Configuring access profiles
Access profiles, together with ADOMs, determine administrator accounts’ permissions.
When an administrator has only read access to a feature, the administrator can access the web UI page for that feature, and can use the get and show CLI command for that feature, but cannot make changes to the configuration. There are no Create or Apply buttons, or config CLI commands. Lists display only the View icon instead of icons for Edit, Delete or other modification commands. Write access is required for modification of any kind.
In larger companies where multiple administrators divide the share of work, access profiles often reflect the specific job that each administrator does (“role”), such as user account creation or log auditing. Access profiles can limit each administrator account to their assigned role. This is sometimes called role-based access control (RBAC).
The prof_admin access profile, a special access profile assigned to the admin administrator account and required by it, does not appear in the list of access profiles. It exists by default and cannot be changed or deleted, and consists of essentially UNIX root-like permissions.

|
Even if you assign the prof_admin access profile to other administrators, they will not have all of the same permissions as the admin account. The admin account has some special permissions, such as the ability to reset administrator passwords, that are inherent in that account only. Other accounts should not be considered a complete substitute. |
If you create more administrator accounts, whether to harden security or simply to prevent accidental modification, create other access profiles with the minimal degrees and areas of access that each role requires. Then assign each administrator account the appropriate role-based access profile.
For example, for an administrator whose only role is to audit the log messages, you might make an access profile named auditor that only has Read permissions to the Log & Report area.
To configure an access profile
1. Go to System > Admin > Profile.
To access this part of the web UI, your administrator's account access profile must have Read and Write permission to items in the Admin Users category. For details, see Permissions.
2. Click Create New.
A dialog appears.
3. In Profile Name, type a unique name that can be referenced by other parts of the configuration. Do not use spaces or special characters. The maximum length is 63 characters.
4. Configure the permissions options.
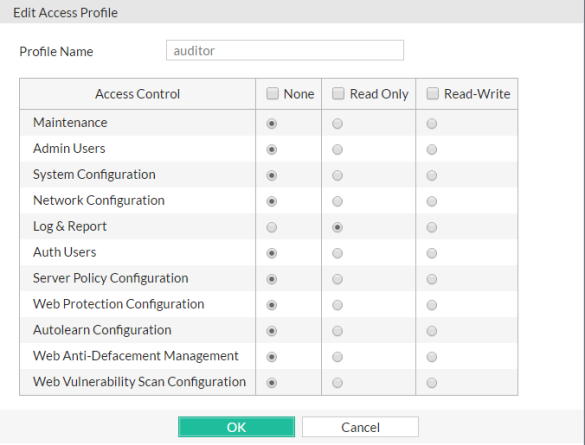
For each row associated with an area of the configuration, mark either the None, Read Only, or Read-Write radio buttons to grant that type of permission. For a list of features governed by each access control area, see Permissions.
Click the Read Only check box to select or deselect all read categories.
Click the Read-Write check box select or deselect all write categories.
Unlike the other rows, whose scope is an area of the configuration, the Maintenance row does not affect the configuration. Instead, it indicates whether the administrator can do special system operations such as changing the firmware.
5. Click OK.
See also
Open topic with navigation
