Uploading a server certificate
You also use this process to upload a client certificate for FortiWeb. You add this certificate to a server pool configuration if connections to a pool member require a valid client certificate (see
“Creating a server pool”).
You can import (upload) either:
• Base64-encoded
• PKCS #12 RSA-encrypted
X.509 server certificates and private keys to the FortiWeb appliance.
If a server certificate is signed by an intermediate certificate authority (CA) rather than a root CA, before clients will trust the server certificate, you must demonstrate a link with root CAs that the clients trust, thereby proving that the server certificate is genuine. You can demonstrate this chain of trust either by:
• Appending a signing chain in the server certificate.
• Installing each intermediary CA’s certificate in clients’ trust store (list of trusted CAs).
Which method is best for you often depends on whether you have a convenient method for deploying CA certificates to clients, such as you may be able to for clients in an internal Microsoft Active Directory domain, and whether you often refresh the server certificate.
To append a signing chain in the certificate itself, before uploading the server certificate to the FortiWeb appliance
1. Open the certificate file in a plain text editor.
2. Append the certificate of each intermediary CA in order from the intermediary CA who signed the local certificate to the intermediary CA whose certificate was signed directly by a trusted root CA.
For example, a server’s certificate that includes a signing chain might use the following structure:
-----BEGIN CERTIFICATE-----
<server certificate>
-----END CERTIFICATE-----
-----BEGIN CERTIFICATE-----
<certificate of intermediate CA 1, who signed the server certificate>
-----END CERTIFICATE-----
-----BEGIN CERTIFICATE-----
<certificate of intermediate CA 2, who signed the certificate of intermediate CA 1 and whose certificate was signed by a trusted root CA>
-----END CERTIFICATE-----
3. Save the certificate.
To upload a certificate
1. Go to System > Certificates > Local.
To access this part of the web UI, your administrator's account access profile must have
Read and
Write permission to items in the
Admin Users category. For details, see
“Permissions”.
2. Click Import.
A dialog appears.
3. Configure these settings:
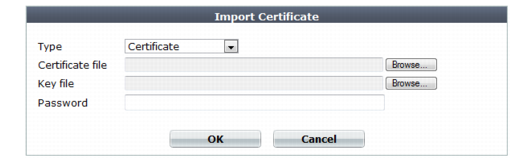
Setting name | Description |
Type | Select the type of certificate file to upload, either: • Local Certificate — An unencrypted certificate in PEM format. • Certificate — An unencrypted certificate in PEM format. The key is in a separate file. • PKCS12 Certificate — A PKCS #12 encrypted certificate with key. Other fields may appear depending on your selection. |
Certificate file | Click Browse to locate the certificate file that you want to upload. This option is available only if Type is Certificate or Local Certificate. |
Key file | Click Browse to locate the key file that you want to upload with the certificate. This option is available only if Type is Certificate. |
Certificate with key file | Click Browse to locate the PKCS #12 certificate-with-key file that you want to upload. This option is available only if Type is PKCS12 Certificate. |
Password | Type the password that was used to encrypt the file, enabling the FortiWeb appliance to decrypt and install the certificate. This option is available only if Type is Certificate or PKCS12 Certificate. |
4. Click OK.
See also


