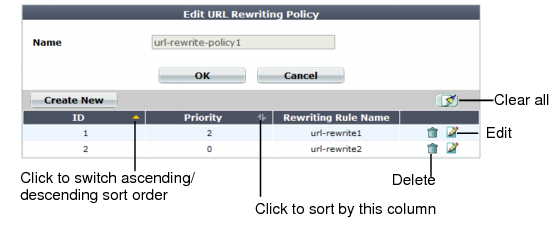
A dialog appears. Its appearance varies by your settings in Action Type, and Request Action or Response Action. 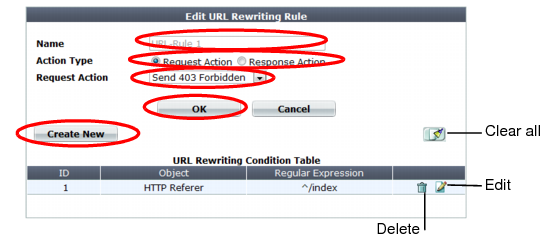

Rewrites/redirects are not supported in all modes. See “Supported features in each operation mode”. FortiWeb cannot rewrite requests that exceed FortiWeb’s buffer size. To block requests that cannot be rewritten, configure Malformed Request. |

Setting name | Description |
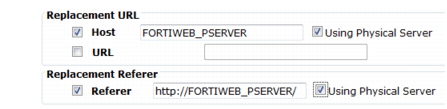
Host | Enable then type either a host name, such as store.example.com, or IP address if you want to replace the value of the Host: field in the header of HTTP requests. Requests will be redirected to this web host. This field supports back references such as $0 to the parts of the original request that matched any capture groups that you entered in Regular Expression for each object in the condition table. (A capture group is a regular expression, or part of one, surrounded in parentheses. See “Regular expression syntax”.) For an example, see “Example: Rewriting URLs using variables”. |
Using Physical Server | At the time of each specific HTTP request, FortiWeb will replace this variable with the IP address of the physical server to which it is forwarding the request. Tip: Use this option when the Deployment Mode option in the server policies using this rule is either Server Balance or HTTP Content Routing. In such cases, by definition of load balancing, HTTP requests will be distributed among multiple web servers, and the specific IP addresses of the physical servers cannot be known in advance. |
URL | Enable then type a string, such as /catalog/item1, if you want to replace the URL in the HTTP request. Do not include the name of the web host, such as www.example.com, nor the protocol. Like Host, this field supports back references such as $0 to the parts of the original request that matched any capture groups that you entered in Regular Expression for each object in the condition table (see “What are back-references?”). For an example, see “Example: Rewriting URLs using regular expressions”. |
Referer | Enable then type a URI, such as http://www.example.com/index, if you want to rewrite the Referer: field in the HTTP header. This option is available only if Request Action is Rewrite HTTP Header. |
Using Physical Server | At the time of each specific HTTP request, FortiWeb will replace this variable with the IP address of the physical server to which it is forwarding the request. Tip: Use this option when the Deployment Mode option in the server policies using this rule is either Server Balance or HTTP Content Routing. In such cases, by definition of load balancing, HTTP requests will be distributed among multiple web servers, and the specific IP addresses of the physical servers cannot be known in advance. |
Setting name | Description |
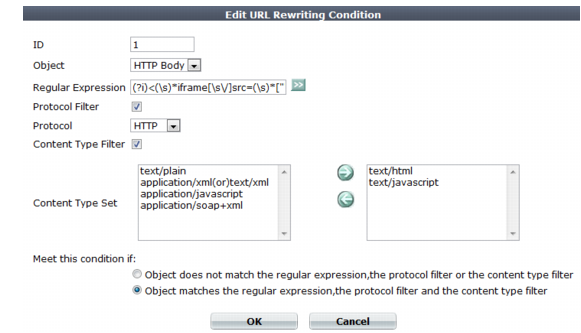
Object | Select which part of the HTTP request will be tested for a match: • HTTP Host — The Host: field in the HTTP header. This option does not appear if Response Action in step 6 was Rewrite HTTP Body. • HTTP Request URL — The URL in the HTTP header. The URL can be up to 1,024 characters long, unless superseded by HTTP constraints such as Header Line Length. This option does not appear if Response Action in step 6 was Rewrite HTTP Body. • HTTP Referer — The Referer: field in the HTTP header. This option appears only if Action Type in step 4 was Request Action. This option does not appear if Response Action in step 6 was Rewrite HTTP Body. • HTTP Body — The content of the request, such as an HTML document. This option appears only if Response Action in step 6 was Rewrite HTTP Body. • HTTP Location — The Location: field in the header of the request. This option appears only if Response Action in step 6 was Rewrite HTTP Location. If the request must meet multiple conditions (for example, it must contain both a matching Host: field and a matching URL), add each condition to the condition table separately. |
Regular Expression | Depending on your selection in Object and Meet this condition if, type a regular expression that defines either all matching or all non-matching objects. Also configure Meet this condition if. |
For example, for the URL rewriting rule to match all URLs that begin with /wordpress, you could enter ^/wordpress, then, in Meet this condition if, select Object matches the regular expression. The pattern is not required to begin with a slash ( / ). When you have finished typing the regular expression, click the >> (test) icon. This opens the Regular Expression Validator window where you can fine-tune the expression (see “Regular expression syntax”, “What are back-references?” and “Cookbook regular expressions”). | |
Protocol Filter | Enable if you want to match this condition only for either HTTP or HTTPS. Also configure Protocol. For example, you could redirect clients that accidentally request the login page by HTTP to a more secure HTTPS channel — but the redirect is not necessary for HTTPS requests. As another example, if URLs in HTTPS requests should be exempt from rewriting, you could configure the rewriting rule to apply only to HTTP requests. |
Protocol | Select which protocol will match this condition, either HTTP or HTTPS. This option appears only if Protocol Filter is enabled. |
Content Type Filter | Enable if you want to match this condition only for specific HTTP content types (also called Internet or MIME file types) such as text/html, as indicated in the Content-Type: HTTP header. Also configure Content Type Set. |
Content Type Set | In the left text area, select one or more HTTP content types that you want to match this condition, then click the right arrow button to move them into the text area on the right side. This option is visible only if Content Type Filter is enabled. |
Meet this condition if | Indicate how to use Regular Expression when determining whether or not this URL rewriting condition is met. • Object does not match the regular expression — If the regular expression does not match the request object, the condition is met. • Object matches the regular expression — If the regular expression does match the request object, the condition is met. If all conditions are met, the FortiWeb appliance executes the Request Action or Response Action, whichever you selected. |
Setting name | Description |
If no Referer field in HTTP header | Select either: • Do not meet this condition • Meet this condition Requests can lack a Referer: field for several reasons, such as if the user manually types the URL, and the request does not result from a hyperlink from another web site, or if the URL resulted from an HTTPS connection. (See the RFC 2616 section on the Referer: field.) In those cases, the field cannot be tested for a matching value. This option appears only if Object is HTTP Referer. |