Configuring SNAT
You use source NAT (SNAT) when clients have IP addresses from private networks. This ensures you do not have multiple sessions from different clients with source IP 192.168.1.1, for example. Or, you can map all client traffic to a single source IP address because a source address from a private network is not meaningful to the FortiADC system or backend servers.
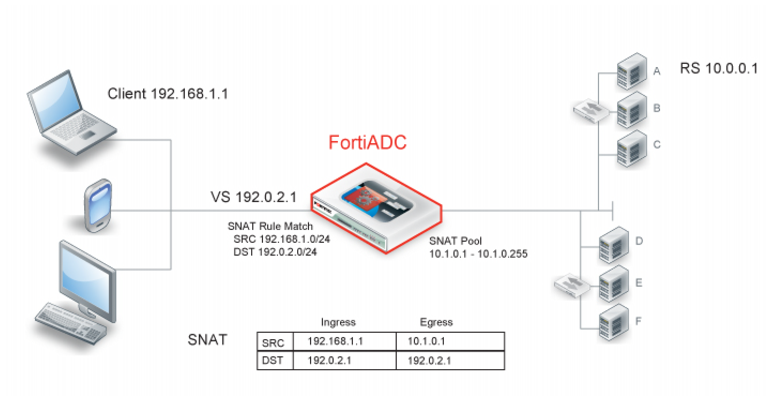
Figure 63 illustrates SNAT. The SNAT rule matches traffic with source and destination IP addresses that fall within the specified ranges. If the client request matches, the system translates the source IP address to an address from the SNAT pool. In this example, a client with private address 192.168.1.1 requests a resource from the virtual server address at 192.0.2.1 (not the real server address 10.0.0.1; the real server address is not published). The two rule conditions match, so the system translates the source IP to the next address in the SNAT pool—10.1.0.1. SNAT rules do not affect destination addresses, so the destination address in the request packet is preserved.
The system maintains this NAT table and performs the inverse translation when it receives the server-to-client traffic. Be sure to configure the backend servers to use the FortiADC address as the default gateway so that server responses are also rewritten by the NAT module.
Before you begin:
• You must know the IP addresses your organization has provisioned for your NAT design.
• You must have Read-Write permission for System settings.
To configure source NAT:
1. Go to Networking > NAT.
The configuration page displays the Source tab.
2. Click Add to display the configuration editor.
3. Complete the configuration as described in
Table 85.
4. Save the configuration.
5. Reorder rules, as necessary.
Table 85: Source NAT configuration
Settings | Guidelines |
Name | Unique name. No spaces or special characters. After you initially save the configuration, you cannot edit the name. |
Source | Address/mask notation to match the source IP address in the packet header. For example, 192.0.2.0/24. |
Destination | Address/mask notation to match the destination IP address in the packet header. For example, 10.0.2.0/24. |
Egress Interface | Interface that forwards traffic. |
Translation Type | • IP Address—Select to translate the source IP to a single specified address. • Pool—Select to translate the source IP to the next address in a pool. |
Translation to IP Address | Specify an IPv4 address. The source IP address in the packet header will be translated to this address. |
Pool Address Range | First IP address in the SNAT pool. |
To | Last IP address in the SNAT pool. |
Reordering |
| After you have saved a rule, reorder rules as necessary. The rules table is consulted from top to bottom. The first rule that matches is applied and subsequent rules are not evaluated. |