HTTP response security headers are a set of standard HTTP response headers proposed to prevent or mitigate known XSS, clickjacking, and MIME sniffing security vulnerabilities. These response headers define security policies to client browsers so that the browsers avoid exposure to known vulnerabilities when handling requests.
When FortiWeb's HTTP Security Headers feature is enabled, headers with specified values are inserted into HTTP responses coming from the backend web servers. This is a quick and simple solution to address the security vulnerabilities on your web site without code and configuration changes. The following includes three different security headers that FortiWeb can insert into resposnes:
| Security headers | Descriptions |
|---|---|
| X-Frame-Options |
This header prevents browsers from Clickjacking attacks by providing appropriate restrictions on displaying pages in frames. The X-Frame-Options header can be implemented with one of the following options:
|
| X-Content-Type-Options |
This header prevents browsers from MIME content-sniffing attacks by disabling the browser's MIME sniffing function. The X-Content-Type-Options header can be implemented with one option:
|
| X-XSS-Protection |
This header enables a browser's built-in Cross-site scripting (XSS) protection. The X-XSS-Protection header can be implemented with one of the following options:
|
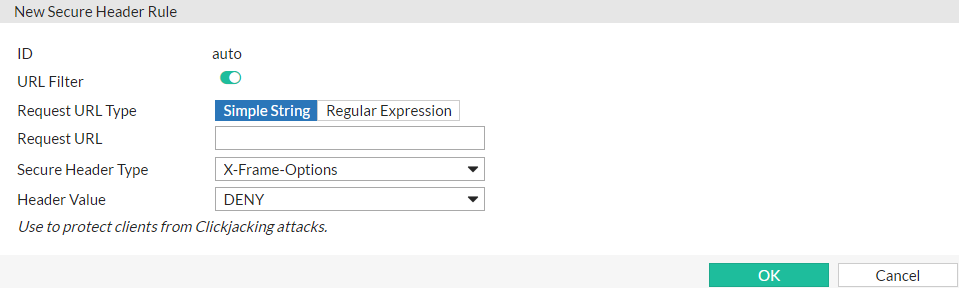
1. Go to Web Protection > Advanced Protection > HTTP Header Security and select an existing policy or create a new one. If creating a new policy, the maximum length of the name is 63 characters; special characters are prohibited.
2. If you created a new policy, click OK to save it. If editing an existing policy, select it and click Edit.
3. Select an existing rule to edit or create a new one in Secure Header Table.
4. Configure the following settings:

| Fields | Descriptions |
|---|---|
| URL Filter |
Click to enable/disable URL filter.
|
| Request URL Type |
Select Simple String to match the URL of requests with a literal URL specified in Request URL. Select Regular Expression to match the URL of requests with a regular expression specified in Request URL. Note: this is available only when URL Filter is enabled. |
| Request URL |
Specify the URL used to match requests so that security headers can be applied to responses of the matched requests. if Simple String is selected in Request URL Type, enter a literal URL. If Regular Expression is selected, enter a regular expression. After filling in the field with a regular expression, it is possible to to fine-tune the expression in a Regular Expression Validator by clicking the >> button on the side. For details, see Regular expression syntax. Note: this is available only when URL Filter is enabled. |
| Secure Header Type |
Select the security header to be inserted into the responses.
For details, see FortiWeb security headers. |
| Header Value |
Select the value for the selected security header. If X-Frame-Options is selected, the options will be:
If X-Content-Type-Options is selected, the option will be:
If X-XSS-Protection is selected, the options will be:
For details, see FortiWeb security headers. |
| Allowed From URL |
It will require you to specify a URI (Uniform Resource Identifier) if header X-Frame-Options and the option ALLOW-FROM are selected. For details, see FortiWeb security headers. |
5. Click OK to save the configuration.
6. To use this HTTP Header Security policy in a protection profile, go to Policy > Web Protection Profile and configure an inline protection profile with the HTTP Header Security policy. For details, see Configuring a protection profile for inline topologies.