Predefined suspicious request URLs
Predefined regular expressions can be used by auto-learning to detect requests that are suspicious because they are for a URL that provides administrative access to the web server, servlet, or web application, such as:
/admin.php
/conf/Catalina/localhost/admin.xml
or access to its back-end cache, data files, or Berkeley databases, such as:
/local/notesdata
Normally, requests for these URLs should only originate from a trusted network such as your management computers, not from the Internet. (Exceptions include hosting providers, whose clients around the globe configure their own web applications.) Therefore these requests are a good candidate for URL access control rules.
Many signatures exist for popular web servers and applications such as Apache, nginx IIS, Tomcat, and Subversion. Known suspicious request URLs can be updated. See
“Connecting to FortiGuard services”.
To access this part of the web UI, your administrator’s account access profile must have
Read and
Write permission to items in the
Server Policy Configuration category. For details, see
“Permissions”.
Table 31: Auto Learn > Predefined Pattern > URL Pattern (image cropped)
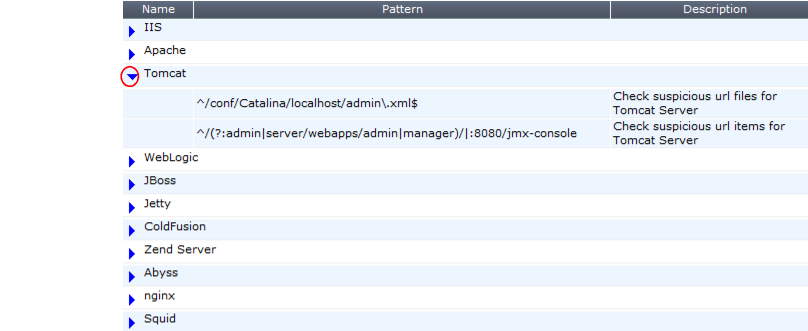
Setting name | Description |
Name | The name of the predefined suspicious URL pattern set. To display the patterns it contains, click the blue arrow next to the name. |
Pattern | When you click a blue arrow to expand a suspicious URL pattern, this column displays the regular expression used to detect the presence of the suspicious URL in a client’s request. |
Description | When you click a blue arrow to expand a data type, this column displays a description of the URLs matched by this pattern, such as Apache web server administrative web UI files or IBM Lotus Domino data. |
See also


