Expanding the initial configuration
After your FortiWeb appliance has operated for several days without significant problems, it is a good time to adjust profiles and policies to provide additional protection and to improve performance.
• Begin monitoring the third-party cookies FortiWeb observes in traffic to your web servers. When cookies are found, an icon appears on
Policy > Server Policy > Server Policy for each affected server. If cookies are threats, such as if they are used for state tracking or database input, consider enabling the
Cookie Poisoning option on the inline protection profiles for those servers.
• Add any missing rules and policies to your protection profiles, such as:
Especially if you began in offline protection mode and later transitioned to another operation mode such as reverse proxy, new features may be available that were not supported in the previous operation mode.
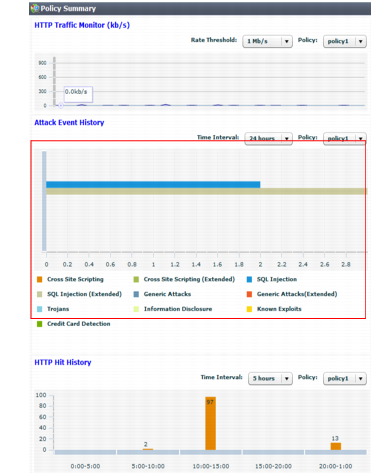
• Examine the Attack Event History in the Policy Summary widget on System > Status > Status. If you have zero attacks, but you have reasonable levels of traffic, it may mean the protection profile used by your server policy is incomplete and not detecting some attack attempts.
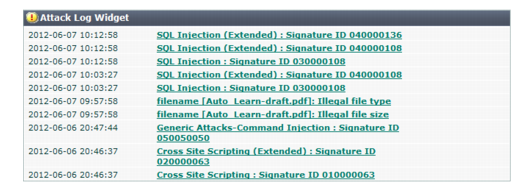
• Examine the
Attack Log widget on
System > Status > Status. If the list includes many identical entries, it likely indicates false positives. If there are many entries of a different nature, it likely indicates real attacks. If there are no attack log entries but the
Attack Event History shows attacks, it likely means you have not correctly configured logging. See
“Configuring logging”.
You can create reports to track trends that may deserve further attention. See
“Data analytics”,
“Vulnerability scans”, and
“Reports”.