Preventing a TCP SYN flood
You can configure protection from TCP SYN flood-style denial of service (DoS) attacks.
TCP SYN floods attempt to exploit the state mechanism of TCP. At the point where a client has only sent a SYN signal, a connection has been initiated and therefore consumes server memory to remember the state of the half-open connection. However, the connection has not yet been fully formed, and therefore packets are not required to contain any actual application layer payload such as HTTP yet. Because of this, it cannot be blocked by application-layer scans, nor can it be blocked by scans that only count fully-formed socket connections (where the client’s SYN has been replied to by a SYN ACK from the server, and the client has confirmed connection establishment with an ACK).
Normally, a legitimate client will quickly complete the connection build-up and tear-down. However, an attacker will initiate many connections without completing them, until the server is exhausted and has no memory left to track the TCP connection state for legitimate clients.
To prevent this, FortiWeb can use a “SYN cookie” — a small piece of memory that keeps a timeout for half-open connections. This prevents half-open connections from accumulating to the point of socket exhaustion.
This feature is similar to DoS Protection > Network > TCP Flood Prevention. However, this feature counts partially-formed TCP connections, while TCP Flood Prevention counts fully-formed TCP connections.
To configure TCP SYN flood protection
1. Go to
DoS Protection > Network > Syn Cookie.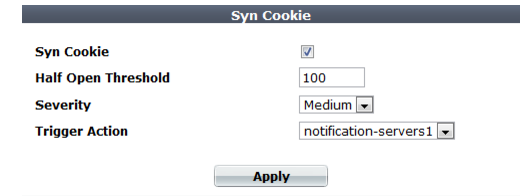
To access this part of the web UI, your administrator’s account access profile must have
Read and
Write permission to items in the
Web Protection Configuration category. For details, see
“Permissions”.
2. Enable Syn Cookie.
3. In Half Open Threshold, enter the maximum number of TCP SYN packets, including retransmission, that may be sent per second to a destination address. If this threshold is exceeded, the FortiWeb appliance assumes a DoS attack is occurring and ignores additional traffic from that source IP address.
4. From the Severity drop-down list, select the severity level to include in logs and/or alert email when this type of attack is detected.
5. From the
Trigger Action drop-down list, select the trigger, if any, that defines which log and/or alert email servers the FortiWeb appliance will use contact when the threshold is exceeded (see
“Configuring triggers”).
6. Click Apply.
Unlike other DoS protection features, you do not need to include this setting in a DoS protection policy to make it effective. Once configured, the FortiWeb appliance applies SYN flood protection immediately to all connections attempting to through it.
See also


