A dialog appears.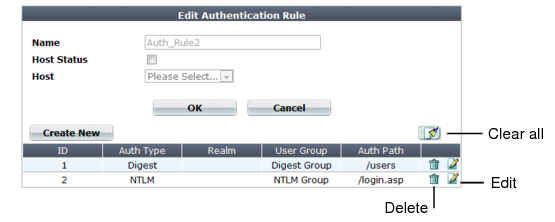

Alternatively, you can configure site publishing, which has the additional advantage of optionally providing SSO for multiple web applications. See “Single sign-on (SSO) (site publishing)”. |

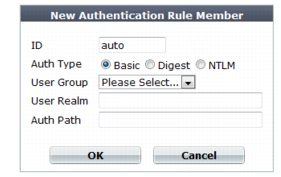
Setting name | Description |
Auth Type | Select which type of HTTP authentication to use: • Basic — Clear text, Base64-encoded user name and password. Supports all user queries except NTLM. NTLM users will be ignored if included in the user group. • Digest — Hashed user name, realm, and password. Only local users are supported. Other types are ignored if included in the user group. • NTLM — Encrypted user name and password. Only NTLM queries are supported. Other types are ignored if included in the user group. For more information on available user types, see “Grouping users”. |
User Group | Select the name of an existing end-user group that is authorized to use the URL in Auth Path. |
User Realm | Type the realm, such as Restricted Area, to which the Auth Path belongs. The realm is often used by browsers: • It may appear in the browser’s prompt for the user’s credentials. Especially if a user has multiple logins, and only one login is valid for that specific realm, displaying the realm helps to indicate which user name and password should be supplied. • After authenticating once, the browser may cache the authentication credentials for the duration of the browser session. If the user requests another URL from the same realm, the browser often will automatically re-supply the cached user name and password, rather than asking the user to enter them again for each request. The realm may be the same for multiple authentication rules, if all of those URLs permit the same user group to authenticate. For example, the user group All_Employees could have access to the Auth Path URLs /wiki/Main and /wiki/ToDo. These URLs both belong to the realm named Intranet Wiki. Because they use the same realm name, users authenticating to reach /wiki/Main usually will not have to authenticate again to reach /wiki/ToDo, as long as both requests are within the same browser session. This field does not appear if Auth Type is NTLM, which does not support HTTP-style realms. |
Auth Path | Type the literal URL, such as /employees/holidays.html, that a request must match in order to invoke HTTP authentication. |