Figure 93: SNMP trap receivers configuration page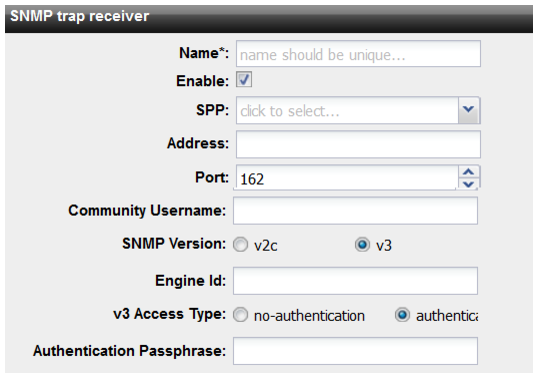


Settings | Guidelines |
Name | Identifies this SNMP trap receiver in the list of receivers. |
Enable | Enable the configuration. |
SPP | Select the SPP for the configuration. |
Address | IP address of the SNMP manager that receives attack log traps. |
Port | Listening port of the SNMP manager. The default value is 162. |
Community Username | String that specifies the SNMP community to which the FortiDDoS system and the SNMP manager at the specified address belong. |
SNMP Version | • v2c • v3 |
SNMPv3 | |
Engine ID | Engine ID that uniquely identifies the SNMP agent. |
v3 Access Type | • No authentication • Authentication • Privacy |
Authentication Passphrase | If authentication is required, specify the authentication passphrase configured on the SNMP manager. |
Privacy Passphrase | If privacy is required, specify the privacy passphrase configured on the SNMP manager. |