A dialog appears. 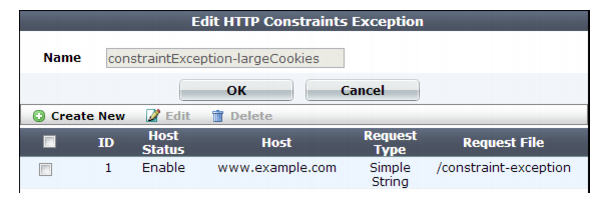

Like any software, FortiWeb’s buffers are not endless. If an HTTP request overall or its individual components such as parameters are too long to fit the scan buffer, they will you do not want to |

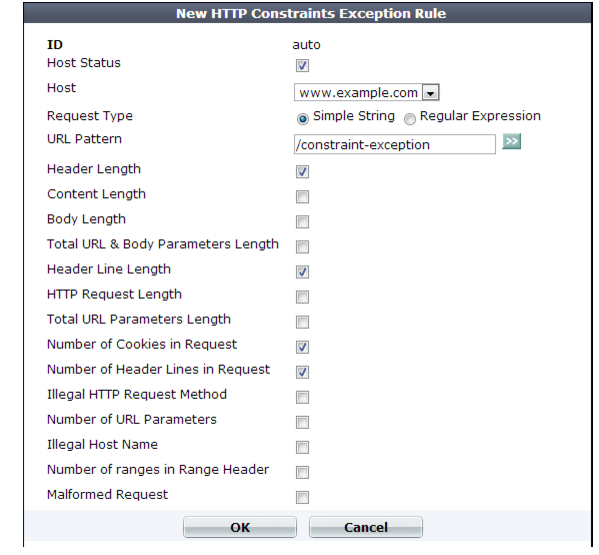
Setting name | Description |
Host Status | Enable to apply this HTTP constraint exception only to HTTP requests for specific web hosts. Also configure Host. Disable to apply the exceptions to all web hosts. |
Host | Select the IP address or fully qualified domain name (FQDN) of the protected host to which this exception applies. This setting is available only if Host Status is enabled. |
Request Type | Select whether the URL Pattern field will contain a literal URL (Simple String), or a regular expression designed to match multiple URLs (Regular Expression). |
URL Pattern | Depending on your selection in the Request Type field, enter either: • the literal URL, such as /index.php, that the HTTP request must contain in order to match the input rule. The URL must begin with a backslash ( / ). • a regular expression, such as ^/*.php, matching all and only the URLs to which the input rule should apply. The pattern does not require a slash ( / ); however, it must at match URLs that begin with a slash, such as /index.cfm. Do not include the domain name, such as www.example.com, which is configured separately in the Host drop-down list. To create and test a regular expression, click the >> (test) icon. This opens the Regular Expression Validator window where you can fine-tune the expression (see “Regular expression syntax”)n. |
Header Length | Enable to omit the constraint on the maximum acceptable size in bytes of the HTTP header. |
Content Length | Enable to omit the constraint on the maximum acceptable size in bytes of the request body. |
Body Length | Enable to omit the constraint on the maximum acceptable size in bytes of the HTTP body. |
Parameter Length | Enable to omit the constraint on the maximum acceptable size in bytes of parameters in the URL or, for HTTP POST requests. |
Header Line Length | Enable to omit the constraint on the maximum acceptable size in bytes of each line in the HTTP header. |
HTTP Request Length | Enable to omit the constraint on the maximum acceptable length in bytes of the HTTP request. |
URL Parameter Length | Enable to omit the constraint on the maximum acceptable size of an URL parameter (including the name and value). |
Number of Cookies In Request | Enable to omit the constraint on the maximum acceptable number of cookies in an HTTP request. |
Number of Header Lines In Request | Enable to omit the constraint on the maximum acceptable number of lines in the HTTP header. |
Illegal HTTP Request Method | Enable to omit the constraint on to check for invalid HTTP version numbers. |
Number of URL Parameters | Enable to omit the constraint on the maximum number of parameters in the URL. |
Illegal Host Name | Enable to omit the constraint on invalid characters in the Host: line of the HTTP header, such as null characters or encoded characters. |
Number of ranges in Range Header | Enable to omit the constraint on the maximum acceptable number of Range: lines in an HTTP header. Tip: Some versions of Apache are vulnerable to a denial of service (DoS) attack on this header, where a malicious client floods the server with many Range: headers. If your web servers do not run Apache and are not vulnerable to this attack, mark this check box to omit it from the scan and improve performance. |
Malformed Request | Enable to omit the constraint on syntax and FortiWeb parsing errors. Caution: Some web applications require abnormal or very large HTTP POST requests. Since allowing such errors and excesses is generally bad practice and can lead to vulnerabilities, use this option to omit the malformed request scan only if absolutely necessary. |