How to re-encrypt SSL/TLS to back-end servers
Content routing and rewriting requires decryption. Without it, FortiADC cannot inspect and rewrite the packets’ Layer 7 content. SSL/TLS offloading provides this — the packet is available to the appliance in its decrypted state so that FortiADC can modify it. However, in some cases, you may want to re-encrypt traffic before forwarding it to the back-end servers
For example, if you are load balancing traffic and forwarding to back-end servers along untrusted paths, vital credit card and personally identifying information would be vulnerable during its back-end transit unless you re-encrypt it.
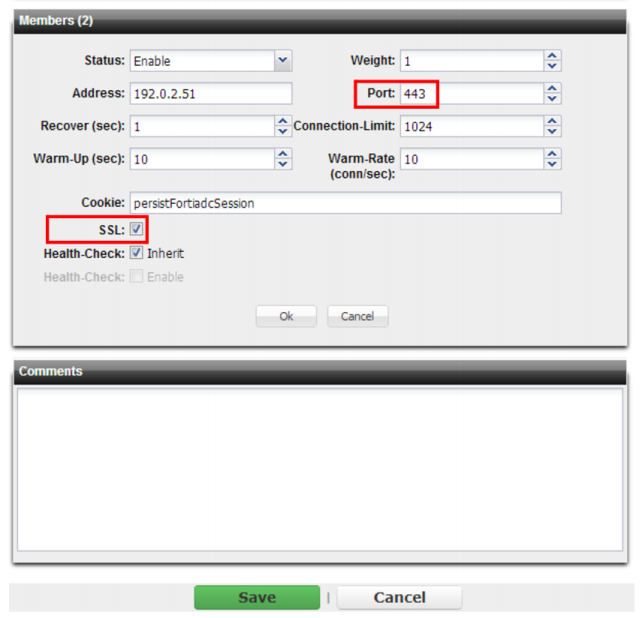
To re-encrypt the packets before forwarding to the back-end server, while configuring the server pool , configure FortiADC to act as an SSL switch by enabling SSL to Server. Also configure the listening port number (typically port 443 for HTTPS) for each entry in the pool definition.
Verify that your back-end servers are configured for encrypted connections — if they are not, the connection will fail. (Conversely, if you do
not enable
SSL to Server, you should also disable SSL/TLS on your servers.) See also
“Defining your pool of back-end servers”.