Coalescing similar attack log messages
FortiWeb can generate many types of attack log messages, including Custom Access Violation, Header Length Exceeded, IP Reputation Violation, and SQL Injection.
To make attack log messages easier to review, when the total number of attack types exceeds 32 in a single day, FortiWeb aggregates two types of messages — signature attacks and HTTP protocol constraints violations — in the Aggregated Attacks page.
FortiWeb aggregates signature attack messages as a "Signature attacks detected" item and the HTTP protocol constraints violations as a "HTTP protocol constraints violations" item. The appliance preserves all other types of attack log messages as individual messages.
For more information on the signatures and constraints that generate the aggregated messages, see
“Blocking known attacks & data leaks” and
“HTTP/HTTPS protocol constraints”.
To coalesce similar attack log messages
1. Go to Log&Report > Log Access > Aggregated Attacks.
To access this part of the web UI, your administrator’s account access profile must have
Read and
Write permission to items in the
Log & Report category. For details, see
“Permissions”.
2. Each row of aggregated log messages is initially grouped into similar attack types, not primarily by day or time.
If you want to aggregate attacks by time instead, click
Aggregate log by Date.
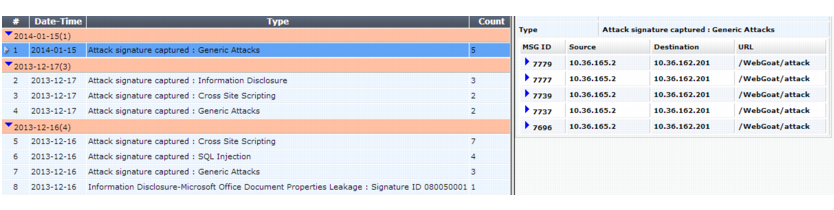
Each page in the display contains up to 7 dates’ worth of aggregated logs. To view dates before that time, click the arrow to go to the next page.
3. To expand a row in order to view individual items comprising it, click the blue arrow in the
# column.
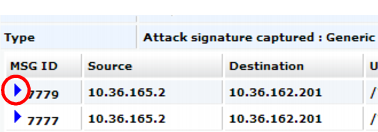
4. To view a list of all mog messages comprising that item, click the item’s row. Details appear in a pane to the right.