Authentication
The Windows AD server and inactive users can be monitored from Monitor > Authentication. Learned RADIUS users can also be configured.
Locked-out Users
To view the locked out users, go to Monitor > Authentication > Locked-out Users.
To unlock a user from the list, select the user, then select Unlock. The list can be refreshed by selecting Refresh, and searched using the search field.
The list shows the username, server, the reason the user was locked out, and when they are locked out until.
For more information on locked out users, see Top User Lockouts widget, Lockouts, and User Management.
RADIUS Sessions
FortiAuthenticator administrators can monitor RADIUS activity and force logout of a user if they wish.
To view currently active RADIUS accounting sessions, go to Monitor > Authentication > RADIUS Sessions.
The page shows the user's name, type, IP address, MAC address, and RADIUS client, duration, and data usage columns. More specifically, Accounting-Start Interim-Update packets are received. A user session is removed from this table once the Accounting-Stop packet is received, or the session doesn't receive any RADIUS accounting packets before the timeout period expires.
To forcefully logout a user, select the user from the table and select Logoff.
There are two pages two view: Active and Cumulative. Select Cumulative to view user stats who have a time and/or data usage limit. This information may be accumulated through a succession of RADIUS accounting sessions. A user's stats are removed when explicitly deleted by the administrator (by selecting the user and selecting Delete), or when the user's account itself is deleted.
While administrators can forcefully logout users, they can also reset a user's time and/or data usage using Reset Usage.
|
|
For more information on user time and data usage limits, see Usage Profile. |
RADIUS Accounting sessions can be configured to timeout after a specific time period has been reached. To do so, see General.
Windows AD
As of FortiAuthenticator 4.2, FortiAuthenticator supports multiple Windows AD server forests, as shown below. A maximum of 20 Remote LDAP servers with Windows AD enabled can be configured at once. In addition, you can now see when the server was updated last, and an option to reset the connection for individual servers.
To view the Windows AD server information, go to Monitor > Authentication > Windows AD.
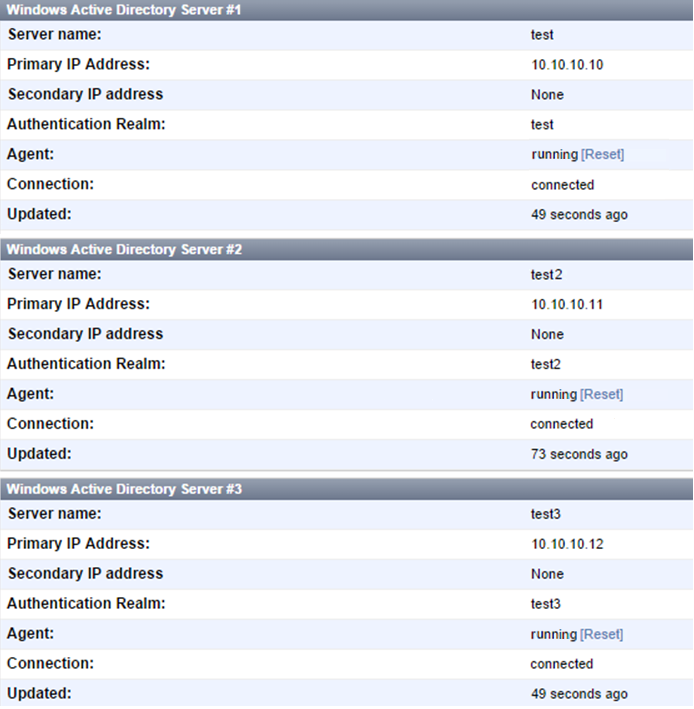
To refresh the connection, select Refresh in the toolbar. The server name, IP address, authentication realm, agent, and connection are shown.
Windows Device Logins
To view the Windows device logins, go to Monitor > Authentication > Windows Device Logins.
To refresh the list, select Refresh in the toolbar. See Machine authentication for more information.
Learned RADIUS users
Learned RADIUS users are users that have been learned by the FortiAuthenticator after they have authenticated against a remote RADIUS server.
For information on enabling learning RADIUS users, see RADIUS on page 1.
