Grouping DoS protection rules
Before you can apply them in a server policy via a protection profile, you must first group DoS prevention rules.
To configure a DoS protection policy
1. Before you can configure a DoS protection policy, you must first configure the rules that you want to include:
2. Go to DoS Protection > DoS Protection Policy > DoS Protection Policy.
To access this part of the web UI, your administrator’s account access profile must have
Read and
Write permission to items in the
Web Protection Configuration category. For details, see
“Permissions”.
3. Click Create New.
A dialog appears.
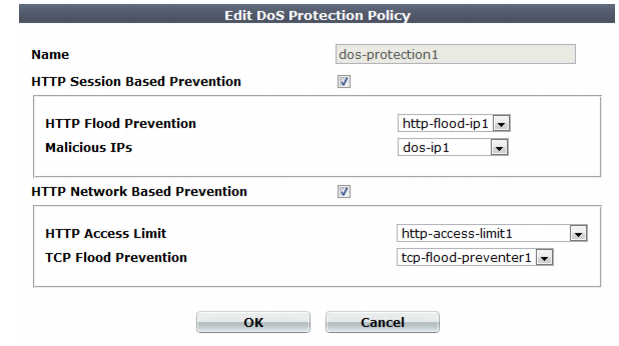
4. In Name, type a unique name that can be referenced by other parts of the configuration. Do not use spaces or special characters. The maximum length is 35 characters.
5. If you want to apply features that use session cookies, enable HTTP Session Based Prevention.
• From
HTTP Flood Prevention, select an existing rule that sets the maximum number of HTTP requests per second to a specific URL (see
“Preventing an HTTP request flood”).
6. If you want to restrict traffic based upon request or connection counts, enable HTTP Network Based Prevention.
7. Click OK.
9. If you have configured DoS protection features that use session cookies, also enable the
Session Management option in the protection profile.
See also


