4. Configure these settings: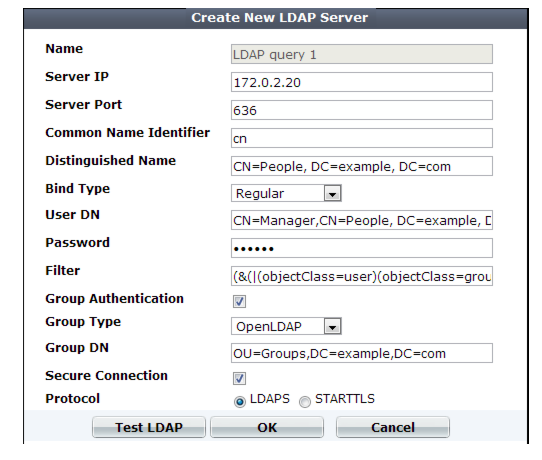

If you use an LDAP query for administrators, separate it from the queries for regular users. Do not combine administrator and user queries into a single entry. Failure to separate queries will allow end-users to have administrative access the FortiWeb web UI and CLI. If administrators are in the same directory but belong to a different group than end-users, you can use Group Authentication to exclude end-users from the administrator LDAP query. |

Setting name | Description |
Name | Type a unique name that can be referenced in other parts of the configuration. Do not use special characters. The maximum length is 35 characters. Note: This is the name of the query only, not the administrator or end-user’s account name/login. Administrator account names are defined in Administrator. |
Server IP | Type the IP address of the LDAP server. |
Server Port | Type the port number where the LDAP server listens. The default port number varies by your selection in Secure Connection: port 389 is typically used for non-secure connections or for STARTTLS-secured connections, and port 636 is typically used for SSL-secured (LDAPS) connections. |
Common Name Identifier | Type the identifier for the common name (CN) attribute (also called the CNID) whose value is the user name. Identifiers vary by your LDAP directory’s schema. This is often cn or uid. For Active Directory, it is often the attribute sAMAccountName. For example, in a default OpenLDAP directory, if a user object is: uid=hlee,cn=users,dc=example,dc=com then the CNID is uid. For an additional example for Active Directory, see “Example for a configuration for AD”. |
Distinguished Name | Specifies the Base DN from which the LDAP query starts. This DN is the full path in the directory to the user account objects. For example: ou=People,dc=example,dc=com or cn=users,dc=example,dc=com |
Bind Type | Select one of the following LDAP query binding styles: • Simple — Bind using the client-supplied password and a bind DN assembled from the Common Name Identifier, Distinguished Name, and the client-supplied user name. • Regular — Bind using a bind DN and password that you configure in User DN and Password. This also allows for group authentication. • Anonymous — Do not provide a bind DN or password. Instead, perform the query without authenticating. Select this option only if the LDAP directory supports anonymous queries. |
User DN | Type the bind DN of an LDAP user account with permissions to query the Distinguished Name. For example: cn=FortiWebA,dc=example,dc=com For Active Directory, the UPN (User Principle Name) is often used instead of a bind DN (for example, user@domain.com) The maximum length is 255 characters. This field can be optional if your LDAP server does not require the FortiWeb appliance to authenticate when performing queries. |
Password | Type the password of the User DN. This field may be optional if your LDAP server does not require the FortiWeb appliance to authenticate when performing queries, and does not appear if Bind Type is Anonymous or Simple. |
Filter | Type an LDAP query filter string that filters the query’s results based on any attribute in the record set. For example: (&(|(objectClass=user)(objectClass=group)(objectClass=publicFolder))) This filter improves the speed and efficiency of the queries. For syntax, see an LDAP query filter reference. If you do not want to exclude any accounts from the query, leave this setting blank. The maximum length is 255 characters. |
Group Authentication | Enable to filter the query results, only allowing users to authenticate if they are members of the LDAP group that you define in Group DN. Users that are not members of that group will not be allowed to authenticate. Also configure Group Type and Group DN. |
Group Type | Indicate the schema of your LDAP directory, either: • OpenLDAP — The directory uses a schema where each user object’s group membership is recorded in an attribute named gidNumber. This is usually an OpenLDAP directory, or another directory where the object class inetOrgPerson or posixAccount. • Windows-AD — The directory uses a schema where each user object’s group membership is recorded in an attribute named memberOf. This is usually a Microsoft Active Directory server. • eDirectory — The directory uses a schema where each user object’s group membership is recorded in an attribute named groupMembership. This is usually a Novell eDirectory server. Group membership attributes may have different names depending on an LDAP directory schemas. The FortiWeb appliance will use the group membership attribute that matches your directory’s schema when querying the group DN. This option appears only when Bind Type is Regular and Group Authentication is enabled. |
Group DN | Type the value of the group membership attribute that query results must have in order to be able to authenticate. The value may vary by your directory’s schema, but may be the distinguished name such as ou=Groups,dc=example,dc=com or a group ID (GID) such as 100. This option appears only when Bind Type is Regular and Group Authentication is enabled. The maximum length is 255 characters. |
Secure Connection | Enable to connect to the LDAP servers using an encrypted connection, then select the style of the encryption in Protocol. |
Protocol | Select which secure LDAP protocol to use, either • LDAPS • STARTTLS The option appears only when Secure Connection is enabled. |