Figure 102: Report configuration page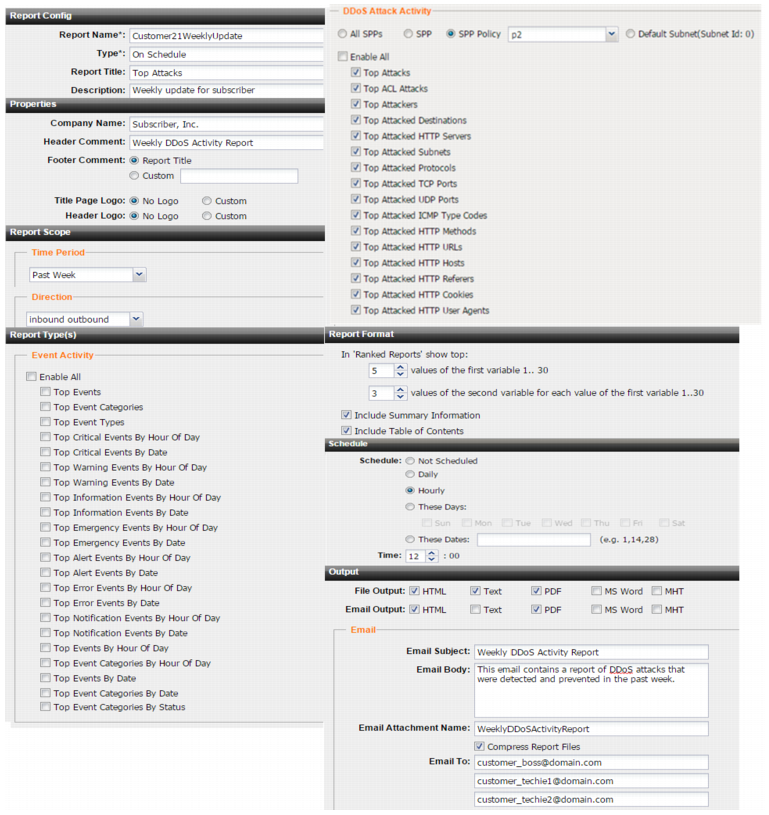


Settings | Guidelines |
Report Config | |
Name | Name for the configuration. Spaces are not valid. |
Type | • On Schedule—Run the report according to the schedule settings (below) • On Demand—Run the report upon saving the configuration. |
Title | Title displayed at the top of the report. |
Description | Description for the configuration. |
Properties | |
Company Name | Company name displayed in the report. |
Header Comment | Page header to appear on reports with page format, like PDF or MS Word. |
Footer Comment | Page footer to appear on reports with page format: • Report Title—Use the report title in the footer. • Custom—Use the specified string in the footer. |
Title Page Logo | Logo to appear on the title page of the report: • No Logo • Custom—Upload a logo file. Note: The report generator supports GIF, JPG, and PNG files. The Windows output format also supports WMF files. |
Header Logo | Logo to appear in the page header on reports with page format: • No Logo • Custom—Upload a logo file. |
Report Scope | |
Time Period | Select a time period. Not Used means all available data is included in the report, regardless of time period. Absolute means you specify precise dates and hours. The other options are self-explanatory. |
Direction | • Inbound • Outbound Note: Shift-click to select both inbound and outbound. |
Report Type | |
Report Type | Select Event Activity and DDoS Attack Activity queries to include in the report. System Event Activity queries are based on the system event log. DDoS Attack Activity queries are based on the DDoS attack log. For DDoS Attack Activity queries, you can specify whether to include all SPPs, one or more specified SPPs, one or more SPP policies, or the default subnet. Shift-click to select multiple SPPs or SPP policies. |
Report Format | |
Top values in ranked reports (first variable) | In ranked reports, (“top x” report types, such as Top Attack Type), you can specify how many items from the top rank are included in the report. For example, you can set the Top Attack URLs report to include up to 30 of the top x denied URLs. The remaining results are combined under “Others.” Note: Reports that do not include “Top” in their name display all results. Changing the ranked reports values does not affect these reports. |
Top values in ranked reports (second variable) | Some ranked reports rank two aspects. For example, the Top Sources By Top Destination report ranks top source IP addresses for each of the top destination IP addresses. For these double-ranked reports, you can also configure the rank threshold of the second aspect. |
Include Summary Information | Select to include a report summary page. |
Include Table of Contents | Select to include a table of contents. |
Schedule | |
Schedule | If configuring a scheduled report, use the controls to specify when to run the report. |
Output | |
File Output, Email Output | • HTML • Text • PDF • MS Word • MHT (MIME HTML) |