5. Click Create New and configure the settings. The settings you select determine which additional settings are displayed: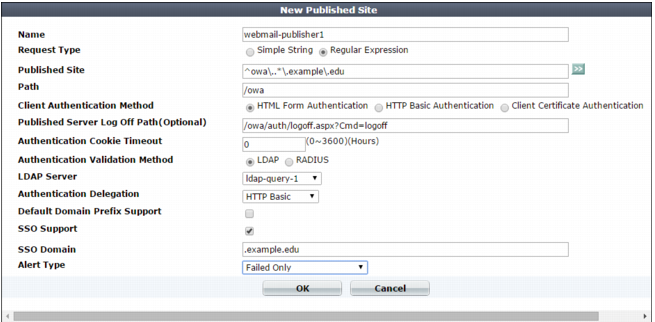


Setting name | Description |
Name | Type a unique name that can be referenced in other parts of the configuration, such as cms-publisher1. Do not use spaces or special characters. The maximum length is 35 characters. |
Request Type | Select one of the following options: • Regular Expression — Published Site contains a regular expression designed to match multiple host names or FQDNs. |
Published Site | Enter one of the following: • The literal Host: name, such as sharepoint.example.com, that the HTTP requests that match the rule contain (if Request Type is Simple String) • A regular expression, such as ^*\.example\.edu, that matches all and only the host names that the rule should match (if Request Type is Regular Expression). The maximum length is 255 characters. Note: Regular expressions beginning with an exclamation point ( ! ) are not supported. For information on language and regular expression matching, see “Regular expression syntax”. |
Path | Enter the URL of the request for the web application, such as /owa. It must begin with a forward slash ( / ). |
Client Authentication Method | Select one of the following options: • HTML Form Authentication — FortiWeb authenticates clients by presenting an HTML web page with an authentication form. • HTML Basic Authentication — FortiWeb authenticates clients by providing an HTTP AUTH code so that the browser displays its own dialog. • Client Certificate Authentication — FortiWeb validates the HTTP client’s personal certificate using the certificate verifier specified in the associated server policy or server pool configuration. Note: This option requires you to select a value for Certificate Verification in the server policy or Certificate Verification in the server pool configuration. |
Published Server Log Off Path | Optionally, type the URL of the request that a client sends to log out of the application. Examples: /owa/auth/logoff.aspx /owa/logoff.owa When clients log out of the web application, FortiWeb redirects them to its authentication dialog. Available only when Client Authentication Method is HTML Form Authentication. |
Authentication Cookie Timeout | Specify the length of time that passes before the cookie that the site publish rule adds expires and the client must re-authenticate. Valid values are from 0 to 3600 hours. To configure the cookie with no expiration, specify 0 (the default). The browser only deletes the cookie when the user closes all browser windows. |
Authentication Validation Method | Select whether FortiWeb uses LDAP or RADIUS to authenticate clients. Available only when Client Authentication Method is HTML Form Authentication or HTML Basic Authentication. |
LDAP Server or RADIUS Server | Select the name of the authentication query that FortiWeb uses to pass credentials to your authentication server. Available only when Client Authentication Method is HTML Form Authentication or HTML Basic Authentication. |
RSA SecurID | Select to enable client authentication using a username and a RSA SecurID authentication code only. Users are not required to enter a password. When this option is enabled, the authentication delegation options in the site publish rule are not available. For more information, see “RSA SecurID authentication”. Alternatively, you can use the default two-factor authentication feature to require users to enter a username, password, and a RSA SecurID authentication code. For more information, see “Two-factor authentication”. Available only when Client Authentication Method is HTML Form Authentication and Authentication Validation Method is RADIUS. |
Authentication Delegation | Select one of the following options: • HTTP Basic — FortiWeb uses HTTP Authorization: headers with Base64 encoding to forward the client’s credentials to the web application. Typically, you select this option when the web application supports HTTP protocol-based authentication. Available only when Client Authentication Method is HTML Form Authentication or HTML Basic Authentication. • Kerberos — After it authenticates the client via the HTTP form or HTTP basic method, FortiWeb obtains a Kerberos service ticket for the specified web application on behalf of the client. It adds the ticket to the HTTP Authorization: header of the client request with Base64 encoding. Available only when Client Authentication Method is HTML Form Authentication or HTML Basic Authentication. • Kerberos Constrained Authentication — After it authenticates the client’s certificate, FortiWeb obtains a Kerberos service ticket for the specified web application on behalf of the client. It adds the ticket to the HTTP Authorization: header of the client request with Base64 encoding. Available only when Client Authentication Method is Client Certificate Authentication. • No Delegation — FortiWeb does not send the client’s credentials to the web application. Select this option when the web application has no authentication of its own or uses HTML form-based authentication. Note: If the web application uses HTML form-based authentication, the client is required to authenticate twice: once with FortiWeb and once with the web application’s form. To work with the Kerberos options, web applications require a specific Windows authentication configuration. See “Configuring Windows Authentication for Kerberos authentication delegation” Not available when RSA SecurID is selected. |
Username Location in Certificate | Use one of the following options to specify how FortiWeb determines the client username: • SAN - UPN — Using the certificate’s subjectAltName (Subject Alternative Name or SAN) and User Principal Name (UPN) values. These values that contain the username in certificates issued in a Windows environment. For example: username@domain • SAN - Email — Using the certificate’s subjectAltName (Subject Alternative Name or SAN) and the email address value in the certificate’s Subject information. • Subject - Email — Using the email address value in the certificate’s Subject information. Note: Because the email value can be an alias rather than the real DC (domain controller) domain, the most reliable method for determining the username is SAN - UPN. Available only when Authentication Delegation is Kerberos Constrained Delegation. |
Delegated HTTP Service Principal Name | Specify the Service Principal Name (SPN) for the web application that clients access using this site publish rule. A service principal name uses the following format: <service_type >/<instance_name>:<port_number>/ <service_name> For example, for an Exchange server that belongs to the domain dc1.com and has the hostname USER-U3LOJFPLH1, the SPN is http/USER-U3LOJFPLH1.dc1.com@DC1.COM. For a FortiWeb site publishing configuration, a valid SPN requires the suffix @<domain> (for example, @DC1.COM). For instructions that include how to obtain SPN information, see “To create an Active Directory (AD) user for FortiWeb”. |
Keytab File | Select the keytab file configuration for the AD user that FortiWeb uses to obtain Kerberos service tickets for clients. To add a keytab configuration, go to Application Delivery > Site Publish > Keytab File. Available only when Authentication Delegation is Kerberos Constrained Delegation. |
Service Principal Name for Keytab File | Specify the Service Principal Name (SPN) of the AD user that is a delegator. It is the SPN that you used to generate the keytab specified by Keytab File. (See “To create an Active Directory (AD) user for FortiWeb”.) For example, host/forti-delegator.dc1.com@DC1.COM. For a FortiWeb site publishing configuration, a valid SPN requires the suffix @<domain> (for example, @DC1.COM). Available only when Authentication Delegation is Kerberos Constrained Delegation. |
Default Domain Prefix Support | Select to allow users in environments that require users to log in using both a domain and username to log in with just a username. Also specify Default Domain Prefix. In some environments, the domain controller requires users to log in with the username format domain\username. For example, if the domain is example.com and the username is user1, the user enters EXAMPLE\user1. Alternatively, enable this option and enter EXAMPLE for Default Domain Prefix. The user enters user1 for the username value and FortiWeb automatically adds EXAMPLE\ to the HTTP Authorization: header before it forwards it to the web application. |
Default Domain Prefix | Enter a domain name that FortiWeb adds to the HTTP Authorization: header before it forwards it to the web application. Available only when Default Domain Prefix Support is enabled. When Authentication Delegation is Kerberos, ensure that the prefix you enter is the full domain name (for example, example.com). |
SSO Support | Enable for single sign-on support. For example, the web site for this rule is www1.example.com and SSO Domain is .example.com. After FortiWeb authenticates the client for www1.example.com, the client can access www2.example.com without authenticating a second time. Site publishing SSO sessions exist on FortiWeb only; they are not synchronized to the authentication or accounting server. Therefore, SSO is not shared with non-web applications. For SSO with other protocols, see the documentation for your FortiGate or other firewall. |
SSO Domain | Type the domain suffix of Host: names that can share this rule’s authentication sessions, such as .example.com. Include the period ( . ) that precedes the host’s name. |
Alert Type | Select whether to log authentication failures, successes, or both: • None — Do not generate an alert email or log message. • Failed Only — Only authentication failures generate alert email and log messages. • Successful Only — Only successful authentication generates alert email or log messages. • All — All HTTP authentication attempts, regardless of success or failure, generate alert email, log messages, or both. Event log messages contain the user name, authentication type, success or failure, and source address (for example, User jdoe [Site Publish] login successful from 172.0.2.5) when an end-user successfully authenticates. A similar message is recorded if the authentication fails (for example, User hackers [Site Publish] login failed from 172.0.2.5). |