Configuring triggers
Triggers are sets of notification servers (Syslog, FortiAnalyzer, and alert email) that you can select in protection rules. The FortiWeb appliance will contact those servers when traffic violates the policy and therefore triggers logging and/or alert email.
For example, if you create a trigger that contains email and Syslog settings, that trigger can be selected as the trigger action for specific violations of a protection profile’s sub-rules. Alert email and Syslog records will be created according to the trigger when a violation of that individual rule occurs.
To configure triggers
2. Go to Log&Report > Log Policy > Trigger Policy.
To access this part of the web UI, your administrator’s account access profile must have
Read and
Write permission to items in the
Log & Report category. For details, see
“Permissions”.
3. Click Create New.
A dialog appears.
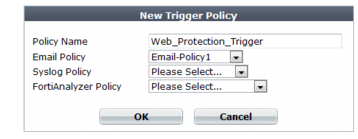
4. In Name, type a unique name that can be referenced by other parts of the configuration. Do not use spaces or special characters. The maximum length is 35 characters.
5. Pick an existing policy from one or more of the three email, Syslog or FortiAnalyzer setting drop-down lists. FortiWeb will use these notification devices for all protection rule violations that use this trigger.
6. Click OK.
7. To apply the trigger, select it in the Trigger Action setting in a web protection feature, such as a hidden field rule, or an HTTP constraint on illegal host names.


