Traffic diversion deployment
In some environments, such as a service provider environment, the total bandwidth is more than what the FortiDDoS appliance supports. However, the attack traffic to a specific subnet or server is within the appliance’s capacity. You can route normal traffic through its regular path and manually divert the attack traffic. The FortiDDoS cleanses the diverted traffic and injects it back to the network.
The FortiDDoS appliance is a Layer 2 bridge and therefore does not have either a MAC address or an IP address in the data path. To allow traffic to be diverted, connect the appliance to interfaces on the routers or switches that have a routable IP address.
Figure 142 shows an example topology. The topology uses the following terminology:
• Divert-from router: Router from which the FortiDDoS appliance diverts the attacked customer traffic.
• Inject-to router: Router to which the FortiDDoS appliance forwards legitimate traffic.
Traffic diversion using separate divert-from and inject-to routers
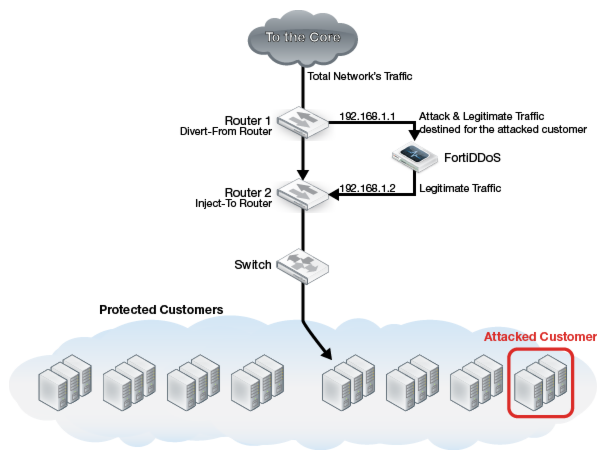
Figure 142 shows a basic topology. In this deployment, Router 1 forwards traffic through the FortiDDoS appliance.
An additional interface on Router 1 Divert-from Router diverts the traffic that is destined for the attacked destination. This traffic passes through the FortiDDoS appliance. The traffic is then forwarded to Router 2 Inject-to Router. These two interfaces are in the same network (192.168.1.x) and therefore an ARP request from Router 1 for 192.168.1.2 passes through the FortiDDoS appliance and reaches Router 2 and Router 2 can respond back with an ARP reply and vice versa.
A static route is added on Router 1 for addresses for the attacked customer network. Because it has the longest matching prefix, the rule matches first and therefore all traffic to the attacked customer network is diverted from Router 1 to Router 2 through the FortiDDoS appliance network rather than going straight from Router 1 to Router 2. Preferably, the return path for traffic is also through the FortiDDoS appliance. Although this solution works even if the traffic is unidirectional through the FortiDDoS appliance, bidirectional traffic helps the appliance determine the statefulness within connections.
Traffic diversion using a single divert-from and inject-to router and a switch
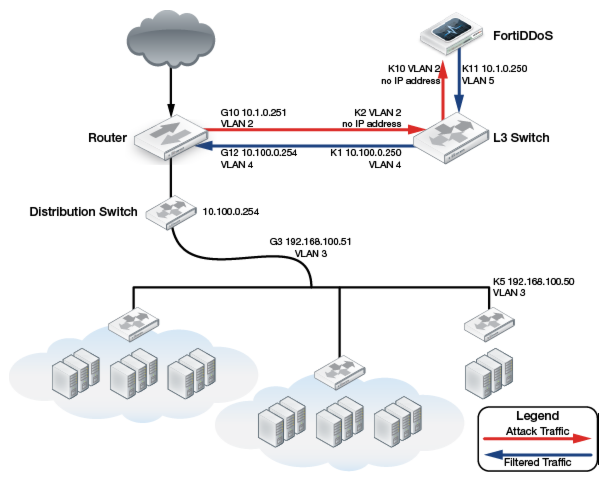
Figure 143 shows a single router that is acting as both a divert-from and inject-to router. Layer 2 forwards through the FortiDDoS appliance.
One interface on the Internet side of the router diverts traffic to the attacked destination. This traffic passes through the FortiDDoS appliance through a switch. The traffic is then forwarded to the inject-to interface on the router through the same switch.
To ensure that the traffic is symmetric and both incoming and outgoing traffic to and from the attacked destination go through the FortiDDoS appliance, the LAN interface of the router diverts the traffic from the attacked destination. This traffic passes through the FortiDDoS appliance through a switch. The traffic is then forwarded to the inject-to interface on the same router through the same switch.
A static route is added on the router for addresses for the attacked customer network. Because it has the longest matching prefix, the rule matches first and therefore all traffic to the attacked customer network is diverted to the Layer 3 switch through the FortiDDoS appliance rather than going straight from the router to the distribution switch.
Preferably, the return path for traffic is through a FortiDDoS appliance. Although the solution works even if the traffic is unidirectional through the FortiDDoS appliance, bidirectional traffic helps the appliance determine the statefulness within connections.
To ensure that the return traffic passes through the FortiDDoS appliance, use the Policy Based Routing (PBR) that is available in most routers. PBR allows you to base routing on the source address of the packets and interface.
Router and switch configuration for diversion
For an example router and switch configuration for traffic diversion, see
“Appendix C: Switch and Router Configuration”.
Setting thresholds for diverted traffic
In some cases, when traffic for a customer network is diverted through the FortiDDoS appliance during attacks, the appliance does not have traffic thresholds that correspond to the diverted network’s normal traffic level or characteristics.
To solve this issue, do one of the following:
• Archive a learning period: During a time of normal traffic activity, divert the customer network traffic to a FortiDDoS appliance. Then, archive the configuration file created during this learning period using System > Maintenance > Backup & Restore. During an attack, restore the configuration and divert the affected traffic to the appliance with the restored configuration.
• Create predefined profiles: Create a series of backup configurations for different traffic levels. For example, define normal traffic levels for 1 Mbps, 10 Mbps, 20 Mbps, 100 Mbps, and so on. In addition, predefine profile parameters such as SYN/second, SYNs/Src, Concurrent Connections/Source, and so on. During an attack, restore the configuration that corresponds to the customer traffic level based on past historical knowledge of the data, and then divert the affected traffic to the appliance with the restored configuration.