If you already have LDAP or RADIUS servers configured on your network, FortiAuthenticator can connect to them for remote authentication, much like FortiOS remote authentication.
If you have existing LDAP servers, you may choose to continue using them with FortiAuthenticator by configuring them as remote LDAP servers.
|
|
When entering the remote LDAP server information, if any information is missing or in the wrong format, error messages will highlight the problem for you. |
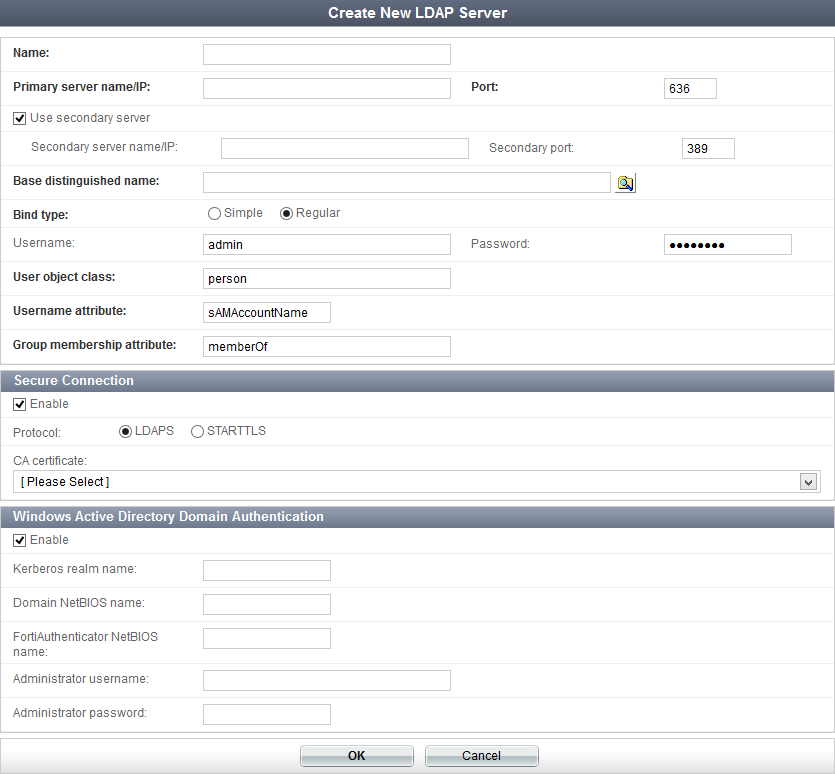
| Protocol | Select LDAPS or STARTLS as the LDAP server requires. |
| CA Certificate | Select the CA certificate that verifies the server certificate from the drop-down list. |
| Kerberos realm name | Enter the domain’s DNS name in uppercase letters. |
| Domain NetBIOS name | Enter the domain’s DNS prefix in uppercase letters. |
| FortiAuthentication NetBIOS name | Enter the NetBIOS name that will identify the FortiAuthenticator unit as a domain member. |
| Administrator username | Enter the name of the user account that will be used to associate the FortiAuthenticator unit with the domain. This user must have at least Domain User privileges. |
| Administrator password | Enter the administrator account’s password. |
When you are finished here, go to Authentication > RADIUS Service > Clients to choose whether authentication is available for all Windows AD users or only for Windows AD users who belong to particular user groups that you select. See RADIUS service for more information.
You can now add remote LDAP users, as described in Remote users.
If you have existing RADIUS servers, you may choose to continue using them with FortiAuthenticator by configuring them as remote RADIUS servers.This feature can also be used to migrate away from third party two-factor authentication platforms.
|
|
When entering the remote RADIUS server information, if any information is missing or in the wrong format, error messages will highlight the problem for you. |
| Name | Enter the name for the remote RADIUS server on FortiAuthenticator. |
| Primary Server | Enter the server name or IP address, port and secret in their requisite locations to configure the primary server. |
| Secondary Server | Optionally, add redundancy by configuring a secondary server. |
| User Migration | Select Enable learning mode to record and learn users that authenticate against this RADIUS server. This option should be enabled if you need to migrate users from the server to the FortiAuthenticator. Select View Learned Users to view the list of learned users. See Learned RADIUS users. |