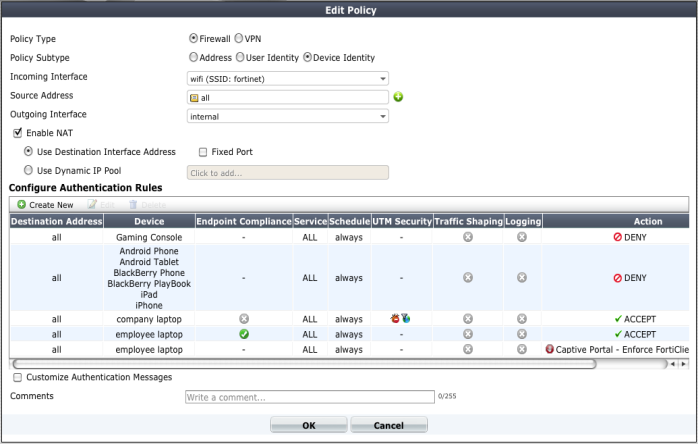
Device policies
Policies based on device identity enable you to implement policies according to device type. For example:
• Gaming consoles cannot connect to the company network or the Internet.
• Personal tablet and phone devices can connect to the Internet but not to company servers.
• Company-issued laptop computers can connect to the Internet and company servers. Web filtering and antivirus are applied.
• Employee laptop computers can connect to the Internet, but web filtering is applied. They can also connect to company networks, but only if FortiClient Endpoint Security is installed to protect against viruses.
Figure 48 shows these policies implemented for WiFi to the company network.
Device-based security policies are similar to policies based on user identity:
• The policy enables traffic to flow from one network interface to another.
• NAT can be enabled.
• Authentication rules can allow or deny specific devices or device groups.
• UTM protection can be applied.
To create a device identity policy
1. Go to Policy > Policy > Policy and select Create New.
2. In Policy Subtype, select Device Identity.
3. Choose Incoming Interface, Source Address, and Outgoing Interface as you would for any security policy.
4. Select Enable NAT if appropriate.
You are now ready to create authentication rules.
To create an authentication rule
1. Select Create New.
2. Enter Destination, Schedule, and Service as you would for any security policy.
3. In Device, select the devices or device groups to which this policy applies.
You can select multiple devices or groups.
4. Select
Compliant with Endpoint Profile if you want to enforce use of FortiClient Endpoint Security by the client devices. This is available here only if Action is ACCEPT. See
“Adding endpoint control” next.
5. Select one of the following for Action:
• ACCEPT
• DENY
6. Configure UTM Security Profiles as you would for any security policy.
7. Select OK.
8. Select OK again to complete creation of the security policy.