4. Configure these settings: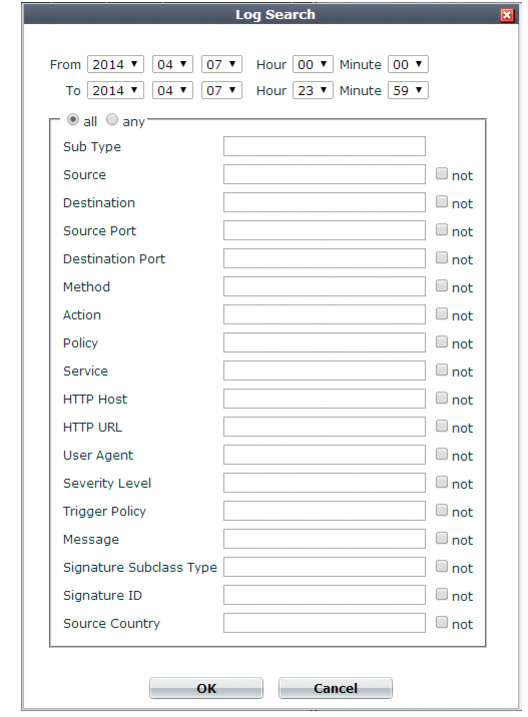

If searching HTTP constraint logs based upon the Message (msg) field, make sure that your search criteria considers the entire message. The whole Message field is not displayed in Formatted view, which hides the prefix; you must use Raw view instead. |

Setting name | Description |
Keyword(s) | Type the exact keywords you want to search for. Unlike a quick search, an advanced search returns only the results that exactly match the specified keywords. For example, entering allow as a keyword will not provide results such as allow_host and waf_allow_method. You must enter the exact terms. If a single keyword consists of multiple words each separated by a space, surround the words with quotation marks ( " ). If quotation marks are not used, the search will treat each word as an individual keyword. This setting is optional. Note: If you entered keywords in the quick search field before opening the advanced Search Dialog, those keywords are retained when the dialog opens, and will be used as part of the parameters for the advanced search. Remove the keyword if it does not apply to your advanced search. |
From/To Hour Minute | Select the date and time range that contains the attack log that you are searching for. Note: The date fields default to the current date. Ensure the date fields are set to the actual date range that you want to search. |
all/any | Select all if you want to search for all terms specified in the fields shown below the all/any options. For example, if terms are entered in Sub Type and Action, the search results display only the attack logs matching both of those terms. Select any if you want to search for any one of the terms specified in the fields shown below the all/any options. For example, if terms are entered in Sub Type, Source, Action and Policy, the search results display the attack logs that match any of those terms. |
not | Select not if you want to search for conditions that exclude a specific term. For example, if an IP address is entered in the Source field, and not is selected, the search results exclude all attack logs with that source IP address. |
Sub Type Source Destination Source Port Destination Port Method Action Policy Service HTTP Host HTTP URL User Agent Severity Level Trigger Policy Message Signature Subclass Type Signature ID Source Country | Type an exact match for the value of one or more log fields. To exclude log records that match a criterion, mark its Not check box. Note: Source may be the IP address according to an HTTP header such as X-Forwarded-For: instead of the SRC at the IP layer. See “Defining your proxies, clients, & X-headers”. |
Search results include only exact matches for keywords and terms entered in the advanced Search Dialog. Ensure that the keywords and terms are accurate and relevant to the search and that the date and time fields cover the actual range you want to search. |