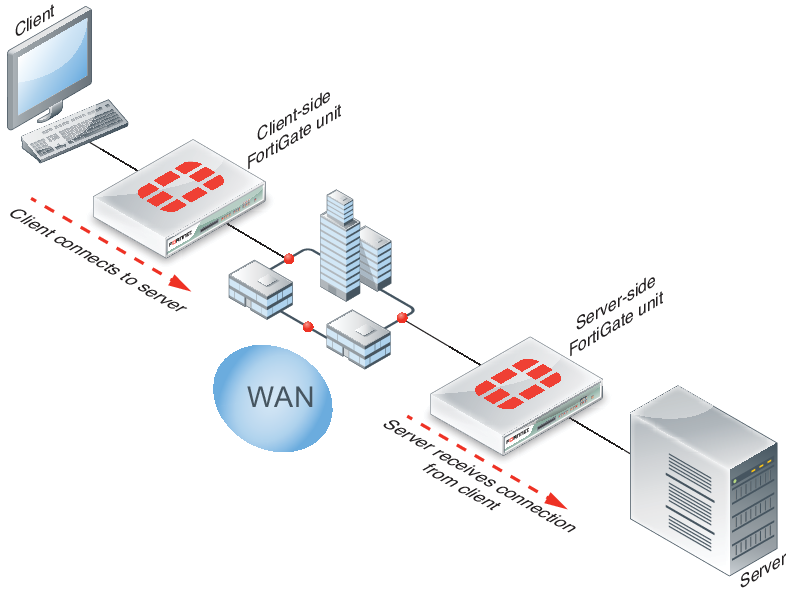
Client/server architecture
Traffic across a WAN typically consists of clients on a client network communicating across a WAN with a remote server network. The clients do this by starting communication sessions from the client network to the server network. These communication sessions can be open text over the WAN or they can be encrypted by SSL VPN or IPsec VPN.
To optimize these sessions, you can add WAN optimization security policies to the client-side FortiGate unit to accept sessions from the client network that are destined for the server network. The client-side FortiGate unit is located between the client network and the WAN. WAN optimization security policies include WAN optimization profiles that control how the traffic is optimized.
These same security policies can also include security profiles that apply UTM and NGFW features to WAN Optimization traffic.
The client-side FortiGate unit must also include the IP address of the server-side FortiGate unit in its WAN optimization peer configuration. The server-side FortiGate unit is located between the server network and the WAN, The peer configuration allows the client-side FortiGate unit to find the server-side FortiGate unit and attempt to establish a WAN optimization tunnel with it.
For the server-side FortiGate unit you must add a security policy with wanopt as the Incoming Interface. This security policy allows the FortiGate unit to accept WAN optimization sessions from the client-side FortiGate unit. For the server-side FortiGate unit to accept a WAN optimization connection it must have the client-side FortiGate unit in its WAN optimization peer configuration.
|
|
WAN optimization profiles are only added to the client-side WAN optimization security policy. The server-side FortiGate unit employs the WAN optimization settings set in the WAN optimization profile on the client-side FortiGate unit. |
Client/server architecture
When both peers are identified the FortiGate units attempt to establish a WAN optimization tunnel between them. WAN optimization tunnels use port 7810. All optimized data flowing across the WAN between the client-side and server-side FortiGate units use this tunnel. WAN optimization tunnels can be encrypted use SSL encryption to keep the data in the tunnel secure.
Any traffic can be sent through a WAN optimization tunnel. This includes SSL and IPsec VPN traffic. However, instead of configuring SSL or IPsec VPN for this communication you can add SSL encryption using the WAN optimization tunnel.
In addition to basic identification by peer host ID and IP address you can configure WAN optimization authentication using certificates and pre-shared keys to improve security. You can also configure FortiGate units involved in WAN optimization to accept connections from any identified peer or restrict connections to specific peers.
The FortiClient application can act in the same manner as a client-side FortiGate unit to optimize traffic between a computer running FortiClient and a FortiGate unit.
WAN optimization peers
The client-side and server-side FortiGate units are called WAN optimization peers because all of the FortiGate units in a WAN optimization network have the same peer relationship with each other. The client and server roles just relate to how a session is started. Any FortiGate unit configured for WAN optimization can be a client-side and a server-side FortiGate unit at the same time, depending on the direction of the traffic. Client-side FortiGate units initiate WAN optimization sessions and server-side FortiGate units respond to the session requests. Any FortiGate unit can simultaneously be a client-side FortiGate unit for some sessions and a server-side FortiGate unit for others.
WAN optimization peer and tunnel architecture
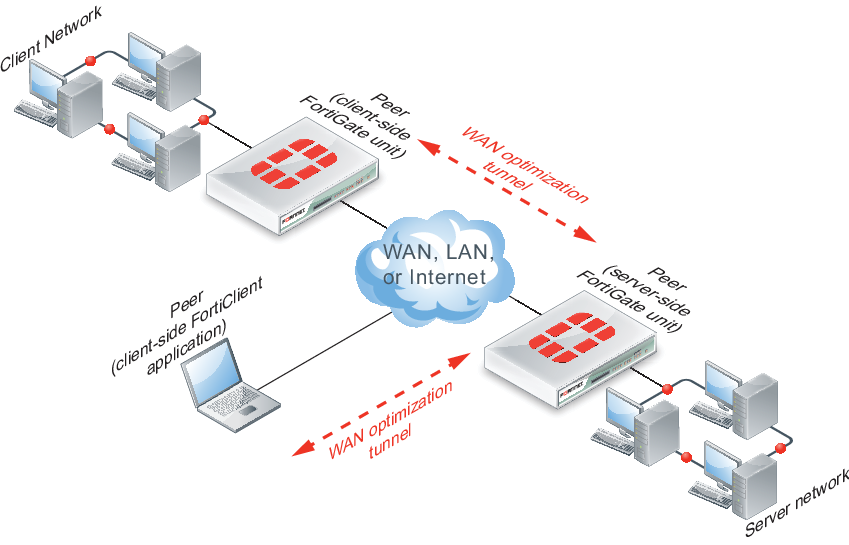
To identify all of the WAN optimization peers that a FortiGate unit can perform WAN optimization with, you add host IDs and IP addresses of all of the peers to the FortiGate unit configuration. The peer IP address is actually the IP address of the peer unit interface that communicates with the FortiGate unit.
Manual (peer-to-peer) and active-passive WAN optimization
You can create manual (peer-to-peer) and active-passive WAN optimization configurations.
Manual (peer to peer) configurations
Manual configurations allow for WAN optimization between one client-side FortiGate unit and one server-side FortiGate unit. To create a manual configuration you add a manual mode WAN optimization security policy to the client-side FortiGate unit. The manual mode policy includes the peer ID of a server-side FortiGate unit.
In a manual mode configuration, the client-side peer can only connect to the named server‑side peer. When the client-side peer initiates a tunnel with the server-side peer, the packets that initiate the tunnel include extra information so that the server-side peer can determine that it is a peer-to-peer tunnel request. This extra information is required because the server-side peer does not require a WAN optimization policy; however, you need to add the client peer host ID and IP address to the server-side FortiGate unit peer list.
In addition, from the server-side FortiGate unit CLI you must and an Explicit Proxy security policy with proxy set to wanopt and the destination interface and network set to the network containing the servers that clients connect to over the WAN optimization tunnel. WAN optimization tunnel requests are accepted by the explicit proxy policy and if the client-side peer is in the server side peer’s address list the traffic is forwarded to the servers on the destination network.
Manual mode client-side policy
You must configure manual mode client-side policies from the CLI. From the GUI a manual mode policy has WAN Optimization turned on and includes the following text beside the WAN optimization field: Manual (Profile: <profile-name>. Peer: <peer-name>.
Add a manual mode policy to the client-side FortiGate unit from the CLI. The policy enables WAN optimization, sets wanopt-detection to off, and uses the wanopt-peer option to specify the server-side peer. The following example uses the default WAN optimization profile.
config firewall policy
edit 2
set srcintf internal
set dstintf wan1
set srcaddr client-subnet
set dstaddr server-subnet
set action accept
set schedule always
set service ALL
set wanopt enable
set wanopt-detection off
set wanopt-profile default
set wanopt-peer server
next
end
Manual mode server-side explicit proxy policy
The server-side explicit proxy policy allows connections from the WAN optimization tunnel to the server network by setting the proxy type to wanopt. You must add policies that set proxy to wanopt from the CLI and these policies do not appear on the GUI. The policy should look like the following:
configure firewall explicit-proxy-policy
edit 3
set proxy wanopt
set dstintf internal
set srcaddr all
set dstaddr server-subnet
set action accept
set schedule always
set service ALL
next
end
Active-passive configurations
Active-passive WAN optimization requires an active WAN optimization policy on the client-side FortiGate unit and a passive WAN optimization policy on the server-side FortiGate unit. The server-side FortiGate unit also requires an explicit proxy policy with proxy set to wanopt.
You can use the passive policy to control WAN optimization address translation by specifying transparent mode or non-transparent mode. SeeWAN optimization transparent mode. You can also use the passive policy to apply security profiles, web caching, and other FortiGate features at the server-side FortiGate unit. For example, if a server-side FortiGate unit is protecting a web server, the passive policy could enable web caching.
A single passive policy can accept tunnel requests from multiple FortiGate units as long as the server-side FortiGate unit includes their peer IDs and all of the client-side FortiGate units include the server-side peer ID.
Active client-side policy
Add an active policy to the client-side FortiGate unit by turning on WAN Optimization and selecting active. Then select a WAN optimization Profile. From the CLI the policy could look like the following:
config firewall policy
edit 2
set srcintf internal
set dstintf wan1
set srcaddr client-subnet
set dstaddr server-subnet
set action accept
set schedule always
set service ALL
set wanopt enable
set wanopt-detection active
set wanopt-profile default
next
end
Server-side tunnel policy
The server-side requires an explicit proxy policy that sets the proxy to wanopt. You must add this policy from the CLI and policies with proxy set to wanopt do not appear on the GUI. From the CLI the policy could look like the following:
configure firewall explicit-proxy-policy
edit 3
set proxy wanopt
set dstintf internal
set srcaddr all
set dstaddr server-subnet
set action accept
set schedule always
set service ALL
next
end
Server-side passive policy
Add a passive policy to the server-side FortiGate unit by selecting Enable WAN Optimization and selecting passive. Then set the Passive Option to transparent. From the CLI the policy could look like the following:
config firewall policy
edit 2
set srcintf "wan1"
set dstintf "internal"
set srcaddr "all"
set dstaddr "all"
set action accept
set schedule "always"
set service "ANY"
set wanopt enable
set wanopt-detection passive
set wanopt-passive-opt transparent
next
WAN optimization profiles
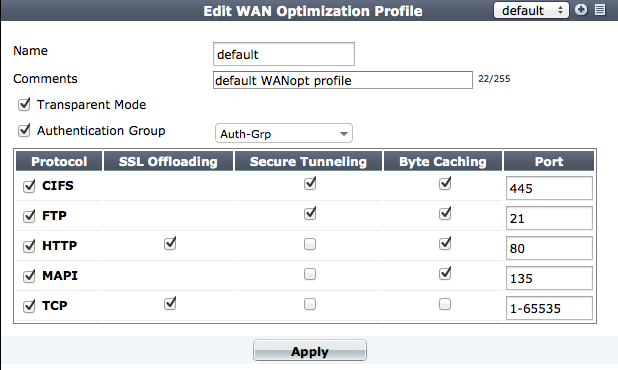
Use WAN optimization profiles to apply WAN optimization techniques to traffic to be optimized. In a WAN optimization profile you can select the protocols to be optimized and for each protocol you can enable SSL offloading (if supported), secure tunneling, byte caching and set the port or port range the protocol uses. You can also enable transparent mode and optionally select an authentication group. You can edit the default WAN optimization profile or create new ones.
To configure a WAN optimization profile go to WAN Opt & Cache > WAN Opt. Profile > Profiles and edit a profile or create a new one.
Configuring a WAN optimization profile
From the CLI you can use the following command to configure a WAN optimization profile to optimize HTTP traffic.
config wanopt profile
edit new-profile
config http
set status enable
end
| Transparent Mode | Servers receiving packets after WAN optimization “see” different source addresses depending on whether or not you select Transparent Mode. For more information, see WAN optimization transparent mode. |
| Authentication Group | Select this option and select an authentication group so that the client and server-side FortiGate units must authenticate with each other before starting the WAN optimization tunnel. You must also select an authentication group if you select Secure Tunneling for any protocol. You must add identical authentication groups to both of the FortiGate units that will participate in the WAN optimization tunnel. For more information, see Configuring authentication groups. |
| Protocol | Select CIFS, FTP, HTTP or MAPI to apply protocol optimization for the selected protocols. See Protocol optimization. Select TCP if the WAN optimization tunnel accepts sessions that use more than one protocol or that do not use the CIFS, FTP, HTTP, or MAPI protocol. |
| SSL Offloading | Select to apply SSL offloading for HTTPS or other SSL traffic. You can use SSL offloading to offload SSL encryption and decryption from one or more HTTP servers to the FortiGate unit. If you enable this option, you must configure the security policy to accept SSL‑encrypted traffic. If you enable SSL offloading, you must also use the CLI command config firewall ssl‑server to add an SSL server for each HTTP server that you want to offload SSL encryption/decryption for. For more information, see Turning on web caching for HTTPS traffic. |
| Secure Tunnelling |
The WAN optimization tunnel is encrypted using SSL encryption. You must also add an authentication group to the profile. For more information, see Secure tunneling. |
| Byte Caching | Select to apply WAN optimization byte caching to the sessions accepted by this rule. For more information, see “Byte caching”. |
| Port | Enter a single port number or port number range. Only packets whose destination port number matches this port number or port number range will be optimized. |
Processing non-HTTP sessions accepted by a WAN optimization profile with HTTP optimization
From the CLI, you can use the following command to configure how to process non-HTTP sessions when a rule configured to accept and optimize HTTP traffic accepts a non-HTTP session. This can occur if an application sends non-HTTP sessions using an HTTP destination port.
config wanopt profile
edit default
config http
set status enable
set tunnel-non-http {disable | enable}
end
To drop non-HTTP sessions accepted by the rule set tunnel-non-http to disable, or set it to enable to pass non‑HTTP sessions through the tunnel without applying protocol optimization, byte-caching, or web caching. In this case, the FortiGate unit applies TCP protocol optimization to non-HTTP sessions.
Processing unknown HTTP sessions
Unknown HTTP sessions are HTTP sessions that do not comply with HTTP 0.9, 1.0, or 1.1. From the CLI, use the following command to specify how a rule handles such HTTP sessions.
config wanopt profile
edit default
config http
set status enable
set unknown-http-version {best-effort | reject | tunnel}
end
To assume that all HTTP sessions accepted by the rule comply with HTTP 0.9, 1.0, or 1.1, select best-effort. If a session uses a different HTTP version, WAN optimization may not parse it correctly. As a result, the FortiGate unit may stop forwarding the session and the connection may be lost. To reject HTTP sessions that do not use HTTP 0.9, 1.0, or 1.1, select reject.
To pass HTTP sessions that do not use HTTP 0.9, 1.0, or 1.1, but without applying HTTP protocol optimization, byte-caching, or web caching, you can also select tunnel. TCP protocol optimization is applied to these HTTP sessions.
Protocol optimization
Protocol optimization techniques optimize bandwidth use across the WAN. These techniques can improve the efficiency of communication across the WAN optimization tunnel by reducing the amount of traffic required by communication protocols. You can apply protocol optimization to Common Internet File System (CIFS), FTP, HTTP, MAPI, and general TCP sessions. You can apply general TCP optimization to MAPI sessions.
For example, CIFS provides file access, record locking, read/write privileges, change notification, server name resolution, request batching, and server authentication. CIFS is a fairly “chatty” protocol, requiring many background transactions to successfully transfer a single file. This is usually not a problem across a LAN. However, across a WAN, latency and bandwidth reduction can slow down CIFS performance.
When you select the CIFS protocol in a WAN optimization profile, the FortiGate units at both ends of the WAN optimization tunnel use a number of techniques to reduce the number of background transactions that occur over the WAN for CIFS traffic.
If a policy accepts a range of different types of traffic, you can set Protocol to TCP to apply general optimization techniques to TCP traffic. However, applying this TCP optimization is not as effective as applying more protocol-specific optimization to specific types of traffic. TCP protocol optimization uses techniques such as TCP SACK support, TCP window scaling and window size adjustment, and TCP connection pooling to remove TCP bottlenecks.
Protocol optimization and MAPI
By default the MAPI service uses port number 135 for RPC port mapping and may use random ports for MAPI messages. The random ports are negotiated through sessions using port 135. The FortiOS DCE-RPC session helper learns these ports and opens pinholes for the messages. WAN optimization is also aware of these ports and attempts to apply protocol optimization to MAPI messages that use them. However, to configure protocol optimization for MAPI you should set the WAN optimization profile to a single port number (usually port 135). Specifying a range of ports may reduce performance.
Byte caching
Byte caching breaks large units of application data (for example, a file being downloaded from a web page) into small chunks of data, labelling each chunk of data with a hash of the chunk and storing those chunks and their hashes in a database. The database is stored on a WAN optimization storage device. Then, instead of sending the actual data over the WAN tunnel, the FortiGate unit sends the hashes. The FortiGate unit at the other end of the tunnel receives the hashes and compares them with the hashes in its local byte caching database. If any hashes match, that data does not have to be transmitted over the WAN optimization tunnel. The data for any hashes that does not match is transferred over the tunnel and added to that byte caching database. Then the unit of application data (the file being downloaded) is reassembled and sent to its destination.
The stored byte caches are not application specific. Byte caches from a file in an email can be used to optimize downloading that same file or a similar file from a web page.
The result is less data transmitted over the WAN. Initially, byte caching may reduce performance until a large enough byte caching database is built up.
To enable byte caching, you select Byte Caching in a WAN optimization profile.
Byte caching cannot determine whether or not a file is compressed (for example a zip file), and caches compressed and non-compressed versions of the same file separately.
Dynamic data chunking for byte caching
Dynamic data chunking can improve byte caching by improving detection of data chunks that are already cached in changed files or in data embedded in traffic using an unknown protocol. Dynamic data chunking is available for HTTP, CIFS and FTP.
Use the following command to enable dynamic data chunking for HTTP in the default WAN optimization profile.
config wanopt profile
edit default
config http
set prefer-chunking dynamic
end
By default dynamic data chunking is disabled and prefer-chunking is set to fix.
WAN optimization transparent mode
WAN optimization is transparent to users. This means that with WAN optimization in place, clients connect to servers in the same way as they would without WAN optimization. However, servers receiving packets after WAN optimization “see” different source addresses depending on whether or not transparent mode is selected for WAN optimization. If transparent mode is selected, WAN optimization keeps the original source address of the packets, so servers appear to receive traffic directly from clients. Routing on the server network should be configured to route traffic with client source IP addresses from the server-side FortiGate unit to the server and back to the server-side FortiGate unit.
|
|
Some protocols, for example CIFS, may not function as expected if transparent mode is not selected. In most cases, for CIFS WAN optimization you should select transparent mode and make sure the server network can route traffic as described to support transparent mode. |
If transparent mode is not selected, the source address of the packets received by servers is changed to the address of the server-side FortiGate unit interface that sends the packets to the servers. So servers appear to receive packets from the server-side FortiGate unit. Routing on the server network is simpler in this case because client addresses are not involved. All traffic appears to come from the server-side FortiGate unit and not from individual clients.
|
|
Do not confuse WAN optimization transparent mode with FortiGate transparent mode. WAN optimization transparent mode is similar to source NAT. FortiGate Transparent mode is a system setting that controls how the FortiGate unit (or a VDOM) processes traffic. |
Configuring Transparent mode
You can configure transparent mode by selecting Transparent in a WAN Optimization profile. The profile is added to an active WAN Optimization policy.
When you configure a passive WAN Optmization policy you can accept the active policy transparent setting or you can override the active policy transparent setting. From the GUI you can do this by setting the Passive Option as follows:
- default use the transparent setting in the WAN Optimization profile added to the active policy (client-side configuration).
- transparent impose transparent mode (override the active policy transparent mode setting). Packets exiting the FortiGate keep their original source addresses.
- non-transparent impose non-transparent mode (override the active policy transparent mode setting). Packets exiting the FortiGate have their source address changed to the address of the server-side FortiGate unit interface that sends the packets to the servers.
From the CLI you can use the following command:
config firewall policy
set wanopt-passive-opt {default | transparent | non-transparent}
end
FortiClient WAN optimization
PCs running the FortiClient application are client-side peers that initiate WAN optimization tunnels with server-side peer FortiGate units. However, you can have an ever-changing number of FortiClient peers with IP addresses that also change regularly. To avoid maintaining a list of such peers, you can instead configure WAN optimization to accept any peer and use authentication to identify FortiClient peers.
Together, the WAN optimization peers apply the WAN optimization features to optimize the traffic flow over the WAN between the clients and servers. WAN optimization reduces bandwidth requirements, increases throughput, reduces latency, offloads SSL encryption/decryption and improves privacy for traffic on the WAN.
For more details, see FortiClient WAN optimization.
Operating modes and VDOMs
To use WAN optimization, the FortiGate units can operate in either NAT/Route or Transparent mode. The client-side and server-side FortiGate units do not have to be operating in the same mode.
As well, the FortiGate units can be configured for multiple virtual domain (VDOM) operation. You configure WAN optimization for each VDOM and configure one or both of the units to operate with multiple VDOMs enabled.
If a FortiGate unit or VDOM is operating in Transparent mode with WAN optimization enabled, WAN optimization uses the management IP address as the peer IP address of the FortiGate unit instead of the address of an interface.
WAN optimization tunnels
All optimized traffic passes between the FortiGate units or between a FortiClient peer and a FortiGate unit over a WAN optimization tunnel. Traffic in the tunnel can be sent in plain text or encrypted using AES‑128bit‑CBC SSL.
WAN optimization tunnels
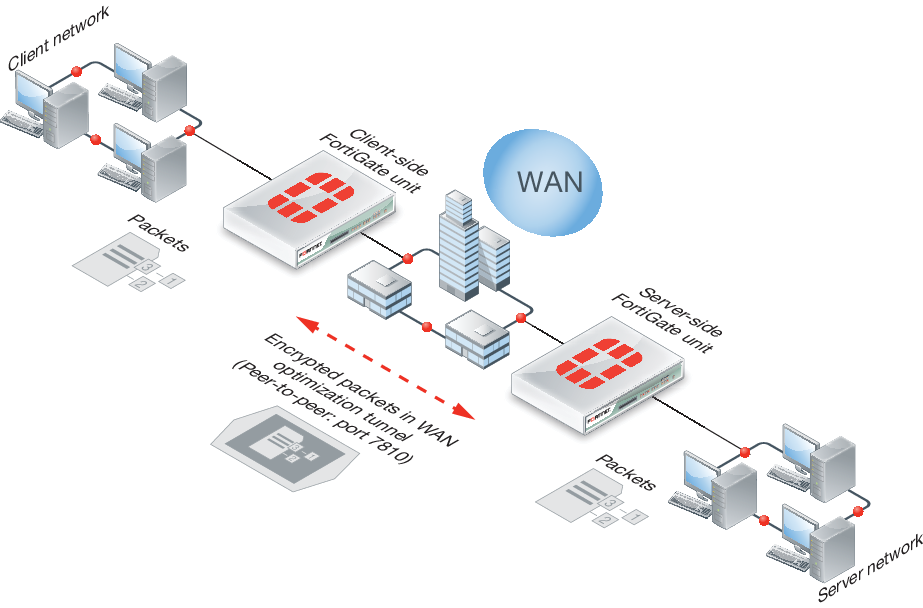
Both plain text and the encrypted tunnels use TCP destination port 7810.
Before a tunnel can be started, the peers must be configured to authenticate with each other. Then, the client-side peer attempts to start a WAN optimization tunnel with the server-side peer. Once the peers authenticate with each other, they bring up the tunnel and WAN optimization communication over the tunnel starts. After a tunnel has been established, multiple WAN optimization sessions can start and stop between peers without restarting the tunnel.
Tunnel sharing
You can use the tunnel-sharing WAN optimization profile CLI keyword to configure tunnel sharing for WAN optimization rules. Tunnel sharing means multiple WAN optimization sessions share the same tunnel. Tunnel sharing can improve performance by reducing the number of WAN optimization tunnels between FortiGate units. Having fewer tunnels means less data to manage. Also, tunnel setup requires more than one exchange of information between the ends of the tunnel. Once the tunnel is set up, each new session that shares the tunnel avoids tunnel setup delays.
Tunnel sharing also uses bandwidth more efficiently by reducing the chances that small packets will be sent down the tunnel. Processing small packets reduces network throughput, so reducing the number of small packets improves performance. A shared tunnel can combine all the data from the sessions being processed by the tunnel and send the data together. For example, suppose a FortiGate unit is processing five WAN optimization sessions and each session has 100 bytes to send. If these sessions use a shared tunnel, WAN optimization combines the packets from all five sessions into one 500-byte packet. If each session uses its own private tunnel, five 100-byte packets will be sent instead. Each packet also requires a TCP ACK reply. The combined packet in the shared tunnel requires one TCP ACK packet. The separate packets in the private tunnels require five.
Use the following command to configure tunnel sharing for HTTP traffic in a WAN optimization profile.
config wanopt profile
edit default
config http
set tunnel-sharing {express-shared | private | shared}
end
Tunnel sharing is not always recommended and may not always be the best practice. Aggressive and non-aggressive protocols should not share the same tunnel. An aggressive protocol can be defined as a protocol that is able to get more bandwidth than a non-aggressive protocol. (The aggressive protocols can “starve” the non-aggressive protocols.) HTTP and FTP are considered aggressive protocols. If aggressive and non-aggressive protocols share the same tunnel, the aggressive protocols may take all of the available bandwidth. As a result, the performance of less aggressive protocols could be reduced. To avoid this problem, rules for HTTP and FTP traffic should have their own tunnel. To do this, set tunnel-sharing to private for WAN optimization rules that accept HTTP or FTP traffic.
It is also useful to set tunnel-sharing to express-shared for applications, such as Telnet, that are very interactive but not aggressive. Express sharing optimizes tunnel sharing for Telnet and other interactive applications where latency or delays would seriously affect the user’s experience with the protocol.
Set tunnel-sharing to shared for applications that are not aggressive and are not sensitive to latency or delays. WAN optimization rules set to sharing and express-shared can share the same tunnel.
WAN optimization and user and device identity policies, load balancing and traffic shaping
Please note the following about WAN optimization and firewall policies:
- WAN optimization is not compatible with firewall load balancing.
- WAN optimization is compatible with source and destination NAT options in firewall policies (including firewall virtual IPs). If a virtual IP is added to a policy the traffic that exits the WAN optimization tunnel has its destination address changed to the virtual IPs mapped to IP address and port.
- WAN optimization is compatible with user identity-based and device identity security policies. If a session is allowed after authentication or device identification the session can be optimized.
Traffic shaping
Traffic shaping works for WAN optimization traffic that is not in a WAN optimization tunnel. So traffic accepted by a WAN optimization security policy on a client-side FortiGate unit can be shaped on ingress. However, when the traffic enters the WAN optimization tunnel, traffic shaping is not applied.
In manual mode:
- Traffic shaping works as expected on the client-side FortiGate unit.
- Traffic shaping cannot be applied to traffic on the server-side FortiGate unit.
In active-passive mode:
- Traffic shaping works as expected on the client-side FortiGate unit.
- If transparent mode is enabled in the WAN optimization profile, traffic shaping also works as expected on the server-side FortiGate unit.
- If transparent mode is not enabled, traffic shaping works partially on the server-side FortiGate unit.
WAN optimization and HA
You can configure WAN optimization on a FortiGate HA cluster. The recommended best practice HA configuration for WAN optimization is active-passive mode. When the cluster is operating, all WAN optimization sessions are processed by the primary unit only. Even if the cluster is operating in active-active mode, HA does not load-balance WAN optimization sessions.
You can also form a WAN optimization tunnel between a cluster and a standalone FortiGate unit or between two clusters.
In a cluster, only the primary unit stores the byte cache database. This database is not synchronized to the subordinate units. So, after a failover, the new primary unit must rebuild its byte cache. Rebuilding the byte cache can happen relatively quickly because the new primary unit gets byte cache data from the other FortiGate unit that it is participating with in WAN optimization tunnels.
WAN optimization, web caching and memory usage
To accelerate and optimize disk access and to provide better throughput and less latency FortiOS WAN optimization uses provisioned memory to reduce disk I/O and increase disk I/O efficiency. In addition, WAN optimization requires a small amount of additional memory per session for comprehensive flow control logic and efficient traffic forwarding.
When WAN optimization is enabled you will see a reduction in available memory. The reduction increases when more WAN optimization sessions are being processed. If you are thinking of enabling WAN optimization on an operating FortiGate unit, make sure its memory usage is not maxed out during high traffic periods.
In addition to using the system dashboard to see the current memory usage you can use the get test wad 2 command to see how much memory is currently being used by WAN optimization. See "get test {wad | wccpd} <test_level>" for more information.
Monitoring WAN optimization performance
Using WAN optimization monitoring, you can confirm that a FortiGate unit is optimizing traffic and view estimates of the amount of bandwidth saved. The WAN optimization monitor presents collected log information in a graphical format to show network traffic summary and bandwidth optimization information.
To view the WAN optimization monitor, go to WAN Opt. & Cache > Monitor > WAN Opt Monitor.
WAN optimization monitor
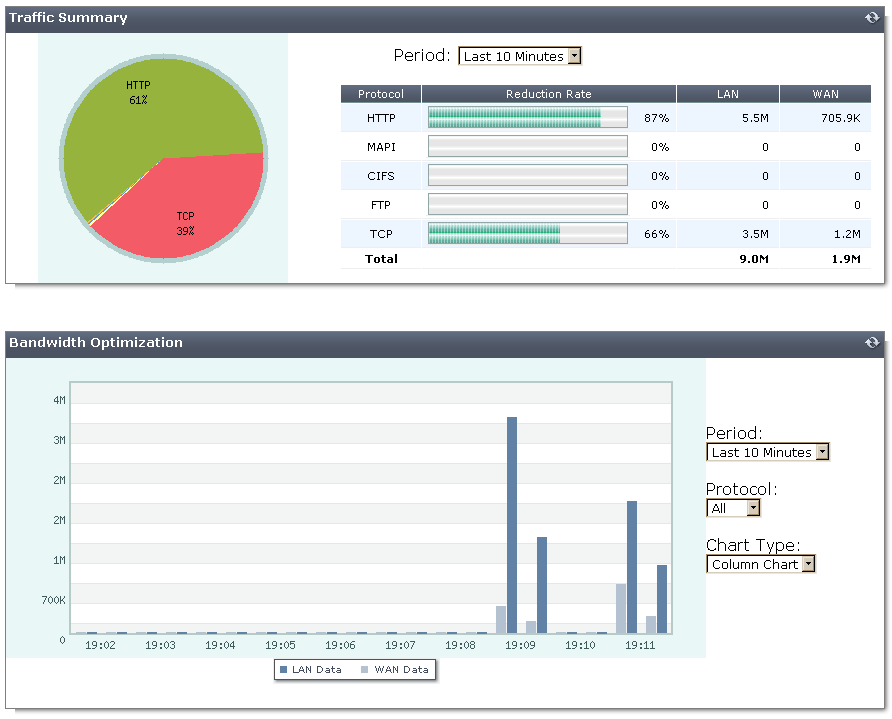
Traffic Summary
The traffic summary shows how WAN optimization is reducing the amount of traffic on the WAN for each WAN optimization protocol by showing the traffic reduction rate as a percentage of the total traffic. The traffic summary also shows the amount of WAN and LAN traffic. If WAN optimization is being effective the amount of WAN traffic should be lower than the amount of LAN traffic.
You can use the refresh icon to update the traffic summary display at any time. You can also set the amount of time for which the traffic summary shows data. The time period can vary from the last 10 minutes to the last month.
Bandwidth Optimization
This section shows network bandwidth optimization per time period. A line or column chart compares an application’s pre-optimized size (LAN data) with its optimized size (WAN data). You can select the chart type, the monitoring time period, and the protocol for which to display data. If WAN optimization is being effective the WAN bandwidth should be lower than the LAN bandwidth.
WAN optimization configuration summary
This section includes a client-side and a server-side WAN Optimization configuration summary.:
Client-side configuration summary
WAN optimization profile
Enter the following command to view WAN optimization profile CLI options:
tree wanopt profile
-- [profile] --*name (36)
|- transparent
|- comments
|- auth-group (36)
|- <http> -- status
|- secure-tunnel
|- byte-caching
|- prefer-chunking
|- tunnel-sharing
|- log-traffic
|- port (1,65535)
|- ssl
|- ssl-port (1,65535)
|- unknown-http-version
+- tunnel-non-http
|- <cifs> -- status
|- secure-tunnel
|- byte-caching
|- prefer-chunking
|- tunnel-sharing
|- log-traffic
+- port (1,65535)
|- <mapi> -- status
|- secure-tunnel
|- byte-caching
|- tunnel-sharing
|- log-traffic
+- port (1,65535)
|- <ftp> -- status
|- secure-tunnel
|- byte-caching
|- prefer-chunking
|- tunnel-sharing
|- log-traffic
+- port (1,65535)
+- <tcp> -- status
|- secure-tunnel
|- byte-caching
|- byte-caching-opt
|- tunnel-sharing
|- log-traffic
|- port
|- ssl
+- ssl-port (1,65535)
Local host ID and peer settings
config wanopt settings
set host-id client
end
config wanopt peer
edit server
set ip 10.10.2.82
end
Security policies
Two client-side WAN optimization security policy configurations are possible. One for active-passive WAN optimization and one for manual WAN optimization.
Active/passive mode on the client-side
config firewall policy
edit 2
set srcintf internal
set dstintf wan1
set srcaddr all
set dstaddr all
set action accept
set schedule always
set service ALL
set wanopt enable <<< enable WAN optimization
set wanopt-detection active <<< set the mode to active/passive
set wanopt-profile "default" <<< select the wanopt profile
next
end
Manual mode on the client-side
config firewall policy
edit 2
set srcintf internal
set dstintf wan1
set srcaddr all
set dstaddr all
set action accept
set schedule always
set service ALL
set wanopt enable <<< enable WAN optimization
set wanopt-detection off <<< sets the mode to manual
set wanopt-profile "default" <<< select the wanopt profile
set wanopt-peer "server" <<< set the only peer to do wanopt
with (required for manual mode)
next
end
server-side configuration summary
Local host ID and peer settings
config wanopt settings
set host-id server
end
config wanopt peer
edit client
set ip 10.10.2.81
end
Security policies
Two server-side WAN optimization security policy configurations are possible. One for active-passive WAN optimization and one for manual WAN optimization.
Active/passive mode on server-side
config firewall policy
edit 2 <<< the passive mode policy
set srcintf wan1
set dstintf internal
set srcaddr all
set dstaddr all
set action accept
set schedule always
set service ALL
set wanopt enable
set wanopt-detection passive
set wanopt-passive-opt transparent
end
config firewall explicit-proxy-policy
edit 3 <<< policy that accepts wanopt tunnel connections from the server
set proxy wanopt <<< wanopt proxy type
set dstintf internal
set srcaddr all
set dstaddr server-subnet
set action accept
set schedule always
set service ALL
next
end
Manual mode on server-side
config firewall explicit-proxy-policy
edit 3 <<< policy that accepts wanopt tunnel connections from the client
set proxy wanopt <<< wanopt proxy type
set dstintf internal
set srcaddr all
set dstaddr server-subnet
set action accept
set schedule always
set service ALL
next
end
Best practices
This is a short list of WAN optimization and explicit proxy best practices.
- WAN optimization tunnel sharing is recommended for similar types of WAN optimization traffic. However, tunnel sharing for different types of traffic is not recommended. For example, aggressive and non-aggressive protocols should not share the same tunnel. See Tunnel sharing.
- Active-passive HA is the recommended HA configuration for WAN optimization. See WAN optimization and HA.
- Configure WAN optimization authentication with specific peers. Accepting any peer is not recommended as this can be less secure. SeeAccepting any peers.
- Set the explicit proxy Default Firewall Policy Action to Deny. This means that a security policy is required to use the explicit web proxy. See The FortiGate explicit web proxy.
- Set the explicit FTP proxy Default Firewall Policy Action to Deny. This means that a security policy is required to use the explicit FTP proxy. See General explicit FTP proxy configuration steps.
- Do not enable the explicit web or FTP proxy on an interface connected to the Internet. This is a security risk because anyone on the Internet who finds the proxy could use it to hide their source address. If you must enable the proxy on such an interface make sure authentication is required to use the proxy. See General explicit web proxy configuration steps.

