Table 39: System > Certificates > Local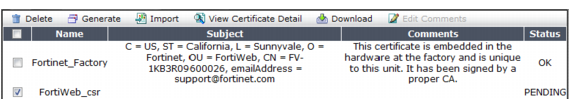

The FortiWeb appliance’s default certificate does not appear in the list of locally stored certificates. It is used only for connections to the web UI and cannot be removed. |

Button/field | Description |
Generate | Click to generate a certificate signing request. For details, see “Generating a certificate signing request”. |
Import | Click to upload a certificate. For details, see “Uploading a server certificate”. |
View Certificate Detail | Click to view the selected certificate’s subject, range of dates within which the certificate is valid, version number, serial number, and extensions. |
Download | Click to download the selected CSR’s entry in certificate signing request (.csr) file format. This button is disabled unless the currently selected file is a CSR. |
Edit Comments | Click to add or modify the comment associated with the selected certificate. |
(No label. Check box in column heading.) | Click to mark all check boxes in the column, selecting all entries. To select an individual entry, instead, mark the check box in the entry’s row. |
Name | Displays the name of the certificate. |
Subject | Displays the distinguished name (DN) located in the Subject: field of the certificate. If the row contains a certificate request which has not yet been signed, this field is empty. |
Comments | Displays the description of the certificate, if any. Click the Edit Comments icon to add or modify the comment associated with the certificate or certificate signing request. |
Status | Displays the status of the certificate. • OK — Indicates that the certificate was successfully imported. To use the certificate, select it in a server policy or server pool configuration. • PENDING — Indicates that the certificate request has been generated, but must be downloaded, signed, and imported before it can be used as a server certificate. |