Figure 90: DDoS Attack Log remote logging configuration page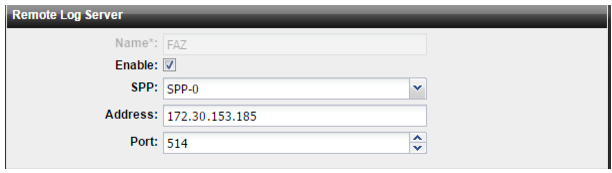


Settings | Guidelines |
Name | Configuration name. |
Enable | Select to enable sending DDoS attack logs to a remote server. |
SPP | Select the SPP whose logs are stored in the remote location. You can specify only one remote log server for each SPP. |
Address | IP address of the FortiAnalyzer/syslog server. |
Port | Listening port number of the FortiAnalyzer/syslog server. Usually this is UDP port 514. |
Field | Example |
Syslog send timestamp | Apr 24 13:22:08 |
Syslog server IP address | 192.168.205.202 |
Device ID | devid=FI800B3913000004 |
Log datestamp | date=2015-04-23 |
Log timestamp | time=01:10:00 |
Log time zone | tz=PDT |
Log type | type=attack |
SPP ID | spp=0 |
Event code | evecode=1 |
Event subcode | evesubcode=14 |
Event type | description="IP Header checksum error" |
Direction (0=inbound, 1=outbound) | dir=1 |
Source IP address | sip=0.0.0.0 |
Destination IP address | dip=10.10.0.1 |
Subnet name | subnet_name=VID0 |
Subnet comment | subnet_comment=Dept_0 |
Drop count | dropcount=684138 |