4. Configure these settings: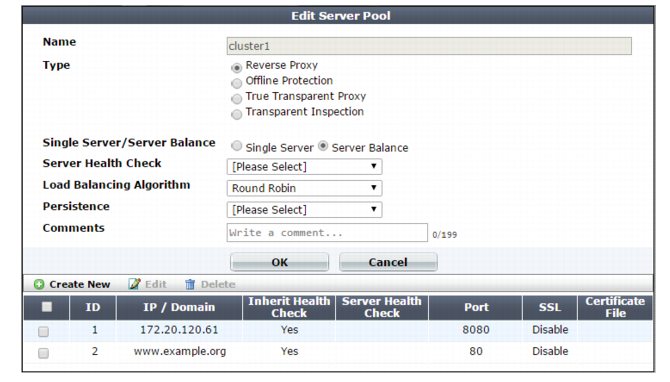


Setting name | Description |
Name | Type a name that can be referenced by other parts of the configuration. Do not use spaces or special characters. The maximum length is 63 characters. |
Type | Select the current operation mode of the appliance to display the corresponding pool options. For full information on the operating modes, see “How to choose the operation mode”. |
Single Server/Server Balance | • Single Server — Specifies a pool that contains a single member. • Server Balance — Specifies a pool that contains multiple members. FortiWeb uses the specified load-balancing algorithm to distribute TCP connections among the members. If a member is unresponsive to the specified server health check, FortiWeb forwards subsequent connections to another member of the pool. Available only when Type is Reverse Proxy. |
Server Health Check | Specifies a test for server availability. By default, this health check is used for all pool members, but you can use the pool member configuration to assign a different health check to a member. For more information, see “Configuring server up/down checks” Available only when Type is Reverse Proxy and Single Server/Server Balance is Server Balance. |
Load Balancing Algorithm | • Round Robin — Distributes new TCP connections to the next pool member, regardless of weight, response time, traffic load, or number of existing connections. FortiWeb avoids unresponsive servers. • Weighted Round Robin — Distributes new TCP connections using the round-robin method, except that members with a higher weight value receive a larger percentage of connections. • Least Connection — Distributes new TCP connections to the member with the fewest number of existing, fully-formed TCP connections. Available only when Type is Reverse Proxy and Single Server/Server Balance is Server Balance. |
Persistence | Select a configuration that specifies a session persistence method and timeout to apply to the pool members. For more information, see “Configuring session persistence”. |
Comments | Type a description of the server pool. The maximum length is 63 characters. |
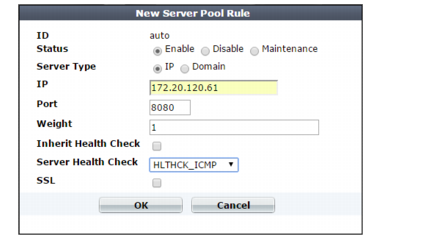
Setting name | Description |
ID | The index number of the member entry within the server pool. FortiWeb automatically assigns the next available index number. For round robin-style load-balancing, the index number indicates the order in which FortiWeb distributes connections. The valid range is from 0 to 65,535. You can use the server-policy server-pool CLI command to change the index number value. For more information, see the FortiWeb CLI Reference. |
Status | • Enable — Specifies that this pool member can receive new sessions from FortiWeb. • Disable — Specifies that this pool member does not receive new sessions from FortiWeb and FortiWeb closes any current sessions as soon as possible. • Maintenance — Specifies that this pool member does not receive new sessions from FortiWeb but FortiWeb maintains any current connections. |
Server Type | Select either IP or Domain to indicate how you want to define the pool member. |
IP or Domain | Specify the IP address or fully-qualified domain name of the web server to include in the pool. Tip: The IP or domain server is usually not the same as a protected host names group. See “Protected web servers vs. allowed/protected host names”. Warning: Server policies do not apply features that do not yet support IPv6 to servers specified using IPv6 addresses or domain servers whose DNS names resolve to IPv6 addresses. Tip: For domain servers, FortiWeb queries a DNS server to query and resolve each web server’s domain name to an IP address. For improved performance, do one of the following: • use physical servers instead • ensure highly reliable, low-latency service to a DNS server on your local network The Server Type value determines the name of this option. |
Port | Type the TCP port number where the pool member listens for connections. The valid range is from 1 to 65,535. |
Weight | If the pool member is part of a pool that uses the weighted round-robin load-balancing algorithm, type the weight of the member when FortiWeb distributes TCP connections. Members with a greater weight receive a greater proportion of connections. Weighting members can be useful when, for example, some servers in the pool are more powerful or if a member is already receiving fewer or more connections due to its role in multiple web sites. This field appears only if Type is Server Balance. |
Inherit Health Check | Clear to use the health check specified by the Server Health Check value in this server pool rule instead of the one specified in the server pool configuration. |
Server Health Check | Specifies an availability test for this pool member. For more information, see “Configuring server up/down checks”. |
SSL | For reverse proxy, offline protection, and transparent inspection modes, enable to use SSL/TLS for connections between FortiWeb and the pool member. For true transparent proxy, enable to both offload SSL/TLS processing to FortiWeb and use SSL/TLS for connections between FortiWeb and the pool member. For offline protection and transparent inspection modes, also configure Certificate File. FortiWeb uses the certificate to decrypt and scan connections before passing the encrypted traffic through to the pool members (SSL inspection). Note: Ephemeral (temporary key) Diffie-Hellman exchanges are not supported if the FortiWeb appliance is operating in transparent inspection or offline protection mode. For true transparent proxy, also configure Certificate File, Client Certificate, and the settings described in step 8. FortiWeb handles SSL negotiations and encryption and decryption, instead of the pool member (SSL offloading). (For reverse proxy mode, you can configure SSL offloading for all members of a pool using a server policy. See “Configuring a server policy”.) Note: When this option is enabled, the pool member must be configured to apply SSL. |
Certificate File | Do one of the following: • Select the server certificate that FortiWeb uses to decrypt SSL-secured connections. • Select Create New to open a window that allows you to upload a new certificate. For more information, see “Uploading a server certificate”. For true transparent proxy operating mode, also complete the settings described in described in step 8. Available when: • SSL is enabled, and • FortiWeb is operating in a mode other than reverse proxy, that performs SSL inspection. See “Offloading vs. inspection”. |
Client Certificate | If connections to this pool member require a valid client certificate, select the client certificate that FortiWeb uses. Available when: • SSL is enabled, and • FortiWeb is operating in reverse proxy or true transparent proxy mode. Upload a client certificate for FortiWeb using the steps you use to upload a server certificate. See “Uploading a server certificate”. |
Setting name | Description |
Certificate Intermediate Group | Select the name of a group of intermediate certificate authority (CA) certificates, if any, that FortiWeb presents to clients. An intermediate CA can complete the signing chain and validate the server certificate’s CA signature. Configure this option when clients receive certificate warnings that an intermediary CA has signed the server certificate specified by Certificate File, not a root CA or other CA currently trusted by the client directly. Alternatively, you can include the entire signing chain in the server certificate itself before you upload it to FortiWeb. See “Uploading a server certificate” and “Supplementing a server certificate with its signing chain”. |
Show/Hide advanced SSL settings | Click to show or hide the settings that allow you to specify a Server Name Indication (SNI) configuration, increase security by disabling specific versions of TLS and SSL for this pool member, and other advanced SSL settings. For example, if FortiWeb can use a single certificate to decrypt and encrypt traffic for all the web sites that reside on the pool member, you may not have to set any advanced SSL settings. For more information, see the descriptions of the individual settings. |
Add HSTS Header | Enable to combat MITM attacks on HTTP by injecting the RFC 6797 strict transport security header into the reply, such as: Strict-Transport-Security: max-age=31536000; includeSubDomains This header forces clients to use HTTPS for subsequent visits to this domain. If the certificate is invalid, the client’s web browser receives a fatal connection error and does not display a dialog that allows the user to override the certificate mismatch error and continue. |
Certificate Verification | Select the name of a certificate verifier, if any, that FortiWeb uses to validate an HTTP client’s personal certificate. However, if you select Enable Server Name Indication (SNI) and the domain in the client request matches an entry in the specified SNI policy, FortiWeb uses the SNI configuration to determine which certificate verifier to use. If you do not select a verifier, clients are not required to present a personal certificate. See also “How to apply PKI client authentication (personal certificates)”. Personal certificates, sometimes also called user certificates, establish the identity of the person connecting to the web site (PKI authentication). You can require that clients present a certificate instead of, or in addition to, HTTP authentication (see “Offloading HTTP authentication & authorization”). Note: The client must support SSL 3.0, TLS 1.0, TLS 1.1, or TLS 1.2. When the operating mode is reverse proxy, you can select this option in the server policy. |
Enable URL Based Client Certificate | Specifies whether FortiWeb uses a URL-based client certificate group to determine whether a client is required to present a personal certificate. |
URL Based Client Certificate Group | Specifies the URL-based client certificate group that determines whether a client is required to present a personal certificate. If the URL the client requests does not match an entry in the group, the client is not required to present a personal certificate. For information on creating a group, see “Use URLs to determine whether a client is required to present a certificate”. |
Max HTTP Request Length | Specifies the maximum allowed length for an HTTP request with a URL that matches an entry in the URL-based client certificate group. FortiWeb blocks any matching requests that exceed the specified size. This setting prevents a request from exceeding the maximum buffer size. |
Client Certificate Forwarding | Enable to configure FortiWeb to include the X.509 personal certificate presented by the client during the SSL/TLS handshake, if any, in an X‑Client‑Cert: HTTP header when it forwards the traffic to the protected web server. FortiWeb still validates the client certificate itself, but this forwarding action can be useful if the web server requires the client certificate for the purpose of server-side identity-based functionality. |
Enable Server Name Indication (SNI) | Select to use a Server Name Indication (SNI) configuration instead of or in addition to the server certificate specified by Certificate File. The SNI configuration enables FortiWeb to determine which certificate to present on behalf of the pool member based on the domain in the client request. See “Allowing FortiWeb to support multiple server certificates”. If you specify both an SNI configuration and Certificate File, FortiWeb uses the certificate specified by Certificate File when the domain in the client request does not match a value in the SNI configuration. If you select Enable Strict SNI, FortiWeb always ignores the value of Certificate File. |
Enable Strict SNI | Select to configure FortiWeb to ignore the value of Certificate File when it determines which certificate to present on behalf of the pool member, even if the domain in a client request does not match a value in the SNI configuration. Available only if Enable Server Name Indication (SNI) is selected. |
SNI Policy | Select the Server Name Indication (SNI) configuration that FortiWeb uses to determine which certificate it presents on behalf of this pool member. Available only if Enable Server Name Indication (SNI) is enabled. |
SSL Protocols | Specify which versions of the SSL or TLS cryptographic protocols clients can use to connect securely to this pool member. For more information, see “Supported cipher suites & protocol versions”. |
SSL/TLS encryption level | Specify whether the set of cipher suites that FortiWeb allows creates a medium-security or high-security configuration. For more information, see “Supported cipher suites & protocol versions”. |
Enable Perfect Forward Secrecy | Enable to configure FortiWeb to generate a new public-private key pair when it establishes a secure session with a Diffie–Hellman key exchange. Perfect forward secrecy (PFS) improves security by ensuring that the key pair for a current session is unrelated to the key for any future sessions. |
Prioritize RC4 Cipher Suite | Enable to configure FortiWeb to use the RC4 cipher when it first attempts to create a secure connection with a client. This option protects against a BEAST (Browser Exploit Against SSL/TLS) attack, a TLS 1.0 vulnerability. |
Disable Client-Initiated SSL Renegotiation | Select to ignore requests from clients to renegotiate TLS or SSL. This setting protects against denial-of-service (DoS) attacks that use TLS/SSL renegotiation to overburden the server. |