Configuring FortiWeb to validate client certificates
To be valid, a client certificate must:
• not be expired or not yet valid
• not be revoked by a certificate revocation list (CRL)
• contain a CA field whose value matches a CA’s certificate
• contain an Issuer field whose value matches the Subject field in a CA’s certificate
If the client presents an invalid certificate during PKI authentication for HTTPS, FortiWeb does not allow the connection.
Certificate validation rules (in the web UI, these are called certificate verification rules) tell FortiWeb which set of CA certificates to use when it validates personal certificates. They also specify a CRL, if any, if the client’s certificate must be checked for revocation.
Alternatively, if you have enabled SNI in a server policy or server pool, FortiWeb uses the set of CA certificates specified in the SNI configuration that matches the client request to validate personal certificates.
If you configure the URL-based client certificate feature in a server policy or group, the rules in the specified URL-based client certificate group determine whether a client is required to present a personal certificate.
To configure a certificate validation rule
2. Go to System > Certificates > Certificate Verify.
To access this part of the web UI, your administrator's account access profile must have
Read and
Write permission to items in the
Admin Users category. For details, see
“Permissions”.
3. Click Create New.
A dialog appears.
4. Configure these settings:
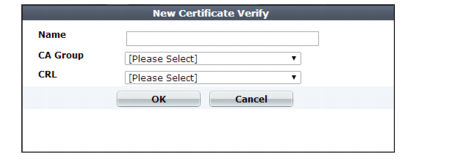
Setting name | Description |
Name | Type a name that can be referenced in other parts of the configuration. Do not use spaces or special characters. The maximum length is 35 characters. |
CA Group | Select the name of an existing CA group that you want to use to authenticate client certificates. See “Grouping trusted CAs’ certificates”. |
CRL | Select the name of an existing certificate revocation list, if any, to use to verify the revocation status of client certificates. See “Revoking certificates”. |
5. Click OK.
6. To apply a certificate verification rule, do one of the following:
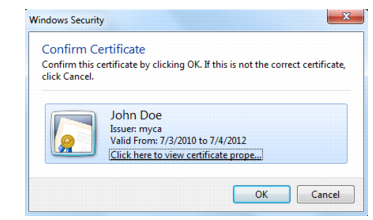
When a client connects to the web site, after FortiWeb presents its own server certificate, it will request one from the client.The web browser should display a prompt, allowing the person to indicate which personal certificate he or she wants to present.
When a PKI authentication attempt fails, if you have enabled logging, attack log messages will be recorded. Messages vary by the cause of the error. Common messages are:
X509 Error 20 - Issuer certificate could not be found (FortiWeb does not have the certificate of the CA that signed the personal certificate, and therefore cannot verify the personal certificate; see
“Uploading trusted CAs’ certificates”)
X509 Error 52 - Get client certificate failed (the client did not present its personal certificate to FortiWeb, which could be caused by the client not having its personal certificate properly installed; see
“How to apply PKI client authentication (personal certificates)”)
X509 Error 53 - Protocol error (various causes, but could be due to the client and FortiWeb having no mutually understood cipher suite or protocol version during the SSL/TLS handshake)
For more logs, see the
FortiWeb Log Reference.
See also