Windows Event Log Sources
If Active Directory will be used to ascertain group information, the FortiAuthenticator unit must be configured to communicate with the domain controller.
A domain controller entry can be disabled without deleting its configuration. This can be useful when performing testing and troubleshooting, or when moving controllers within your network.
|
|
In order to properly discover the available domains and domain controllers, the DNS settings must specify a DNS server that can provide the IP addresses of the domain controllers. See DNS. |
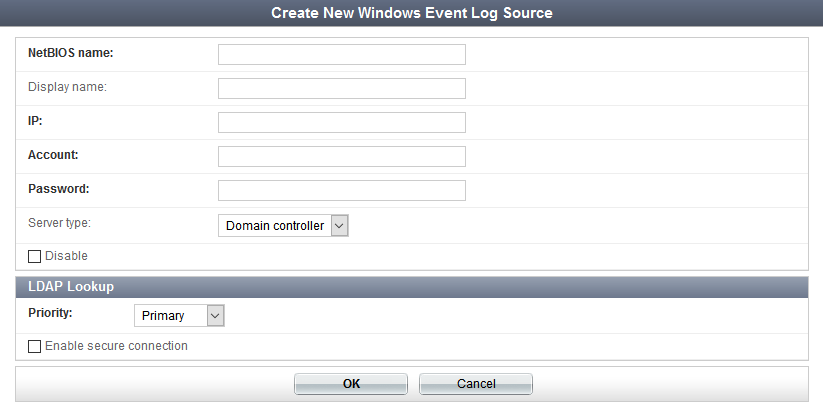
To add a domain controller:
- Go to Fortinet SSO Methods > SSO > Windows Event Log Sources.
- Select Create New to open the Create New Windows Event Log Source window.
- Enter the following information:
- Select OK.
By default, FortiAuthenticator uses auto-discovery of Domain Controllers. If you want to restrict operation to the configured domain controllers only, go to Fortinet SSO Methods > SSO > General and select Restrict auto-discovered domain controllers to configured domain controllers. See General settings.
