Workflow
Begin with
“How to set up your FortiWeb” for your initial deployment. These instructions will guide you to the point where you have a simple, verifiably working installation.
Ongoing use is located in the chapters after “How to set up your FortiWeb”. Once you have successfully deployed, ongoing use involves:
• Backups
• Updates
• Configuring optional features
• Adjusting policies if:
• New attack signatures become available
• Requirements change
• Fine-tuning performance
• Periodic web vulnerability scans if required by your compliance regime
• Monitoring for defacement or focused, innovative attack attempts from advanced persistent threats (APTs)
• Monitoring for accidentally blacklisted client IPs
• Using data analytics to show traffic patterns
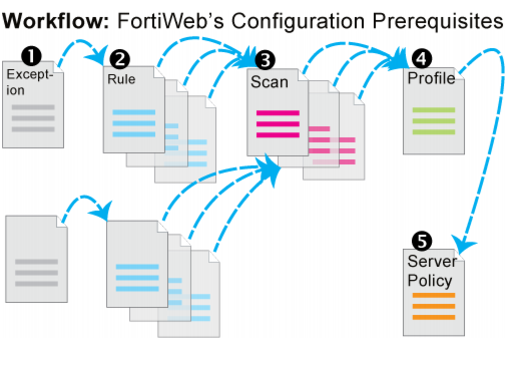
Except for features independent of policies such as anti-defacement, most features are configured
before policies. Policies link protection components together and apply them. As such, policies usually should be configured last, not first.
 Except for features independent of policies such as anti-defacement, most features are configured before policies. Policies link protection components together and apply them. As such, policies usually should be configured last, not first.
Except for features independent of policies such as anti-defacement, most features are configured before policies. Policies link protection components together and apply them. As such, policies usually should be configured last, not first. Except for features independent of policies such as anti-defacement, most features are configured before policies. Policies link protection components together and apply them. As such, policies usually should be configured last, not first.
Except for features independent of policies such as anti-defacement, most features are configured before policies. Policies link protection components together and apply them. As such, policies usually should be configured last, not first.