Captive portal
The following section describes how you can use FortiAuthenticator to grant remote users access to certain portions of the network using delegated authentication through a captive portal. Authentication requires the user to associate their device with the guest SSID as published by the FortiGate wireless controller.
The FortiGate facilitates access control by redirecting the user's web browser to one of the FortiAuthenticator's captive portals. As such, some FortiGate configuration is required.
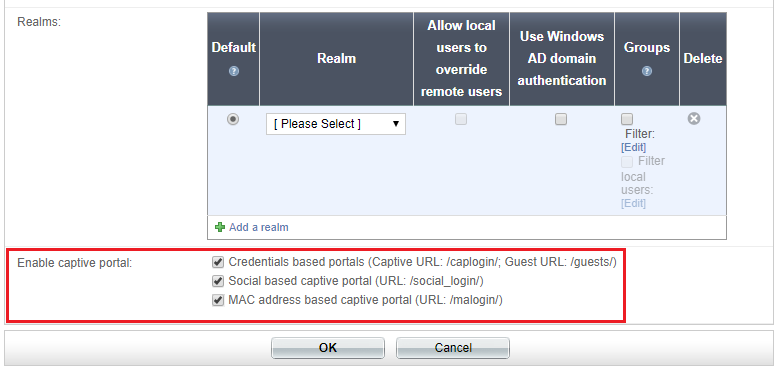
The following captive portal authentication options are available:
To enable each captive portal:
Captive portal access is enabled on a per-FortiGate basis through the RADIUS client configuration at
Authentication > RADIUS Service > Clients > Create New.
Options are available to Enable captive portal for each individual portal:
General
General captive portal configuration is available under Authentication > Captive Portal > General.
Credentials portal
The credentials portal requires known users (users who already have an account) to authenticate using their credentials (password and/or token code). The goal is to restrict access to a set of pre-authorized users only.
The credentials portal administrator must indicate which of the profiles to use for user authentication. For environments where there is one FortiWifi with multiple access points (AP), the administrator can specify a list of IP addresses for all the APs.
When the user is redirected to the credentials portal login page, they must enter their username and password, and (optionally) their FortiToken passcode. Upon successful login, the user is redirected to the webpage originally requested.
Social portal
Social Wifi authentication allows FortiAuthenticator to utilize third-party user identity methods (social sites, valid e-mail address, or phone number) to authenticate users into a wireless guest network.
The goal is to provide some traceability of users without requiring the heavy overhead of creating guest accounts.
Note that social based captive portal must be enabled on at least one RADIUS client under Authentication > RADIUS Service > Clients.
Each third-party method can be enabled or disabled on an individual basis under Authentication >
Captive Portal > General. Supported third-party authentication methods are described in the table below.
| Third-party method | Method description | |
|---|---|---|
| Google + |
Log-in using Google+ is an option for Google users, utilizing the OAUTH2 protocol described here: https://console.developers.google.com/start. Once logged in, the user can Add to Circles with the organization. |
|
|
Log-in via Facebook is known as "Facebook Connect" and is described here: https://developers.facebook.com/products/login. Once logged in, the user can Like the organization's Facebook page. |
||
|
Log-in via Linkedin is supported using the OAUTH2 protocol as described here: https://developer.linkedin.com/documents/authentication. Once logged in, the user can Connect with the organization. |
||
|
Log-in via Twitter is supported as described here: https://developer.twitter.com. Once logged in, the user can Follow the organization. |
||
| Form-based authentication | Similar to the existing Self-registration page, it is possible to register by supplying user details. It is also possible to register using minimal (configurable) information, for example: e-mail or mobile-only. Such information is commonly gathered in short-term transient use locations such as airports and coffee shops. | |
| SMS-based authentication | In SMS-based authentication, the user is redirected to a registration portal which requests a valid mobile phone number. When the user enters their number, a passcode is sent to their mobile device. The user then enters this passcode at the authentication screen to successfully authenticate. | |
| Email-based authentication | Email-based authentication is similar to SMS-based authentication, except that the user enters their email address instead of their mobile phone number. A passcode is then sent to the user's email address. The user enters this passcode into the captive portal registration page. | |
Account expiry
Account expiry can be configured for social and MAC Address portals under Authentication > Captive Portal >
General. Set the desired timeout next to Account expires after.
Account expiry is not available for the Credentials portal.
MAC address portal
This feature is particularly useful in situations where only the identity of the user is important, for example:
- Wireless guest networks
- Retail environments
- Transient access (airports, hotels, etc.)
The purpose is to identify and authenticate users with minimal interaction from the user, with some traceability of the users. This authentication method is less disruptive and therefore provides a better user experience.
With MAC address authentication enabled, the user attempts to open a web browser but is intercepted by the FortiGate wireless controller, and redirected to the FortiAuthenticator portal configured to record the user's MAC address (without requiring any user interaction). The user is then redirected to the webpage originally requested.
FortiWLC wireless controller
Enable Support FortiWLC social/credential captive portal to configure FortiWLC wireless controller captive portal firewall pinhole addresses for social authentication.
Access control
The Access Control page under Authentication > Captive Portal provides a consolidated view of which RADIUS client has access to which captive portal(s).
Replacement messages
Custom login pages for authentication are configurable on a per device, location, or organization basis, allowing the administrator to customize content specific to a brand identity. See Authentication > Captive Portal > Replacement Messages.
To edit a replacement message:
- Select a message in the replacement message list.
- Edit the plain text or HTML code in the lower right pane, or select the Open in new window icon to edit the message in a new browser window.
- Select Save to save your changes.
- Select Restore Default to restore the message to its default value if you made an error while editing the message.
Manage images
Images can be managed by selecting Manage Images in the Replacement Messages window. Images can also be added, edited, and deleted.
To add an image:
- In the Manage Images screen, select Create New.
- Enter a name for the image in the Name field.
- Select Choose File, find the GIF, JPEG, or PNG image file that you are adding, and select Open.
- Select OK to add the image.
The maximum image size is 65kB.
To edit an image:
In the manage images screen, select an image and select Edit.
- In the Edit Image window, edit the image name and file as required.
- Select OK to apply your changes.
To delete an image:
- In the Manage Images screen, select an image and select Delete.
- Select Yes, I’m sure in the confirmation window to delete the image.
Captive portal communication workflow
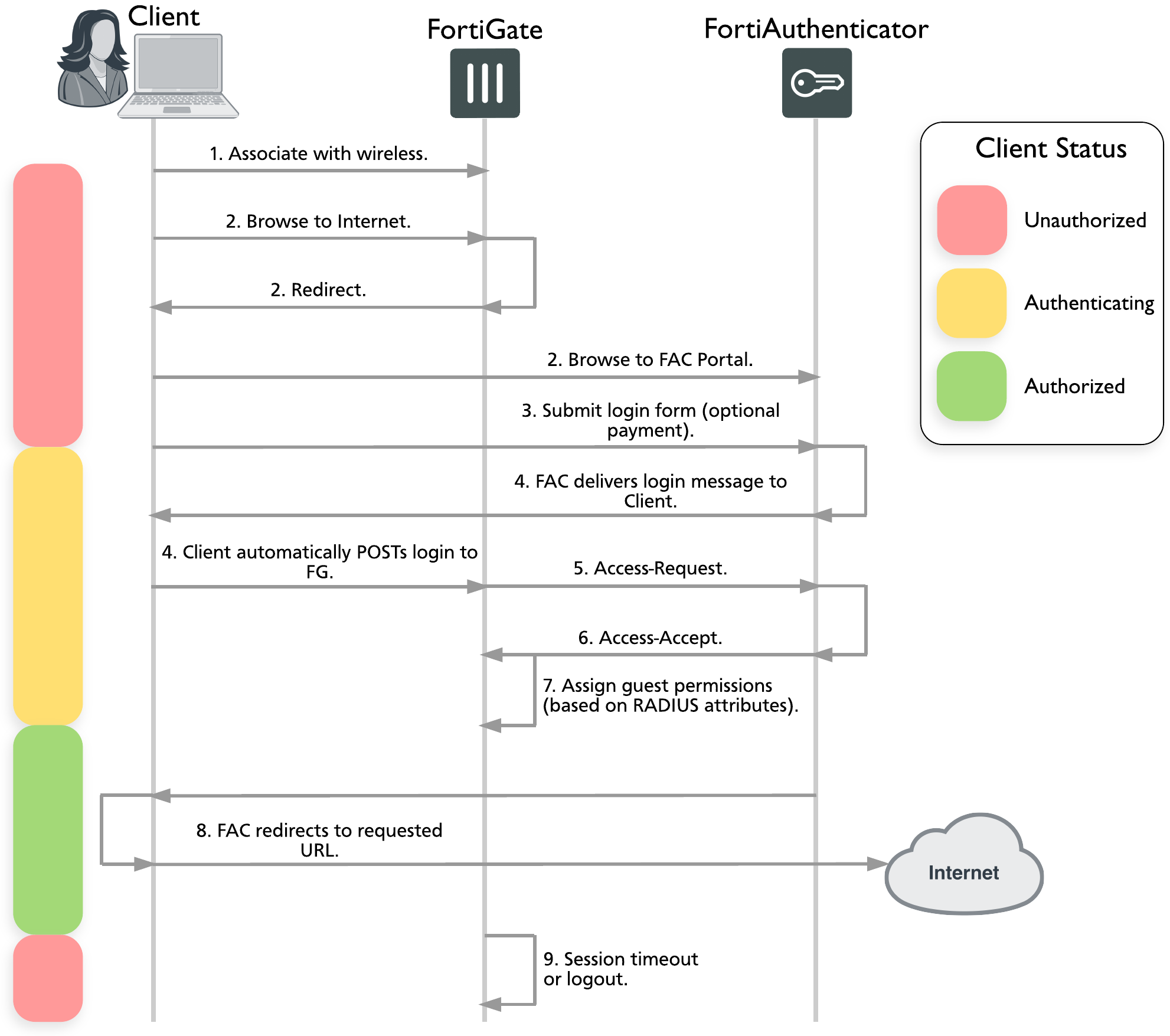
- The client associates their Wi-Fi device to the guest SSID as published by the FortiGate wireless controller.
- The client opens a browser. Based on the configured home page or requested webpage, the initial HTTP traffic is intercepted by the FortiGate wireless controller and redirected to the FortiAuthenticator web login page defined in the FortiGate captive portal profile.
- The client enters their user credentials on the FortiAuthenticator web login page.FortiAuthenticator performs any pre-authorizationn checks that are required and displays the login message to the guest user. If the client does not have credentials, there may (depending on configuration) be an option to purchase login time.
- The login message instructs the guest user’s browser to submit the user credentials directly to the FortiGate as HTTPS POST for authentication processing.
- When the FortiGate receives the client credentials in the HTTPS POST, it sends a RADIUS Access-Request to the FortiAuthenticator RADIUS server to authenticate the user.
- FortiAuthenticator validates the Access-Request message using its user database which can either be local or remote (LDAP/RADIUS).
- Based on the results of the authentication and authorization processing, FortiAuthenticator responds with either an Access-Accept or Access-Reject message. If the authentication is successful, the Access-Accept message contains one or more RADIUS attributes to define the context of the client session. These attributes can include, but are not limited to: the session duration, bandwidth, and access permissions. When the FortiGate receives the Access-Accept message, it changes the role of the client session allowing the device access to the network.
- Following a successful authentication and initiation of the user session, the client is redirected to the originally requested URL, which should now be accessible.
- Based on the Session-Timeout received in the original Access-Accept packet from FortiAuthenticator, the FortiGate counts down the remaining time that is valid for the current guest user session. When the time has expired, or if the user manually terminates the session, FortiGate terminates the session.
FortiGate configuration
In order to allow redirection to an external captive portal and also allow the supply of identifying information about the requesting IP, some FortiGate configuration is required. The example below is configured using the CLI, with the following attributes:
- WAN 1 = Internet
- FortiAuthenticator IP = 192.168.0.122
- Wireless users connecting to "Fortinet" SSID are on the network 10.10.x.x.
Additional non-standard commands to enable the feature are provided in red.
Configuring RADIUS
config user radius
edit "FAC_4.0"
set server "192.168.0.122"
set secret ENC PGTVcRMZH5mFV2aWl1A1Kbqsr3ZAKcZuEdK5Jsx+2h87uBjyWR1wuU2MY07k4H46ZHuLwBKAky9Zyn0RqHEPB3Cku232hFpkOOLlI2gzPnQbPeVcfhC18sxSWvk/fpgDhUTwPoGnYofl9vLrwpPzbkzvJhaXXcgsfSTuQ5wxK/5YghiLbdq04nnnTzQd8N8QjsUE5w==
next
end
|
|
Configuration of the accounting server might not be nessesary if the RADIUS Accounting is the same as the RADIUS Auth server. |
Configuring the group
config user group
edit "Wireless_Auth"
set member "FAC_4.0"
next
end
Configuring VAP
Configure captive portal security with an external Portal rather than the native on-FortiGate portal.
config wireless-controller vap
edit "fortinet"
set vdom "root"
set security captive-portal
set selected-usergroups "Wireless_Auth"
set intra-vap-privacy enable
set local-switching disable
set external-web "http://192.168.0.122/caplogin
next
end
Configuring the FortiAuthenticator address group
Configure the FortiAuthenticator address or group to use as an exemption rule in the firewall policy. This is to allow traffic to flow to the FortiAuthenticator portal to enable authentication when the user is not yet authenticated. This group may also include any servers used to host images referenced on the FortiAuthenticator portal.
config firewall address
edit "FortiAuthenticator"
set type iprange
set associated-interface "internal"
set start-ip 192.168.0.122
set end-ip 192.168.0.123
next
end
|
|
If Social Wifi is enabled, this exemption group will need to consist of all Facebook, Google, LinkedIn, and/or Twitter servers used in the authentication process. |
Configuring the firewall policy
In these firewall policies, an exemption is made to allow access to the FortiAuthenticator (rule 21) and to external Internet resources (rule 17, "For_SocialWiFi"), which may include content embedded on the portal login page (images, videos, organization website), or may be used in the future to enable exemption for Social Wifi (Google, Facebook, LinkedIn, Twitter).
config firewall policy
edit 21
set srcintf "fortinet"
set dstintf "internal"
set srcaddr "all"
set dstaddr "FortiAuthenticator"
set action accept
set schedule "always"
set service "ALL"
set captive-portal-exempt enable
next
:
:
:
edit 17
set uuid 6d71b2b4-4efd-51e4-a21f-272dd0bcdcd9
set srcintf "fortinet"
set dstintf "wan1"
set srcaddr "all"
set dstaddr "For_SocialWiFi"
set action accept
set schedule "always"
set service "ALL"
set captive-portal-exempt enable
set nat enable
next
end
For the credentials portal, the administrator must indicate which of the profiles to use for user authentication. For environments where there is one FortiWifi with multiple access points (AP), the administrator can specify a list of IP addresses for all the APs.
When the user is redirected to the Credentials portal login page, they must enter their username and password, and (optionally) their FortiToken passcode. Upon successful login, the user is redirected to the webpage originally requested.