2. Configure these settings: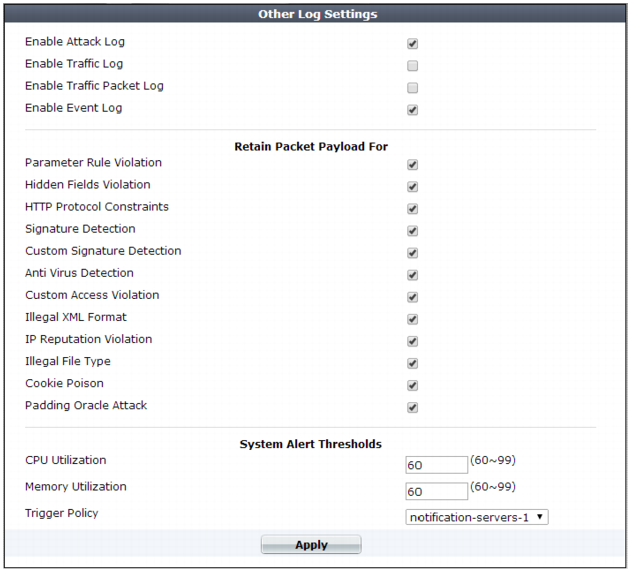


Setting name | Description | |
Enable Attack Log | Enable to log violations of attack policies, such as server information disclosure and attack signature matches, if that feature is configured such that Action is set to Alert, Alert & Deny, or Alert & Erase. | |
Enable Traffic Log | Enable to log traffic events such as HTTP requests and responses, and the expiration of HTTP sessions. Tip: Because resources for this feature increase as your traffic increases, if you do not need traffic data, disable this feature to improve performance and improve hardware life. | |
Enable Traffic Packet Log | Enable to retain the packet payloads of all HTTP request traffic. Unlike attack packet payloads, only HTTP request traffic packets are retained (not HTTP responses), and only the first 4 KB of the payload from the buffer of FortiWeb’s HTTP parser. Packet payloads supplement the log message by providing the actual request body, which may help you to fine-tune your regular expressions to prevent false negatives, or to examine changes to attack behavior for subsequent forensic analysis. To view packet payloads, see “Viewing packet payloads”. Tip: Retaining traffic packet payloads is resource intensive. To improve performance, only enable this option while necessary. | |
Enable Event Log | Enable to log local events, such as administrator logins or rebooting the FortiWeb appliance. | |
Retain Packet Payload For | Mark the check boxes of the attack types or validation failures to retain the buffer from FortiWeb’s HTTP parser. Packet retention is enabled by default for most types. Packet payloads supplement the log message by providing part of the actual data that matched the regular expression, which may help you to fine-tune your regular expressions to prevent false positives, or to examine changes to attack behavior for subsequent forensic analysis. To view packet payloads, see “Viewing packet payloads”. If packet payloads could contain sensitive information, you may need to obscure those elements. For details, see “Obscuring sensitive data in the logs”. Note: FortiWeb retains only the first 4 KB of data from the offending HTTP request payload that triggered the log message. If you require forensic analysis of, for example, buffer overflow attacks that would exceed this limit, you must implement it separately. | |
CPU Utilization | Select a threshold level (60% to 99%) beyond which CPU usage will trigger an event log entry. | |
Memory Utilization | Select a threshold level (60% to 99%) beyond which memory usage will trigger an event log entry. | |
Trigger Action | Select an trigger, if any, to use when memory usage or CPU usage reaches or exceeds its specified threshold. | |