Figure 98: DDoS Attack Log page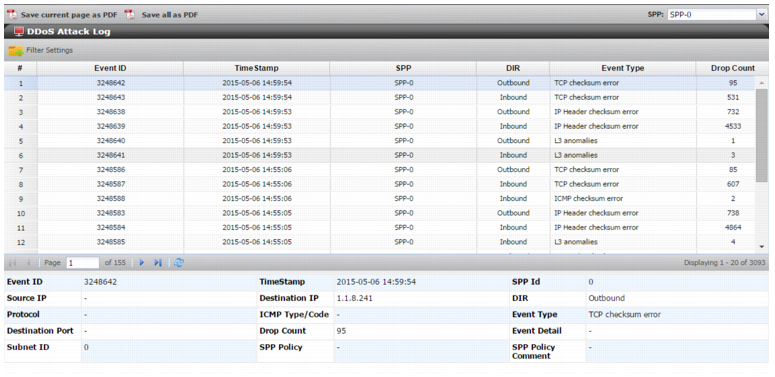

Column | Example | Description |
Event ID | 462380959 | Log ID. |
Timestamp | 2015-05-05 16:31:00 | Log timestamp. |
SPP ID | 0 | SPP ID. |
Source IP | - | Source IP address. |
Destination IP | 74.255.0.253 | Destination IP address. |
DIR | Inbound | Direction: Inbound, Outbound. |
Protocol | 6/tcp | Protocol number. |
ICMP type/code | - | ICMP type/code number. |
Event Type | SYN flood | Event type. |
Destination port | - | Destination port number. |
Drop count | 14 | Packets dropped per this event. |
Event Detail | - | Reason string. |
Subnet ID | 0 | Subnet ID. |
SPP Policy | - | SPP policy: SPP-0, SPP-1, SPP-2, SPP-3, SPP-4, SPP-5, SPP-6, SPP-7. |
SPP Policy comment | - | SPP policy comment. |

Category | Event Type | Description |
Layer 3 | ||
ACL | Protocol denied | A global ACL rule or SPP ACL rule has denied the traffic for the specified reason: • Service (protocol) ACL • Service (fragment) ACL • Geolocation ACL • Source address ACL • The FortiGuard IP Reputation list. • Local address anti-spoofing rules. |
Fragment denied | ||
Denied: Geo-location | ||
Denied: IP address | ||
Denied: IP reputation | ||
Denied: Local address anti-spoof | ||
Header Anomaly | IP header checksum error | Invalid IP header checksum. |
Source IP==dest IP | Identical source and destination IP addresses (LAND attack). | |
Source/dest IP==localhost | Source/destination address is the local host (loopback address spoofing). | |
IP header anomaly, L3 anomalies | An IP packet detected with one or more of the following anomalies: • IP version other than IPv4 or IPv6 • Invalid header length (less than 5 words) • EOP (End of Packet) before 20 bytes of IPv4 data • Total length less than 20 bytes • EOP comes before the length specified by Total Length • End of Header before the data offset (while parsing options) • Length field in the LSRR or SSRR IP option is other than (3+(n*4)) where n is a value greater than or equal to 1 • Pointer in the LSRR or SSRR IP option is other than (n*4) where n is a value greater than or equal to 1 | |
Rate Flood | Protocol flood | Effective rate limit for the protocol has been reached. |
Fragment flood | Effective rate limit for the fragment threshold has been reached. | |
Source flood | • Effective rate limit for the most-active-source threshold has been reached. • Slow connection attack detected and “Source blocking for slow connections” enabled. | |
Destination flood | Effective rate limit for the most-active-destination threshold has been reached. | |
Internal Reason | ST: Hash attack | An issue with the source tracking (ST) table or destination tracking (DT) table. For example: there are excessive hash collisions, the system is out of memory, or there is some other problem with internal FortiDDoS logic or memory. If FortiDDoS drops packets for this reason, contact Fortinet for assistance. |
ST: Out of memory | ||
DT: Hash attack | ||
DT: Out of memory | ||
Layer 4 | ||
ACL | TCP Port denied | An SPP ACL rule has denied the traffic. |
UDP Port denied | ||
ICMP Port denied | ||
Header Anomaly | TCP checksum error, UDP checksum error, ICMP checksum error | Invalid TCP, UDP, or ICMP checksum. |
TCP invalid flag combination | Invalid TCP flag combination. Urgent flag is set then the urgent pointer must be non-zero. SYN, FIN or RST is set for fragmented packets. | |
L4 anomalies | Data offset is less than 5 for a TCP packet. EOP (End of packet) is detected before the 20 bytes of TCP header. EOP before the data offset indicated data offset. Length field in TCP window scale option is a value other than 3. Missing UDP payload. Missing ICMP payload. | |
State Anomaly | State Anomalies: Outside window | The TCP sequence number of a packet was outside the acceptable window. Violations are tracked when the SPP setting seq-validation is enabled. |
State Anomalies: Foreign packet | A foreign packet is a TCP packet that does not belong to any known connections. Foreign packets are tracked when the SPP setting foreign-packet is enabled. | |
State Anomalies: State transition error | The state of the TCP packet received was not consistent with the expected state. State transition anomalies are tracked when the SPP setting state-transition-anomalies-validation is enabled. | |
Rate Flood | SYN Flood | Effective rate limit for the syn threshold has been reached. |
SYN Flood From Source | Effective rate limit for the syn-per-src threshold has been reached. | |
Excessive TCP Packets Per Destination flood | Effective rate limit for the syn-per-dst threshold has been reached. | |
Effective rate limit for the ack-per-dst threshold has been reached. | ||
Effective rate limit for the rst-per-dst threshold has been reached. | ||
Effective rate limit for the fin-per-dst threshold has been reached. | ||
Effective rate limit for the estab-per-dst threshold has been reached. | ||
TCP zombie flood | Effective rate limit for the new-connections threshold has been reached. FortiDDoS has determined that an attack is originating from IP addresses it formerly determined to be legitimate. “Zombies” are systems that are unwitting participants in an attack due to infection from a virus or a worm. | |
TCP port flood | Effective rate limit for the port has been reached. | |
UDP port flood | Effective rate limit for the port has been reached. | |
ICMP type/code flood | Effective rate limit for the ICMP type/code has been reached. | |
Excessive Concurrent Connections Per Source | Effective rate limit for the concurrent-connections-per-source threshold has been reached. | |
Excessive Concurrent Connections Per Destination | Effective rate limit for the concurrent-connections-per-destination threshold has been reached. | |
Internal Reason | TCP SM: Hash Attack, TCP SM: Out of memory | An issue with the TCP state machine (SM) table. For example: there are excessive hash collisions, the system is out of memory, or there is some other problem with internal FortiDDoS logic or memory. If FortiDDoS drops packets for this reason, contact Fortinet for assistance. |
Layer 7 | ||
ACL | URL Denied, HTTP L7 Host Deny, HTTP L7 Cookie Deny, HTTP L7 Referer Deny, HTTP L7 User Agent Deny | An SPP ACL rule has denied the traffic. |
Header Anomaly | Invalid HTTP Method, Undefined HTTP Method Anomaly | Packets dropped due to the unknown-opcode-anomaly rule (Global Settings > Settings page). |
HTTP Version Anomaly | Packets dropped due to the invalid-opcode-anomaly rule (Global Settings > Settings page). | |
Rate Flood | HTTP Method flood | Effective rate limit for a particular HTTP method threshold has been reached. |
URL flood | Effective rate limit for a particular URL threshold has been reached. | |
Host, Referer, Cookie, User-Agent flood | Effective rate limit for a particular Host, Referer, Cookie, or User-Agent threshold has been reached. | |