4. Configure these settings: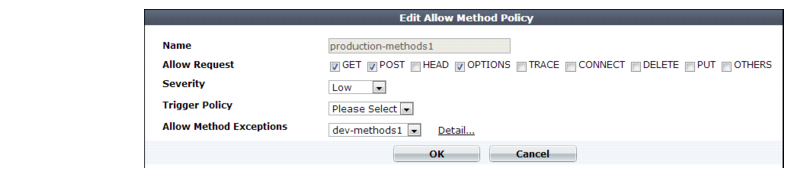

Generally, TRACE should only be used during debugging, and should be disabled otherwise. |

Setting name | Description |
Name | Type a unique name that can be referenced in other parts of the configuration. Do not use spaces or special characters. The maximum length is 35 characters. |
Allow Request | Mark the check boxes for all HTTP request methods that you want to allow for this specific policy. Methods that you do not select will be denied, unless specifically allowed for a host and/or URL in the selected Allow Method Exceptions. The OTHERS option includes methods not specifically named in the other options. It often may be required by WebDAV (RFC 4918) applications such as Microsoft Exchange Server 2003 and Subversion, which may require HTTP methods not commonly used by web browsers, such as PROPFIND and BCOPY. Note: If a WAF Auto Learning Profile is used in the server policy where the HTTP request method is applied (via the Web Protection Profile), you must enable the HTTP request methods that will be used by sessions that you want the FortiWeb appliance to learn about. If a method is disabled, the FortiWeb appliance will reset the connection, and therefore cannot learn about the session. |
Severity | When rule violations are recorded in the attack log, each log message contains a Severity Level (severity_level) field. Select which severity level the FortiWeb appliance will use when it logs a violation of the rule: • Low • Medium • High The default value is Medium. |
Trigger Action | Select which trigger, if any, that the FortiWeb appliance will use when it logs and/or sends an alert email about a violation of the rule. See “Configuring triggers”. |
Allow Method Exceptions | Select an HTTP request method exception definition to apply to the policy. The method exceptions define specific HTTP request methods that are allowed by specific URLs and hosts. If you want to view the information associated with the HTTP request method exceptions used by this policy, select the Detail link beside the Allow Method Exceptions list. The Allow Method Exceptions dialog appears. Use the browser Back button to return. For more information, see “Configuring allowed method exceptions”. |