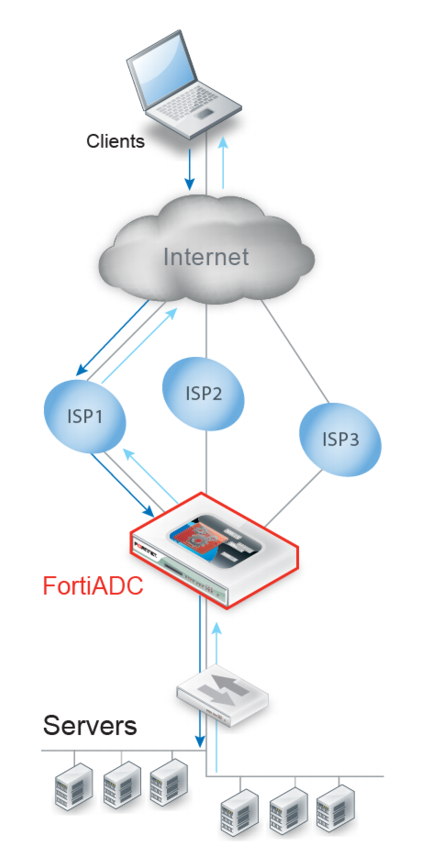
Reverse path route caching
By default, FortiADC caches a reverse path route for inbound traffic so it can forward reply packets to the ISP link that forwarded the corresponding request packet. This is useful when your site receives traffic from multiple ISP links. For example, in
Figure 90, the reverse path pointer ensures that client traffic received from ISP1 is returned through ISP1.
When reverse path caching is not enabled, the system forwards reply packets based on the results of routing lookup.
To enable/disable reverse path route caching, use the config router setting CLI command to set the rt-cache-reverse option:
FortiADC-VM # config router setting
FortiADC-VM (setting) # get
rt-cache-strict : disable
rt-cache-reverse : enable
ip-forward : enable
ip6-forward : enable
FortiADC-VM (setting) # set rt-cache-reverse disable
FortiADC-VM (setting) # end
FortiADC-VM # get router setting
rt-cache-strict : disable
rt-cache-reverse : disable
ip-forward : enable
ip6-forward : enable
The rt-cache-strict option is disabled by default. Enable it when you want to send reply packets only via the same interface that received the request packets. When enabled, source interface becomes part of the matching tuple FortiADC uses to identify sessions, so reply traffic is forwarded from the same interface that received the traffic. Normally each session is identified by a 5-tuple: source IP, destination IP, protocol, source port, and destination port.
If rt-cache-reverse is enabled, you can maintain an exceptions list for source IP addresses that should be handled differently. For example, if you configure an exception for 192.168.1.0/24, FortiADC will not maintain a pointer to the ISP for traffic from source 192.168.1.18. Reply packets will be forwarded based on the results of routing lookup.