Using Kerberos authentication delegation
You can configure FortiWeb to use the Kerberos protocol for authentication delegation. Kerberos authentication uses tickets that are encrypted and decrypted by secret keys and do not contain user passwords. FortiWeb uses Kerberos to give clients it has already authenticated access to web applications, not for the initial authentication.
Types of Kerberos authentication delegation
FortiWeb’s site publish feature supports two different types of Kerberos authentication delegation. The type you use depends on the client authentication method that you specify:
• Regular Kerberos delegation — Users enter a user name and password in an HTML authentication form (the HTML Form Authentication or HTTP Basic Authentication site publish rule options). FortiWeb then obtains a Kerberos service ticket on behalf of the client to allow it to access the specified web application.
• Kerberos constrained delegation — FortiWeb verifies a user’s SSL certificate using the certificate authority specified in a server policy or server pool member configuration (Client Certificate Authentication). FortiWeb then obtains a Kerberos service ticket on behalf of the client to allow it to access the specified web application.
This authentication delegation configuration requires you to create an Active Directory user for FortiWeb that can act on behalf of the web application (see
“To create an Active Directory (AD) user for FortiWeb”).
For information on the site publish rules settings related to Kerberos, see
“Offloaded authentication and optional SSO configuration”.
Configuring Windows Authentication for Kerberos authentication delegation
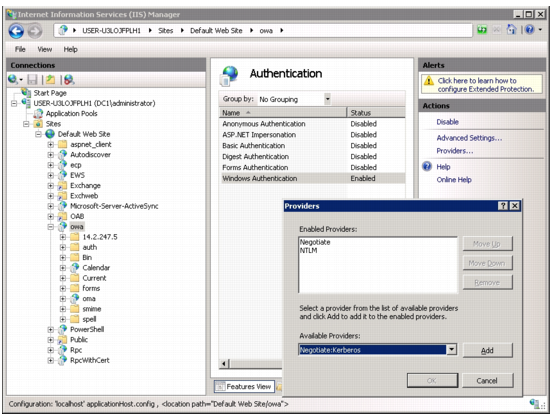
For both types of Kerberos authentication delegation, ensure that Windows Authentication is enabled for the web application and that is uses one of the following provider configurations. (You specify a provider using the Windows Authentication advanced settings):
• Negotiate and NTLM (the default values; Negotiate includes Kerberos)
• Negotiate: Kerberos (remove Negotiate and NTLM)
When the web application is Microsoft Exchange Outlook Web App (OWA), ensure Integrated Windows authentication is also enabled.
To access the Integrated Windows authentication setting:
1. In the Exchange Management Console, in the virtual directory you want to configure, under Server Configuration, select Client Access.
2. Select the server that hosts the OWA virtual directory, and then click the Outlook Web App tab.
3. In the work pane, select the virtual directory that you want to configure, and then click Properties.
See also
 in IIS Manager
in IIS Manager in IIS Manager
in IIS Manager in IIS Manager
in IIS Manager Configure Integrated Windows authentication for OWA
Configure Integrated Windows authentication for OWA