4. Configure these settings: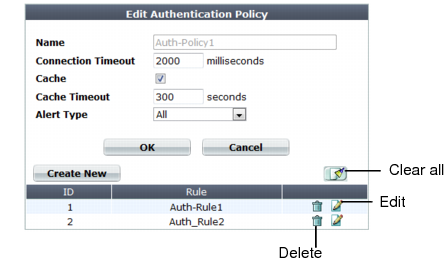

Alternatively or in addition to HTTP authentication, with SSL connections, you can require that clients present a valid personal certificate. For details, see “Certificate Verification”. |

Setting name | Description |
Name | Type a unique name that can be referenced in other parts of the configuration. Do not use spaces or special characters. The maximum length is 35 characters. |
Connection Timeout | Type the connection timeout for the query to the FortiWeb’s query to the remote authentication server in milliseconds. The default is 2,000 (2 seconds). If the authentication server does not answer queries quickly enough, to prevent dropped connections, increase this value. |
Cache | Enable if you want to cache authentication query results. Tip: This can improve performance, especially if the connection to the remote authentication server is slow or experiences latency. |
Alert Type | Select whether to log authentication failures and/or successes: • None — Do not generate an alert email and/or log message. • Failed Only — Alert email and/or log messages are caused only by HTTP authentication failures. • Successful Only — Alert email and/or log messages are caused only by successful HTTP authentication. • All — Alert email and/or log messages are caused for all HTTP authentication attempts, regardless of success or failure. Event log messages contain the user name, authentication type, success or failure, and source address (for example, User jdoe HTTP BASIC login successful from 172.20.120.46) when an end-user successfully authenticates. A similar message is recorded if the authentication fails (for example, User hackers HTTP BASIC login failed from 172.20.120.227). |
Setting name | Description |
Cache Timeout | Type the number of seconds that authentication query results will be cached. When a record’s timeout is reached, FortiWeb will remove it from the cache. Subsequent requests from the client will cause FortiWeb to query the authentication server again, adding the query results to the cache again. This setting is applicable only if Cache is enabled. The default value is 300. |
If you have enabled logging, you can also make reports such as “Top Failed Authentication Events By Day” and “Top Authentication Events By User” to identify hijacked accounts or slow brute force attacks. See “Reports”. |