Web application firewall configuration overview
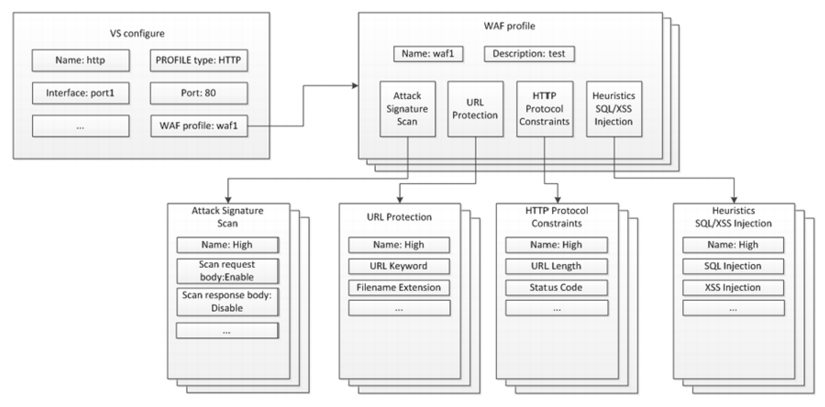
Figure 50 shows the relationship between WAF configuration elements. A WAF profile comprises a Web Attack Signature policy, URL Protection policy, HTTP Protocol Constraint policy, and SQL/XSS Injection Detection policy. The profile is applied to a load balancing virtual server, so all traffic routed to the virtual server is subject to the WAF rules. WAF profiles can be applied to HTTP and HTTPS virtual servers but not HTTP Turbo virtual servers.
Predefined configuration elements
The FortiADC WAF includes many predefined configuration elements to help you get started. It includes predefined WAF profiles, predefined Web Attack Signature policies, predefined HTTP Protocol Constraint policies, and predefined SQL/XSS Injection Detection policies.
Severity
The severity ratings for predefined Web Attack Signatures and the default severity rating for feature options like SQL/XSS Injection Detection are based on the Open Web Application Security Project (OWASP)
Risk Rating Methodology. In order to harmonize the significance of severity levels in logs, we recommend you use this methodology to assign severity for any custom elements you create.