Web application firewall basics
A web application firewall (WAF) is a security policy enforcement point positioned between a client endpoint and a web application. The primary purpose is to prevent attacks against the web servers. A WAF is deployed separately from the web application so that the process overhead required to perform security scanning can be offloaded from the web server, and policies can be administered from one platform to many servers.
A WAF uses methods that complement perimeter security systems, such as the FortiGate next-generation firewall. The FortiADC WAF module applies a set of policies to HTTP scanpoints, which are parsed contexts of an HTTP transaction.
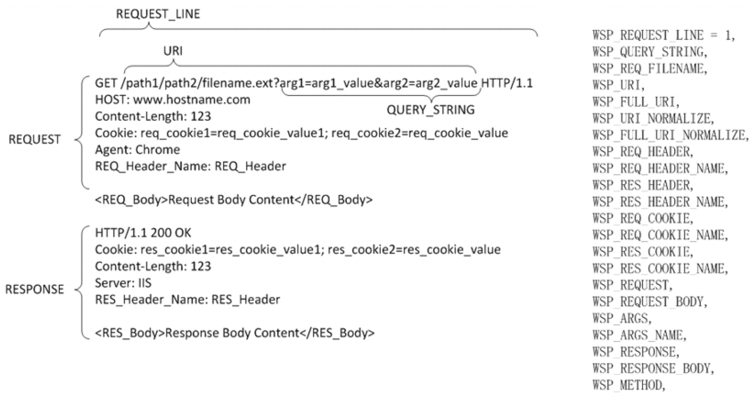
Figure 49 illustrates the scanpoints. In the WAF policy configurations, you have options to enable rules to detect attacks at the request line, query string, filename, URI, request headers, request body, response code, or response body.
In particular:
• Web Attack Signature policy—The signature database includes signatures that can detect known attacks and exploits that can be found in 22 scanpoints. In your policy configuration, you choose classes of scanpoints to process: HTTP Headers, HTTP Request Body, and HTTP Response Body.
• URL Protection policy—This policy enables you to create rules that detect patterns in the URI or the file extension.
• HTTP Protocol Constraint policy—This policy enables you to create rules that restrict URI length, HTTP method, or HTTP response code.
• SQL/XSS Injection Detection policy—This policy includes rules to detect SQL/XSS injection in the HTTP Request URI, HTTP Referer Header, HTTP Cookie Header, or HTTP Request Body.
Policy rules are enforced (action taken) when scanning is completed at four checkpoints:
• HTTP Request Header
• HTTP Request Body
• HTTP Response Header
• HTTP Response Body
If the HTTP Request Header violates a rule, and the action is Deny, the attempted session is dropped and scanning for the transaction stops. If the action is Alert, the event is logged and rules processing continues.