FortiWeb appliances can recognize known attacks by comparing each request to a signature. How, then, does it recognize requests that aren’t known to be an attack, or aren’t always an attack, but might be?
FortiWeb uses several methods for this:
Web applications’ administrative URLs often should not be accessible by clients on the Internet, and therefore any request for those URLs from source IP addresses on the Internet may represent an attempt to scout your web servers in advance of an attack. (Exceptions include hosting providers, whose clients may span the globe and often configure their own web applications.) Administrative requests from the Internet are therefore suspicious: the host may have been compromised by a rootkit, or its administrative login credentials may have been stolen via spyware, phishing, or social engineering.
FortiWeb appliances can compare each request URL with regular expressions that define known administrative URLs, and log and/or block these requests.
Regular expressions for suspicious requests by URL are categorized as:
Both types can be grouped into a set that can be used in auto-learning profiles.
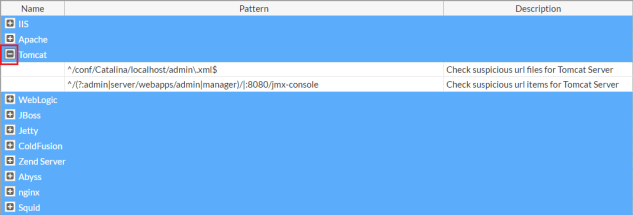
Predefined regular expressions can be used by auto-learning to detect requests that are suspicious because they are for a URL that provides administrative access to the web server, servlet, or web application, such as:
/admin.php
/conf/Catalina/localhost/admin.xml
or access to its back-end cache, data files, or Berkeley databases, such as:
/local/notesdata
Normally, requests for these URLs should only originate from a trusted network such as your management computers, not from the Internet. (Exceptions include hosting providers, whose clients around the globe configure their own web applications.) Therefore these requests are a good candidate for URL access control rules.
Many signatures exist for popular web servers and applications such as Apache, nginx IIS, Tomcat, and Subversion. Known suspicious request URLs can be updated. See Connecting to FortiGuard services.
To access this part of the web UI, your administrator’s account access profile must have Read and Write permission to items in the Server Policy Configuration category. For details, see Permissions.

To augment FortiWeb’s predefined list of suspicious request URLs, you can configure your own.
1. Go to Auto Learn > Custom Pattern > Suspicious URL and select Suspicious URL Rule tab.
To access this part of the web UI, your administrator’s account access profile must have Read and Write permission to items in the Server Policy Configuration category. For details, see Permissions.
2. Click Create New.
A dialog appears.
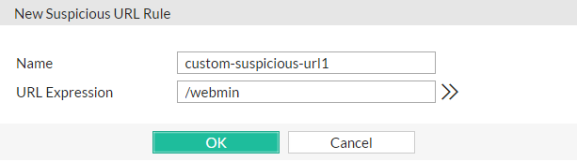
3. In Name, type a unique name that can be referenced by other parts of the configuration. Do not use spaces or special characters. The maximum length is 35 characters.
4. In URL Expression, enter a regular expression that defines this suspicious URL, such as ^/my_admin_panel.jsp.
To test the regular expression against sample text, click the >> (test) icon. This opens the Regular Expression Validator window where you can fine-tune the expression (see Regular expression syntax and Cookbook regular expressions).
5. Click OK.
6. Group custom suspicious URL patterns (see Grouping custom suspicious request URLs).
7. Group custom and predefined suspicious URL groups together (see Grouping all suspicious request URLs).
8. Select the supergroup when configuring an auto-learning profile (see Configuring an auto-learning profile).
Before you can use them, you must first group custom and predefined suspicious URLs.
1. Before you can create a custom suspicious URL rule, you must first define one or more custom suspicious URLs (see Configuring custom suspicious request URLs).
2. Go to Auto Learn > Custom Pattern > Suspicious URLand select Suspicious URL Policy tab.
To access this part of the web UI, your administrator’s account access profile must have Read and Write permission to items in the Server Policy Configuration category. For details, see Permissions.
3. Click Create New.
A dialog appears.
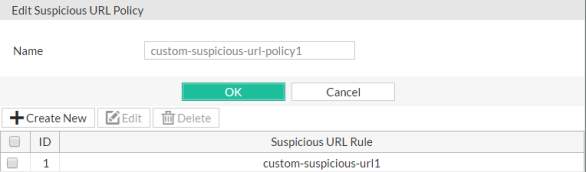
4. In Name, type a unique name that can be referenced by other parts of the configuration. Do not use spaces or special characters. The maximum length is 35 characters.
5. Click OK.
6. Click Create New to add an entry to the set.
A dialog appears.
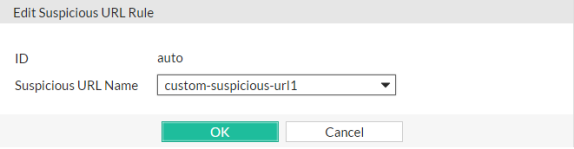
7. From Suspicious URL Name, select the name of a custom suspicious URL rule.
8. Click OK.
9. Repeat the previous steps for each custom suspicious URL rule you want added to the policy.
10. Group custom and predefined suspicious URL groups together (see Grouping all suspicious request URLs).
11. Select the supergroup when configuring an auto-learning profile (see Configuring an auto-learning profile).
Auto Learn > Predefined Pattern > Suspicious URL groups both custom and predefined suspicious URLs together so that they can be selected in an auto-learning profile.
1. Before grouping all suspicious URL patterns, you must first group any custom suspicious URL groups that you want to include. For details, see Grouping custom suspicious request URLs.
2. Go to Auto Learn > Predefined Pattern > Suspicious URL.
To access this part of the web UI, your administrator's account access profile must have Read and Write permission to items in the Server Policy Configuration category. For details, see Permissions.
3. Click Create New.
Alternatively, to clone an existing pattern as the basis for a new group, mark the check box next to it, then click the Clone icon.
A dialog appears.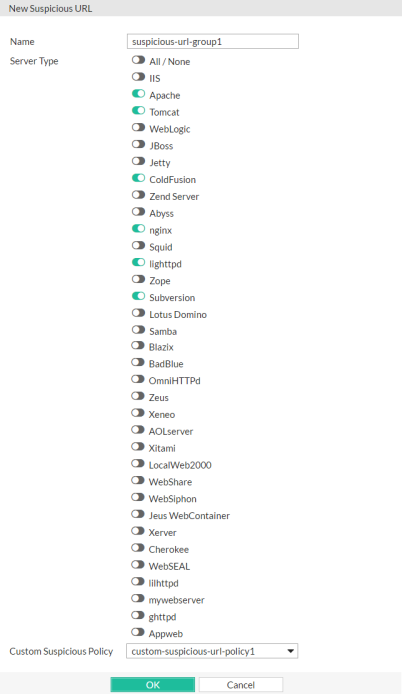
4. In Name, type a unique name that can be referenced by other parts of the configuration. Do not use spaces or special characters. The maximum length is 35 characters.
5. In Server Type, enable one or more of the predefined, web server-specific suspicious URL sets that you want to detect.
To view detailed descriptions of the types of patterns that each suspicious URL type will detect, see Predefined suspicious request URLs.
|
|
If you know that your network’ does not rely on one or more of the listed web server types, disable scans for suspicious access to their administrative URLs in order to improve performance. |
6. From the Custom Suspicious Policy drop-down list, select a group of custom suspicious URLs, that you have configured, if any.
7. Click OK.
8. To use a suspicious URL pattern, select it when configuring an auto-learning profile (see Configuring an auto-learning profile).