In this way, FortiADC bears the load for encryption processing instead of your back-end servers, allowing them to focus resources on the network application itself. This is called SSL offloading.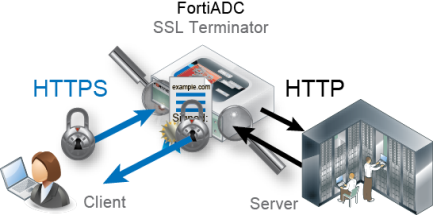


SSL offloading can be associated with improved SSL/TLS performance. In hardware models with specialized ASIC chip SSL accelerator(s), FortiADC can encrypt and decrypt packets at better speeds than a back-end server with a general-purpose CPU. |
Secure traffic between FortiADC and back-end servers when using SSL offloading. Failure to do so will compromise the security of all offloaded sessions. No attack will be apparent to clients, as SSL offloading cannot be detected by them, and therefore they will not receive any alerts that their session has been compromised. For example, you might pass decrypted traffic to back-end servers as directly as possible, through one switch that is physically located in the same locked rack, and that has no other connections to the overall network. Alternatively, configure FortiADC as an SSL switch, re-encrypting the traffic before forwarding to back-end servers. SSL offloading performance benefits will be lost, but this can be useful in cases where you are load balancing traffic that is forwarded along untrusted paths towards back-end servers. See “How to re-encrypt SSL/TLS to back-end servers”. |