FortiDDoS compared with conventional network behavior analysis
FortiDDoS is a hardware-based NBA solution. Unlike software-based solutions, it maintains normal levels of processing and data throughput during denial of service attacks.
FortiDDoS appliances are powered by one or more purpose-built FortiASIC-TP2 traffic processors that maintain massive connection tables and still perform with the lowest latency in the industry. Each FortiASIC-TP2 processor maintains the following resources:
• Source table with 1,000,000 rows. This table tracks the packet rate for every source IP address and is used for “per-source” thresholds.
• Destination table with 1,000,000 rows. This table tracks the packet rate for every destination IP address and is used for “per-destination” thresholds.
• Connection (session) table with 1,000,000 rows. This table tracks the status of every active TCP session. Connections are identified using the 4-tuple of Source IP Address, Source Port, Destination IP Address, and Destination Port. It is used for connection count and connection rate thresholds.
• Legitimate IP address table with 2,000,000 rows. This table tracks every IP address that has successfully created the TCP 3-way handshake. Entries expire after 5 minutes, so IP addresses are regarded as recently known to be legitimate.
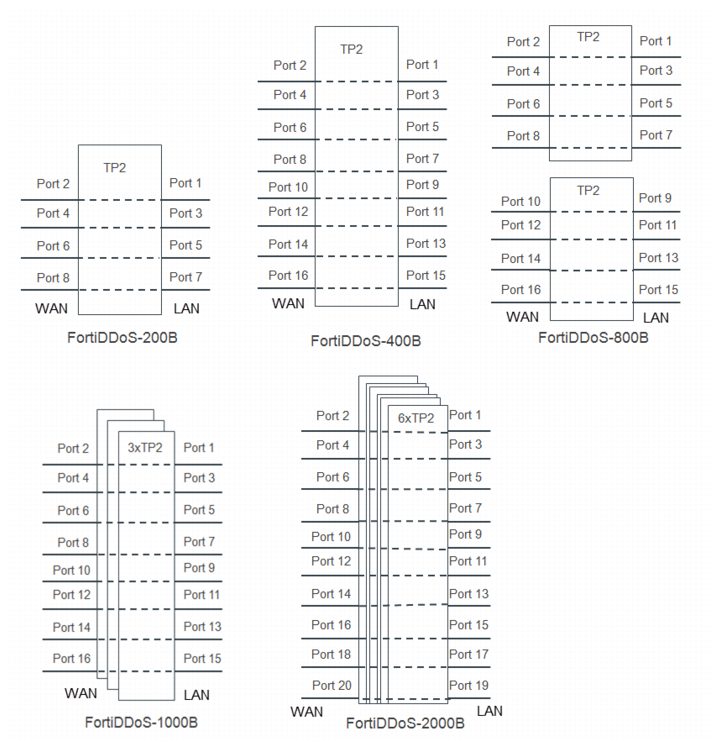
Figure 3 illustrates the number of FortiASIC-TP2 traffic processors for each FortiDDoS appliance model. Note the following:
• FortiDDoS 200B and FortiDDoS 400B—These models have 1 TP2.
• FortiDDoS 800B—These models have 2 TP2s. Interfaces 1-8 are bound to one TP2, and interfaces 9-16 are bound to the other.
• FortiDDoS 1000B and FortiDDoS 2000B—The FortiDDoS 1000B has 3 TP2s, and the FortiDDoS 2000B has 6 TP2s. Sessions are distributed among the TP2s using a hash-based load balancing algorithm. For TCP/UDP traffic, the hash includes Source IP / Source Port / Destination IP / Destination Port / Protocol. For non-TCP/non-UDP traffic, the hash includes Source IP / Destination IP / Protocol.
With its massive computing power, the FortiDDoS system maintains the magnitude of bidirectional traffic data that security administrators need to prevent DDoS attacks. The system uses counters, historical data, and predictive models to enforce intelligent rate limits based on granular Layer 3, Layer 4, and Layer 7 parameters and aggregations.
The result is excellent security, fewer false positives, and visibility into key trends.