Self-service portal
Configure general self-service portal options, including access control settings, self-registration options, replacement messages, and device self-enrollment settings.
General
To configure general self-service portal settings, go to Authentication > Self-service Portal > General.
The following settings can be configured:
| Default portal language | Select from several default portal language packs from the dropdown menu. | |
| Add a Language Pack |
Upload a different language pack. Obtain additional translation packs from the Fortinet Support website if you need to translate to your local language. |
|
| Site name | Enter a name that is used when referring to this site. If left blank, the default name will be the site DNS domain name or IP address. | |
| Email signature | Add a signature to be appended to the end of outgoing email messages. | |
| Allow users to change their password | Enable to allow local and/or remote users the ability to change their own password. | |
Access control
To configure self-service portal access settings, go to Authentication > Self-service Portal > Access Control.
The following settings can be configured:
Self-registration
When self-registration is enabled, users can request registration through the FortiAuthenticator login page. Self-registration can be configured so that a user request is emailed to the device administrator for approval.
When the account is ready for use, the user receives an email or SMS message with their account information.
To enable self-registration:
- Go to Authentication > Self-service Portal > Self-registration.
- Select Enable to enable self-registration.
- Optionally, configure the following settings:
- Select OK to apply your changes.

| Require administrator approval | Select to require that an administrator approves the user. | |
| Enable email to freeform addresses | Select to send self-registration requests to the email addresses entered in the Administrator email addresses field. | |
| Select User Groups allowed to approve new user registrations | Select to send self-registration requests to specific user groups. Select the required approvers from the Available groups box and move them to the Chosen groups box. If enabled, the guests are given a dropdown list of approvers to choose from on the self-registration page. The FortiAuthenticator sends an approval request to that approver's email address. The list of approvers is the union of all the users/administrators who are members of the specified groups. Local, remote LDAP, and remote RADIUS groups are supported. |
|
| Account expires after | Enable to specify an expiration for self-generated accounts after they are generated. | |
| Use mobile number as username | If enabled, after a successful registration, the user’s password will be sent to them via SMS to confirm their identity. | |
| Place registered users into a group | Select a group into which self-registered users will be placed from the dropdown menu. | |
| Password creation |
Select how a password is created, either User-defined or Randomly generated. |
|
|
Send account information via |
Choose how to send account information to the user, either SMS, Email, or Display on browser page. The Display on browser page option is only available if administrator approval is not required. |
|
| SMS gateway |
Select an SMS gateway from the dropdown menu. See SMS gateways for more information. |
|
|
Required Field Configuration |
Select the fields that the user is required to populate when self-registering. Options include: First name, Last name, Email, address, Address, City, State/Province, Country, Phone number, Mobile number, Custom field 1, Custom field 2, and Custom field 3. See Custom user fields for more information. |
|
Self-registration approval
The self-registration page is a customizable replacement message. The default replacement message contains a new optional field for the self-registering guest to select an approver. The list of approvers comes from the groups specified in the configuration. The dropdown list is populated with the explicit list of group members for local groups, remote RADIUS groups, and remote LDAP groups.
Each approver in the dropdown list is designated as "Lastname, Firstname". In cases where first and last name are not available, an approver is designated as "username" instead. Disabled user accounts are excluded from the list. User accounts without a configured email address are also excluded from the list.
To approve a self-registration request:
- Select the link in the Approval Required for... email message to open the New User Approval page in your web browser.
- Review the information and select either Approve or Deny, as appropriate.
Approval is required only if Require administrator approval is enabled in the self-registration settings.
If the request is approved, FortiAuthenticator sends the user an email or SMS message stating that the account has been activated.
How a user requests registration
A user can request registration, or self-register, from the FortiAuthenticator login screen.
To request registration:
- Browse to the IP address of FortiAuthenticator.
- Select Register to open the user registration page.
- Fill in all the required fields and, optionally, fill in the Additional Information fields.
- Select OK to request registration.
Security policies must be in place on the FortiGate unit to allow these sessions to be established.
If administrator approval is not required and Display on browser page is enabled, the account details are immediately displayed to the user.
Token self-provisioning
User token self-provisioning allows users to set up their own FortiTokens without direct intervention of an administrator.
To configure token self-provisioning settings, go to Authentication > Self-service Portal > Token self-provisioning.
The following settings can be configured:
| Token Self-registration | |
|---|---|
| Allow FortiToken Hardware self-provisioning | Enable this option if you want to allow users to self-provision their own FortiToken Hardware tokens. |
| Allow FortiToken Mobile self-provisioning | Enable this option if you want to allow mobile users to self-provision their FortiToken Mobile. |
| Allow Email self-provisioning | Enable this option if you want to allow users to self-provision their FortiToken Mobile via email. |
| Allow SMS self-provisioning | Enable this option if you want to allow users to self-provision their FortiToken Mobile via SMS. |
| Allow user to request a token from Administrator at this email address | Enable this option if you want to allow users to request a new token using an email address. |
| Token Self-revocation | |
|---|---|
| Allow users to report a lost token to the Administrator at this email address | Enable this option if you want to allow users to report a lost token to a specific email address. |
| Allow users to temporarily use SMS token authentication if a mobile number was pre-configured | Enable this option if you want to allow users to switch to temporary SMS based authentication. The administrator will also be notified. |
| Allow users to temporarily use email token authentication if an email was pre-configured | Enable this option if you want to allow users to switch to temporary email based authentication. The administrator will also be notified. |
| Allow users to re-provision their FortiToken Mobile | Enable this option if you want to allow mobile users to re-provision their token. |
How a user registers a token
If enabled, a user can self-register a token from the user portal screen.
To self-register:
- Browse to the IP address of the user portal and log in.
- Go to My Account > User > Register Token to open the token registration options.
- Fill in all the required fields.
Only options that the administrator has configured under the Token Self-registration options will be available.
- Select OK to register token.
If a token is already assigned to the user, the token registration page will display the token along with its serial number.
How a user reports a lost token
A user can report a lost token (mobile or physical) from the user portal screen.
To report lost token:
- Browse to the IP address of the user portal.
- Select I lost my token.
The user will be directed to a page warning them that their account will be locked and the administrator will be notified. Select OK to continue.
- Select the preferred option.
Only options that the administrator has configured under the Token Self-revocation options will be available.
- Select OK to continue.
Replacement messages
The replacement messages list allows you to view and customize replacement messages, and manage images.
Go to Authentication > Self-service Portal > Replacement Messages to view the replacement message list.
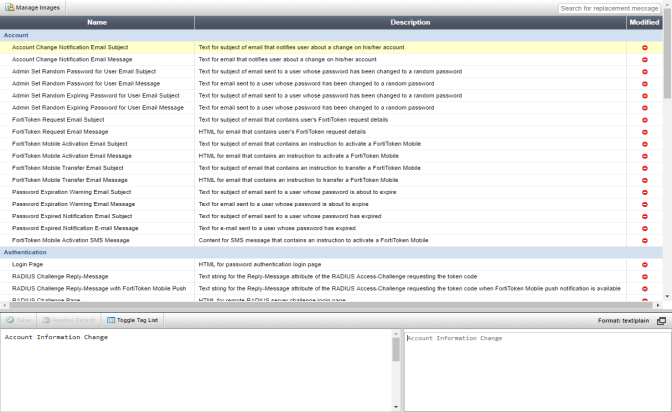
The replacement messages are split into seven categories: Account, Authentication, Device Certificate Enrollment, Password Reset, User Registration, SAML IdP, and SAML SP (FSSO).
|
|
The two pre-authentication replacement messages under Authentication are only available once pre-authentication has been enabled under System > Administration > System Access. |
Selecting a specific message will display the text and HTML or plain text of the message in the lower half of the content pane.
Selecting Toggle Tag List will display a table of the tags used for that message atop the message’s HTML or plain text box.
To edit a replacement message:
- Select a message in the replacement message list.
- Edit the plain text or HTML code in the lower right pane, or select the Open in new window icon to edit the message in a new browser window.
- Select Save to save your changes.
- Select Restore Default to restore the message to its default value if you made an error while editing the message.
Manage images
Images can be managed by selecting Manage Images in the Replacement Messages window. Images can also be added, edited, and deleted.
To add an image:
- In the Manage Images screen, select Create New.
- Enter a name for the image in the Name field.
- Select Choose File, find the GIF, JPEG, or PNG image file that you are adding, and select Open.
- Select OK to add the image.
The maximum image size is 65kB.
To edit an image:
In the manage images screen, select an image and select Edit.
- In the Edit Image window, edit the image name and file as required.
- Select OK to apply your changes.
To delete an image:
- In the Manage Images screen, select an image and select Delete.
- Select Yes, I’m sure in the confirmation window to delete the image.
Device self-enrollment
Device certificate self-enrollment is a method for local and remote users to obtain certificates for their devices. It can be used to enable EAP-TLS for BYOD configurations, or for VPN authentication. For example:
- A user brings their tablet to a BYOD organization.
- They log in to FortiAuthenticator and create a certificate for the device.
- With their certificate, username, and password they can authenticate to gain access to the wireless network.
- Without the certificate, they are unable to access the network.
|
|
EAP-TLS is a bidirectional certificate authentication method; the client and the FortiAuthenticator EAP need to have matching certificates from the same CA. |
To enable device self-enrollment and adjust self-enrollment settings, go to Authentication > Self-service Portal > Device Self-enrollment and select Enable user device certificate self-enrollment.
|
|
SCEP must be enabled to activate this feature, see SCEP. |
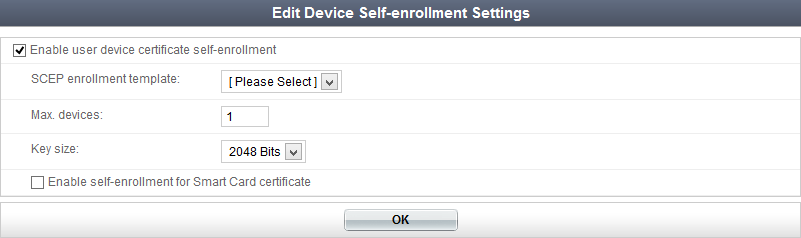
The following settings can be configured:
Select OK to apply any changes you have made.