SSL offloading
SSL offloading means the ADC handles encryption processing instead of the backend servers, allowing them to dedicate resources to their own application processes.
SSL offloading results in improved SSL/TLS performance. On VM models, acceleration is due to offloading the cryptography burden from the backend server. On hardware models with ASIC chips, cryptography is also hardware-accelerated: the system can encrypt and decrypt packets at better speeds than a backend server with a general-purpose CPU.
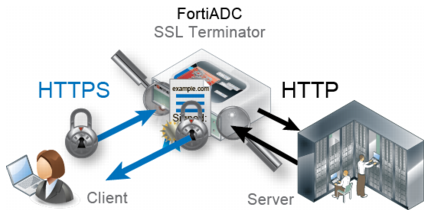
Figure 2 illustrates how FortiADC acts as the SSL/TLS terminator in HTTPS sessions. Instead of a single encrypted tunnel along the entire path from the client to a backend server, the client HTTPS request is decrypted when it reaches the FortiADC system. FortiADC then forwards unencrypted HTTP traffic to your servers. When the server replies, the server connects to the FortiADC via clear text HTTP. FortiADC then encrypts the response and forwards it via HTTPS to the client.
To enable SSL offloading, you import the X.509 v3 server certificates and private keys for the backend servers, as well as any certificate authority (CA) or intermediate CA certificates that are used to complete the chain of trust between your clients and your servers. FortiADC acts as an SSL proxy for the server, using the certificates to:
• authenticate itself to clients
• decrypt requests
• encrypt responses
When session data has been decrypted, you can use the FortiADC content rewriting and content routing rules.
When you offload the SSL burden from backend servers to an ADC, the ADC forwards data unencrypted to the servers. You must deploy the FortiADC appliance in a trusted network with direct path to the backend servers. For example, the FortiADC and the backend servers are connected through a switch and all are located physically in the same locked rack. In cases where traffic is forwarded along untrusted paths towards backend servers, you have the option to re-encrypt the data before forwarding it to the backend servers.
Table 2 lists supported TLS/SSL cipher suites. The recommended cipher suite is in bold.
Table 2: Supported cipher suites
Cipher Suite | Protocol | Key Exchange | Auth | Encryption | MAC |
SSL_RSA_WITH_RC4_128_MD5 | SSL 3.0 | RSA | RSA | RC4 | MD5 |
SSL_RSA_WITH_RC4_128_SHA | SSL 3.0 | RSA | RSA | RC4 | SHA |
SSL_RSA_WITH_DES_CBC_SHA | SSL 3.0 | RSA | RSA | DES-CBC | SHA |
SSL_RSA_WITH_3DES_EDE_CBC_SHA | SSL 3.0 | RSA | RSA | DES-CBC3 | SHA |
TLS_RSA_WITH_RC4_128_MD5 | TLS 1.0 | RSA | RSA | RC4 | MD5 |
TLS_RSA_WITH_RC4_128_SHA | TLS 1.0 | RSA | RSA | RC4 | SHA |
TLS_RSA_WITH_DES_CBC_SHA | TLS 1.0 | RSA | RSA | DES-CBC | SHA |
TLS_RSA_WITH_3DES_EDE_CBC_SHA | TLS 1.0 | RSA | RSA | DES-CBC3 | SHA |
TLS_RSA_WITH_AES_128_CBC_SHA | TLS 1.0 | RSA | RSA | AES(128) | SHA |
TLS_RSA_WITH_AES_256_CBC_SHA | TLS 1.0 | RSA | RSA | AES(256) | SHA |
TLS_RSA_WITH_AES_128_CBC_SHA256 | TLS 1.2 | RSA | RSA | AES(128) | SHA |
TLS_RSA_WITH_AES_256_CBC_SHA256 | TLS 1.2 | RSA | RSA | AES(256) | SHA |
For information on importing X.509 v3 server certificates, see
“Using certificates”.
For information on specifying certificates and a cipher suite list in HTTPS and TCPS profiles, see
“Configuring profiles”.